Report from SANS '98 - SunWorld (original) (raw)
Click on our Sponsors to help Support SunWorld
![]()
Abstract
Didn't have time to hit the hottest network security conference of the season? Have no fear, Peter Galvin was there. This month he reports on the SANS conference held in Monterey, CA recently. Find out what went on at the best sessions and get Peter's take on the all-important trinket-disbursement situation.
Also this month: Reader tips on setting up a padded cell, bugs, break-ins, and the Stalker's Home Page. (2,600 words)
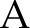 s long-time readers already know, I'm a fan of both the SANS (System Administration Networking and Security) conference and its sister show, the Network Security conference. I had high expectations going into SANS, but was overwhelmed by the quantity of quality, interesting talks available. I counted no fewer than 21 talks I wanted to attend, and most of the ones I did manage to make were terrific.
s long-time readers already know, I'm a fan of both the SANS (System Administration Networking and Security) conference and its sister show, the Network Security conference. I had high expectations going into SANS, but was overwhelmed by the quantity of quality, interesting talks available. I counted no fewer than 21 talks I wanted to attend, and most of the ones I did manage to make were terrific.
There was too much going on at the conference to report on everything (and Monterey, CA, where the conference was held, holds its own interesting diversions, including a well-named local microbrew called Peter B's), so I'll confine myself to reporting on the interesting security-related talks I attended.
If you missed the conference, the good news is that almost all of the talks are on a proceedings CD. You can get this from the SANS Web site (see Resources below). Printed proceedings, course materials, and other goodies are also available. However, you may find these offerings to be a poor substitute for attending a conference. Most of the entries are just copies of the slides that were presented at the talk (I'm as guilty of this as the other speakers). These handouts can serve as a good reminder of what was said, or a good place to scribble notes, but nothing beats attending the talk yourself. Hopefully, this column will serve as the next best thing.
Turning off sendmail forever
One of the highlights was the talk by Wietse Venema about the work he is doing as a visiting fellow at IBM's T. J Watson Research Center. Wietse is well-known as the author of one of the most useful, and well-used free security tools: tcp-wrappers. He also co-authored the network analysis tool, Satan. Wietse says he's decided that sendmail can never be made secure. Rather, he thinks it should be replaced by a program that can be secure. The fundamental problem with sendmail is that it must be setuid-root. Wietse has designed a mail delivery agent that doesn't have that weakness. The mailer, which he plans to use as an example in a forthcoming book with Dan Farmer, has several goals, including:
- Wide deployment: He's giving it away
- Compatibility with sendmail
- Performance: It should be faster than the competition
- Security: There should be no root shells for random strangers
- Flexibility: C is not an acceptable scripting language
- Reliability: It should behave rationally under stress
So far, so good. Of course there are challenges in implementing such a package, including a lot of broken (PC) software that doesn't correctly speak network protocols, concurrent mail database access, mail address parsing and routing, and queue management. Wietse also wants to include spam/relay control. The basic architecture dictates that the mail system server run as a user mail system. This component receives mail from remote and local senders and stores it in a mail queue. Then a setuid-root component delivers mail from the mail queue to local mailboxes or remote systems, as appropriate. In this way, there is no user interaction with the setuid-root component. This architecture also solves several other long-standing security problems with sendmail, such as /tmp race conditions, remote data in shell variables, and fixed-length string buffers.
In terms of compatibility, the vmailer package works with /etc/aliases, NIS aliases, and NetInfo aliases, /var/spool/mail/user, forward files, and file and pipe delivery. There is no sendmail.cf however. The performance is good, but Wietse wants more. He's done some performance testing and the bottleneck is -- and you could have guessed this -- file creation performance. Unix file creation is done synchronously, so every incoming mail message causes a physical disk wait while its inode is allocated and updated. Current performance is 5.3 messages per second being received and 75 deliveries per second. Wietse is working on solving this problem as well as adding new features, including more configuration options and a scripting language. Currently, the code is in public beta release, and it has been used in place of sendmail at several locales. It's available for most common versions of Unix. No, it won't run on Windows.
Short takes
I attended several interesting short but in-depth courses, including:
- DNS and sendmail in a firewalled environment by Hal Pomeranz. Hal discussed the details of DNS service and sendmail mail exchange in the presence of a firewall. The hard part is making sure that the facility protected by the firewall is still secure after those services are allowed. Given the variety of sites and the needs of those sites, he described several possible architectures, from "most paranoid" to least. Generally, the solutions include a DMZ with bastion hosts providing the services. "Split-horizon" DNS -- wherein different DNS information is provided to the outside and inside worlds -- is also part of most solutions.
- Firewall architectures and product selection by Char Sample. Char talked about firewall architectures, selection methods, and a little about specific products. Her main point bears repeating: Let policy drive the decisions on what architecture to implement and which products to use.
- Network-based denial of service attacks by Craig Huegen of Cisco. Craig provided a nice overview of all current, common attacks: who launches them, why they do it, and what can be done to combat them.
- Virtual private networks in the real world by Tina Bird of Secure Network Systems. Bird gave a nice overview of the issues surrounding VPN implementation and included an example of a site using VPNs. She discussed the pros and cons of VPNs, as well as some challenges in implementing them.
- DNS security: Secure naming & key distribution by Donald EastLake III from Cybercash. This course provided details on current and forthcoming DNS security features, including public key cryptography and details of the DNSSEC beta release. These changes should allow for secure management of domains as well as digital signatures to indicate that a domain's information is valid.
Talks
I also attended several interesting talks about security and systems management:
- Big Brother -- Monitoring systems and networks without SNMP, by Sean MacGuire of The MacLawran Group, highlighted one of the hottest free tools available for monitoring Unix machines. Although not strictly a security tool, it's worth including in this conference report due to its value in monitoring systems, both in general and for security. One of the major selling points of Big Brother, as it's author, Sean, pointed out, is its simplicity and ease of installation. Sean acknowledged that in the time the audience spent in the talk, they could have downloaded, compiled, and installed Big Brother on their machines. Although Big Brother is retro -- written in C with some shell scripts, it still has value as a system administration tool. It's designed to automate the tasks that are dull and repetitive in system monitoring. Judging by the number of users of the package, it seems to have hit the mark. Big Brother is obviously simpler than BMC patrol, HP OpenView, and Sun's SunNet Manager, but not all sites need that complexity.
- Experiences learned securing a Web server, by David Kensiski of Deer Run Associates, described the work he did at Cisco to secure its Cisco Connection Online Web site. Dave described the security precautions taken, right down to the application level. A couple of commercial tools were used, and it wasn't clear why Cisco didn't just use VPN tunnels for some pieces of the security puzzle. However, there was great information to be had on methods and procedures to put into place to assure that system-level security work is not undone by user sloppiness.
- Reviewing your network security by Nik Knoth, SRI Consulting. Nik reviewed three Web sites and talked about the security problems he found therein. The problems were fairly obvious, but worth repeating: One site had a Web server on its internal network (rather than on the DMZ); another had a firewall with one rule -- allow everything in and everything out (!); and the third site allowed the r* commands through the firewall and had a rogue + symbol in the /etc/hosts.equiv file. I'm sure you, dear reader, wouldn't make the same mistakes...but would it really hurt to double check?
- Dealing with your first break-in: Mistakes made, lessons learned by Steven Remsing of Goddard Space Flight Center/NASA. This talk described a break-in, what steps were made to track down the problem, decision points along the way, recovery from the break-in, and the aftermath. Of these, the aftermath was probably the most interesting. Steven described the methods used to convince users and management that increased security was needed, including user education. User education is often overlooked in a site security plan.
Advertisements
Handouts
The SANS organization distributed a couple of useful handouts. One was its annual salary survey. It's not only interesting for its numbers, and their subsequent use both by managers and managees (usually to different ends), but also for the advice it contains. There are stories from people about how they secured themselves larger-than-average raises. There are also tips for managers on how to keep your best technical people.
Another useful handout was the Windows NT security step-by-step guide, labeled as a survival guide for Windows NT security. Written by more than 100 contributors, this 32-page guide has a unique format. Some of the steps are obvious: avoid using shared accounts, protect ports via a firewall, and restrict anonymous logon. Those suggestions bear repeating, however, as intruders continue to take advantage of these common weaknesses. But most of the steps in the guide are valuable -- even more valuable are the "actions" associated with each step. Specific changes, including registry keys and their values, are included with each. This guide should be useful for those dealing with NT security, from the novice to intermediate level.
Trinkets
Unfortunately, there were no standout trinkets at this year's vendor show. There were plenty of T-shirts to go around though. There were also a few "hostility" suites in which vendors tried to hold presentations or discussions while potential customers ate and drank. The welcoming party hosted by SANS and the conference hotel was quite a lot of fun, with model-car racing, pinball, video games, and other games of semi-skill. Quite a few brave souls made fools of themselves riding around a circle on motorized garbage cans (yeah, you had to be there). Generally, the conference was very smoothly run, with plenty to do and very few snafus along the way. If there was one problem, it was not having enough time to explore the areas surrounding Monterey. Maybe next time the talks won't be quite so compelling.
Bugs
Sun has released security bulletin #170 about the rpc.nisd daemon. This RPC daemon is required on all NIS+ servers. Unfortunately, there's a buffer overflow possibility in all OS releases, which could lead to root access via the network. Patches for all recently OS releases are now available.
Sun also released bulletin #171, describing a potential denial-of-service attack in all recent releases of in.ftpd. Again, patches are available.
Break-ins
It's been an unprecedented couple of months on the break-in front. Most recently, three teenage computer hackers claim to have broken into computer systems at India's Bhabha Atomic Research Center (BARC) and say that they are targeting Pakistani computers in a protest against the two nations' recent nuclear weapons tests. Apparently the hackers gained access to six of eight servers in the barc.ernet.in domain, stole copies of e-mail between scientists, and modified the Web server contents. No one seems to know exactly how much sensitive or classified information these kids got their hands on.
Also in the news, was the Rt66 break-in. This ISP was taken down for nearly 36 hours after a root disk was erased on one of its systems. The ISP was a bystander when one of the sites it hosts, Carolyn Meinel's_King of the Hill_ Web site, issued a challenge to "hack this site." Both the Web site and the ISP were attacked. They were subjected to an average of 1,000 hack attacks a day. Almost all were repulsed, but one managed to get root access on one of the ISP's servers and do the damage.
Conferences
If this column whets your appetite for attending security conferences, you should make plans now to attend Network Security '98, in Orlando, FL, from October 24 to 31.
After that, the next major conference is LISA '98, to be held in Boston in December.
Letters
The topic of building padded cells for Web and mail servers elicited quite a lot of reader response. Many asked for help in building the padded cells. Most of these were resolved with judicious use of truss to determine why programs were failing in the padded cell. There were also several good comments and suggestions, not to mention differences of opinion.
Gilles Ciselet from IBM Belgium points out some common variations that may be required at sites with requirements differing from our project. He writes:
Hi Peter,
I was really happy to read your column regarding the Web server in the padded cell.
I've designed Web hosting systems and I'm happy to learn I'm not the only one out there using this. What inspired me from the beginning was the "virtual servers technology."
What I disagree with is the sendmail set up: Customers very much like to put a cgi script that sends mail (e.g., Formmail.pl). The approach I have taken is to remove the suid bit from sendmail, and I've granted enough permissions to the queue directory. Of course there's only one customer per cell. I believe the padded cell security is good as long as you don't have suid root programs in it, since root can escape a chroot.
One last thing: As customers need both FTP and telnet I needed to put quite a lot in /usr (shells, terminfo, etc.), so I made a new filesystem with all the code and mounted it as read-only over the /new/root/usr directory.
The basic principle is to allow only what is necessary. If sendmail is necessary, include it, but only with minimum privileges. Certainly adding complexity can result in security problems, but as Gilles points out, the end result is almost certain to be more secure than the non-chrooted alternative. The read-only idea is a good one. Certainly not fool-proof, as a mount can be re-mounted read-write, but at least it's another layer in the security onion.
The Bookshelf
The _Stalker's Home Page_reminds us that the Web is like a nuclear bomb -- it can be used for good or evil. The page has links to many sources of information, which can be used together to gather quite a lot of information about an individual. Some of the sources cost money, but you can also find many interesting things for free. On the page, you can look up all sorts of personal information: addresses, social security numbers, and other personal details. Is this a cautionary tale of our diminishing privacy? Or just someone spreading a lot of FUD? You decide.
Next month
The column about secure programming apparently struck a nerve. It seems that few companies are taking security into account when creating programs, which results in potential security problems. Next month, I'll present a secure-programming FAQ that includes a succinct list of dos, don'ts, whys, and why-nots. Hopefully, that will help the industry move forward and start producing code that's solid and secure -- not just more hacker bait.![]()
Click on our Sponsors to help Support SunWorld
Resources
- Big Brother
http://maclawran.ca/sean/bb-dnld/index.html - Network Security '98
http://www.sans.org/NS98/main.htm - SANS
http://www.sans.org - The Stalker's Home Page
http://www.glr.com/stalk.html - Last month's Security column
http://www.sunworld.com/swol-06-1998/swol-06-security.html - Full listing of Security columns in SunWorld
http://www.sunworld.com/common/swol-backissues-columns.html#security - Related network security stories in SunWorld's Site Index
http://www.sunworld.com/common/swol-siteindex.html#netsec - Peter Galvin's Solaris Security FAQ
http://www.sunworld.com/common/security-faq.html
About the author![]() Peter Galvin is chief technologist for Corporate Technologies Inc., a systems integrator and VAR. He is also adjunct system planner for the Computer Science Department at Brown University, and has been program chair for the past four SUG/SunWorld conferences. As a consultant and trainer, he has given talks and tutorials worldwide on the topics of system administration and security. He has written articles for Byte and Advanced Systems (SunWorld) magazines, and the Superuser newsletter. Peter is co-author of the best-selling Operating Systems Concepts textbook. Reach Peter at peter.galvin@sunworld.com.
Peter Galvin is chief technologist for Corporate Technologies Inc., a systems integrator and VAR. He is also adjunct system planner for the Computer Science Department at Brown University, and has been program chair for the past four SUG/SunWorld conferences. As a consultant and trainer, he has given talks and tutorials worldwide on the topics of system administration and security. He has written articles for Byte and Advanced Systems (SunWorld) magazines, and the Superuser newsletter. Peter is co-author of the best-selling Operating Systems Concepts textbook. Reach Peter at peter.galvin@sunworld.com.
![]()
[![]() ](/sunworldonline/common/swol-copyright98.html)
](/sunworldonline/common/swol-copyright98.html)
If you have technical problems with this magazine, contact webmaster@sunworld.com
URL: http://www.sunworld.com/swol-07-1998/swol-07-security.html
Last modified: