Standard Cryptographic Algorithm Naming (original) (raw)
Symmetric Ciphers
Also see the notes for block cipher modes andKeyGenerators.
Key scheduling
Ciphers that have different key schedules, but are otherwise identical are given different names (for example,SAFER-K andSAFER-SK). Sometimes it is useful to bypass the normal key scheduling process, and specify the subkeys (which should be random and independent) directly in the input key. The name of such a cipher is derived by adding "-Direct" to the standard name (except that if part of the name already specifies the key schedule, that part is dropped). For example, "DES-Direct" and "SAFER-Direct" refer to DES and SAFER respectively with independent subkeys. This convention can also be used for experimental ciphers that have no defined key schedule. [A previous version of SCAN specified "-ISK" instead of "-Direct". This is a backward-incompatible change, although an alias has been added for "Blowfish-ISK".]
If the subkeys are not in fact random and independent (to a close-enough approximation), the cipher may become vulnerable to related-key attacks, and therefore particular care is needed from the application designer in choosing how to generate subkeys.
Subkeys are encoded in the order in which they are used for encryption (or if this is ambiguous, the order in which they are presented or numbered in the original document specifying the cipher). Where applicable, they have the same byte order as is used in the rest of the cipher. However, in some cases these conventions may still not be sufficient to decide how to encode the subkeys; if you wish to use a "-Direct" algorithm where the subkey encoding is not clear, ask for a comment to be added to the algorithm definition.
Designer:
Published:
1994
Alias:
"ThreeWay" (use for identifiers)
References:
- [_Def, An_] Joan Daemen,
"Cipher and Hash Function Design, Strategies based on linear and differential cryptanalysis,"
Ph.D. Thesis, Katholieke Universiteit Leuven, March 1995. http://www.esat.kuleuven.ac.be/~cosicart/ps/JD-9500/
(in particular seechapter 7, "block cipher design"). - [_Def, An_] J. Daemen, R. Govaerts, J. Vandewalle,
"A New Approach to Block Cipher Design,"
Fast Software Encryption, Cambridge Security Workshop Proceedings, Volume 809 of Lecture Notes in Computer Science (Ross Anderson, ed.), pp. 18-32. Springer-Verlag, 1994. - [_Inf_] Bruce Schneier,
"Section 14.5 3-Way,"
Applied Cryptography, Second Edition, John Wiley & Sons, 1996. - [_An_] John Kelsey, Bruce Schneier, David Wagner,
"Key-Schedule Cryptanalysis of 3-WAY, IDEA, G-DES, RC4, SAFER, and Triple-DES".
http://www.counterpane.com/key_schedule.html - [_An_] John Kelsey, Bruce Schneier, David Wagner,
"Related-Key Cryptanalysis of 3-WAY, Biham-DES, CAST, DES-X, NewDES, RC2, and TEA",
ICICS '97 Proceedings, Springer-Verlag, November 1997.
http://www.counterpane.com/related-key_cryptanalysis.html - [_Test_] Wei Dai,
Crypto++ 3.0, file 3wayval.dat
http://www.eskimo.com/~weidai/cryptlib.html
Key length:
96 bits.
Block size:
12 bytes.
Comment:
The byte ordering convention is as follows: within each 12-byte block, the 32-bit words are represented in the same order as they are written in chapter 7 of Joan Daemen's thesis. Within each 32-bit word, the bytes are in big-endian order. This is consistent with the four test vectors in Crypto++ (note that the same four test vectors are included on page 659 ofApplied Cryptography, 2nd edition, with the words written in the opposite order).
For reference, the fourth test vector in this set is:
key = plaintext = <4059C76E83AE9DC4AD21ECF7> ciphertext = <478EA8716B13F17C15B155ED>
Security comment:
3-Way is vulnerable to related-key attacks, and therefore it should only be used with keys that are generated by a strong RNG, or by a source of bits that are sufficiently uncorrelated (such as the output of a hash function).
Designers:
Alias:
"OpenPGP.Cipher.7"
Object Identifiers:
- 2.16.840.1.101.3.4.1.1 for AES128/ECB/NoPadding
- 2.16.840.1.101.3.4.1.2 for AES128/CBC/PKCSPadding
- 2.16.840.1.101.3.4.1.3 for AES128/CFB
- 2.16.840.1.101.3.4.1.4 for AES128/OFB
Description:
AES128 is defined as Rijndael with a 128-bit block size and 10 rounds.
References:
- [see references for Rijndael]
- [_Inf_] NIST,
AES Home Page,
http://www.nist.gov/aes/ - [_Inf_] AES Round 1 Information,
http://csrc.nist.gov/encryption/aes/round1/round1.htm - [_Inf_] AES Round 2 Information,
http://csrc.nist.gov/encryption/aes/round2/round2.htm - [_Inf_] The CAESAR - Candidate AES for Analysis and Reviews project,
http://www.dice.ucl.ac.be/crypto/CAESAR/caesar.html - [_Inf_] Lars Knudsen, Vincent Rijmen,
The Block Cipher Lounge - AES,
http://www.ii.uib.no/~larsr/aes.html - [_Inf_] John Savard,
Towards the 128-bit Era - AES Candidates,
http://fn2.freenet.edmonton.ab.ca/~jsavard/crypto/co0408.htm - [_An_] Eli Biham,
"A Note on Comparing the AES Candidates,"
Presented at the 2nd AES Conference.
http://csrc.nist.gov/encryption/aes/round1/conf2/papers/biham2.pdf - [_An_] Olivier Baudron, Henri Gilbert, Louis Granboulan, Helena Handschuh, Antoine Joux, Phong Nguyen, Fabrice Noilhan, David Pointcheval, Thomas Pornin, Guillaume Poupard, Jacques Stern, Serge Vaudenay,
"Report on the AES Candidates,"
Presented at the 2nd AES Conference.
http://csrc.nist.gov/encryption/aes/round1/conf2/papers/baudron1.pdf - [_An_] G. Carter, E. Dawson, L. Nielsen,
"Key Schedule Classification of the AES Candidates,"
Presented at the 2nd AES Conference.
http://csrc.nist.gov/encryption/aes/round1/conf2/papers/carter.pdf - [_An_] B. Preneel, A. Bosselaers, V. Rijmen, B. Van Rompay, L. Granboulan, J. Stern, S. Murphy, M. Dichtl, P. Serf, E. Biham, O. Dunkelman, V. Furman, F. Koeune, G. Piret, J-J. Quisquater, L. Knudsen, H. Raddum,
"Comments by the NESSIE Project on the AES Finalists,"
Submitted to NIST as an AES comment, May 2000.
http://csrc.nist.gov/encryption/aes/round2/comments/20000524-bpreneel.pdf - [_An_] Thomas S. Messerges,
"Securing the AES Finalists Against Power Analysis Attacks,"
Presented at Fast Software Encryption 2000, New York.
Key length:
128 bits.
Block size:
16 bytes.
Designers:
Alias:
"OpenPGP.Cipher.8"
Object Identifiers:
- 2.16.840.1.101.3.4.1.21 for AES192/ECB/NoPadding
- 2.16.840.1.101.3.4.1.22 for AES192/CBC/PKCSPadding
- 2.16.840.1.101.3.4.1.23 for AES192/CFB
- 2.16.840.1.101.3.4.1.24 for AES192/OFB
Description:
AES192 is defined as Rijndael with a 128-bit block size and 12 rounds.
References:
[see references for AES128 andRijndael]
Key length:
192 bits.
Block size:
16 bytes.
Designers:
Alias:
"OpenPGP.Cipher.9"
Object Identifiers:
- 2.16.840.1.101.3.4.1.41 for AES256/ECB/NoPadding
- 2.16.840.1.101.3.4.1.42 for AES256/CBC/PKCSPadding
- 2.16.840.1.101.3.4.1.43 for AES256/CFB
- 2.16.840.1.101.3.4.1.44 for AES256/OFB
Description:
AES256 is defined as Rijndael with a 128-bit block size and 14 rounds.
References:
[see references for AES128 andRijndael]
Key length:
256 bits.
Block size:
16 bytes.
Designers:
Paulo Barreto,Vincent Rijmen
Published:
November 2000
References:
- [_Def, An_] Paulo Barreto, Vincent Rijmen,
The Anubis Block Cipher,
Presented at the First Open NESSIE Workshop, November 2000.
https://www.cosic.esat.kuleuven.ac.be/nessie/workshop/submissions/anubis.zip - [_Inf, Test_] Paulo Barreto, Vincent Rijmen,
The Anubis Page,
http://www.esat.kuleuven.ac.be/~rijmen/anubis/ - [_Test_] Paulo Barreto, Vincent Rijmen,
Anubis Test Values,
https://www.cosic.esat.kuleuven.ac.be/nessie/workshop/submissions/anubis.zip
Key length:
Minimum 128, maximum 320, multiple of 32 bits; default 128 bits.
Block size:
16 bytes.
Designer:
Published:
1994
Alias:
"OpenPGP.Cipher.4"
References:
- [_Def_] Bruce Schneier,
"Description of a New Variable-Length Key, 64-Bit Cipher (Blowfish),"
Fast Software Encryption, Cambridge Security Workshop Proceedings, pp. 191-204. Springer-Verlag, 1994.
http://www.counterpane.com/bfsverlag.html - [_Inf, Impl_] Bruce Schneier,
The Blowfish Encryption Algorithm page,
http://www.counterpane.com/blowfish.html - [_Inf_] Bruce Schneier,
"Blowfish -- One Year Later,"
Dr. Dobb's Journal, September 1995.
http://www.counterpane.com/bfdobsoyl.html - [_Inf_] Bruce Schneier,
"Section 14.3 Blowfish,"
Applied Cryptography, Second Edition, John Wiley & Sons, 1996.
(Note: the C source in the appendix contains abug; this bug is not present in Eric Young's C reference implementation.) - [_An_] Serge Vaudenay,
"On the weak keys of Blowfish,"
Fast Software Encryption, Third International Workshop, Volume 1008 of Lecture Notes in Computer Science (B. Preneel, ed.), pp. 286-297. Springer-Verlag, 1995. - [_Test_] Eric Young,
Blowfish test vectors,
http://www.counterpane.com/vectors.txt (also in C syntax)
Key length:
Minimum 32, maximum 448, multiple of 8 bits; default 128 bits.
Block size:
8 bytes.
Security comment:
The weak keys described in Vaudenay's paper do not appear to be significant for full (16-round) Blowfish.
Variant:
"Blowfish-Direct" or "Blowfish-ISK" - the subkeys are specified (using the notation of Applied Cryptography) as P1..18 first, followed by S1, 0..255, S2, 0..255, S3, 0..255, and S4, 0..255. Each entry is represented as 4 bytes in big-endian order.
Weak keys may be avoided by ensuring that no S-box has duplicate entries (i.e. that there does not exist i, j, k where j != k such that Si, j = Si, k).
Designers:
Johan Håstad, Mats Näslund
Published:
October 2000
Description:
BMGL is an alias for "Rijndael-256/KFB(40)"; that is, Rijndael with a 256-bit block size, used in KFB mode, with 40 bits of keystream taken for each application of Rijndael. See the description of KFB mode for further detail.
References:
- [_Def, An_] Johan Håstad, Mats Näslund,
BMGL: Synchronous Key-stream Generator with Provable Security,
https://www.cosic.esat.kuleuven.ac.be/nessie/workshop/submissions/bmgl.zip - [_Test_] Johan Håstad, Mats Näslund,
BMGL Test Values,
https://www.cosic.esat.kuleuven.ac.be/nessie/workshop/submissions/bmgl.zip
Key length:
Minimum 128, maximum 320, multiple of 32 bits; default 128 bits.
Security comment:
The security bounds proven for BMGL in Corollary 13 of Håstad and Näslund's paper, hold provided that less than 230 bits (128 MBytes) of output are used. The "provable security" referred to in the paper is in the sense of a proven reduction from predicting the keystream generator, to breaking Rijndael-256 as a one-way function.
Designers:
Carlisle Adams,Stafford Tavares
Published:
1997
Aliases:
"CAST5", "OpenPGP.Cipher.3"
References:
- [_Def, Test_] Carlisle Adams,
"The CAST-128 Encryption Algorithm,"
RFC 2144, May 1997. - [_Inf, An_] CAST Encryption Algorithm Related Publications,
http://adonis.ee.queensu.ca:8000/cast/ - [_Inf_] Carlisle Adams,
"Constructing Symmetric Ciphers Using the CAST Design Procedure,"
Selected Areas in Cryptography (E. Kranakis and P. van Oorschot, ed.), pp. 71-104. Kluwer Academic Publishers, 1997, and
Designs, Codes, and Cryptography, Vol. 12, No. 3, pp. 283-316, 1997.
http://www.entrust.com/resourcecenter/pdf/cast.pdf
Also "CAST Design Procedure Addendum,"
http://www.entrust.com/downloads/castadd.pdf - [_Patent_] Carlisle Adams,
"Symmetric cryptographic system for data encryption,"
U.S. Patent 5,511,123, filed August 4 1994, issued April 23 1996.
Also see:
Canadian Patent Application 2,134,410.
Japanese Patent Application 6-295746.
U.S. Patent Application 08/761,763.
Canadian Patent Application 2,164,768.
PCT Patent Application CA96/00782.
U.S. Patent Application 08/895,875.
Key length:
Minimum 40, maximum 128, multiple of 8 bits; default 128 bits.
Block size:
8 bytes.
Comment:
Strictly speaking the alias "CAST5" only applies to CAST-128 with a key size of 80 or 128 bits. Implementations MAY enforce this.
Patent status:
The design procedure that was used to obtain the CAST S-boxes is patented by Entrust Technologies, Inc.. However, quoting from RFC 2144,
The CAST-128 cipher described in this document is available worldwide on a royalty-free basis for commercial and non-commercial uses.
Designer:
Carlisle Adams, Howard Heys,Stafford Tavares, Michael Wiener
Published:
June 1998
Alias:
"CAST6"
References:
- [_Def, An_] Carlisle Adams,
The CAST-256 Encryption Algorithm,
http://www.entrust.com/resources/pdf/cast-256.pdf - [_Def, Test_] Carlisle Adams, Jeff Gilchrist,
"The CAST-256 Encryption Algorithm,"
RFC 2612, June 1999. - [_Inf_] Carlisle Adams,
"Constructing Symmetric Ciphers Using the CAST Design Procedure,"
Selected Areas in Cryptography (E. Kranakis and P. van Oorschot, ed.), pp. 71-104. Kluwer Academic Publishers, 1997, and
Designs, Codes, and Cryptography, Vol. 12, No. 3, pp. 283-316, 1997.
http://www.entrust.com/resources/pdf/cast.pdf
Also "CAST Design Procedure Addendum,"
http://www.entrust.com/resources/pdf/castadd.pdf
(This does not describe CAST-256, but is relevant to its design.) - [_An_] C. Adams, H. Heys, S. Tavares, M. Wiener,
"An Analysis of the CAST-256 Cipher,"
Proceedings of IEEE Canadian Conference on Electrical and Computer Engineering, 1999.
http://www.engr.mun.ca/~howard/PAPERS/cast256.ps - [_Patent_] Carlisle Adams,
"Symmetric cryptographic system for data encryption,"
U.S. Patent 5,511,123, filed August 4 1994, issued April 23 1996.
Also see:
Canadian Patent Application 2,134,410.
Japanese Patent Application 6-295746.
U.S. Patent Application 08/761,763.
Canadian Patent Application 2,164,768.
PCT Patent Application CA96/00782.
U.S. Patent Application 08/895,875. - [_Test_] NIST,
CAST-256 Test Values,
http://www-08.nist.gov/encryption/aes/round1/testvals/cast-256-vals.zip
Key length:
Minimum 128, maximum 256, multiple of 32 bits; default 128 bits.
Block size:
16 bytes.
Patent status:
The design procedure that was used to obtain the CAST S-boxes is patented by Entrust Technologies, Inc.. However, quoting from RFC 2612,
The CAST-256 cipher described in this document is available worldwide on a royalty-free and licence-free basis for commercial and non-commercial uses.
Designer:
Published:
1998
Alias:
"CRYPTONv05" (use for identifiers)
Description:
This is the version of CRYPTON originally submitted to NIST as an AES candidate.
References:
- [_Def, An_] Chae Hoon Lim, Hyo Sun Hwang,
CRYPTON: A New 128-bit Block Cipher - Specification and Analysis (Version 0.5),
http://crypt.future.co.kr/~chlim/pub/cryptonv05.ps (PDF version). - [_Inf, Test_] The CRYPTON: A new 128-bit block cipher page.
http://crypt.future.co.kr/~chlim/crypton.html - [_An_] D'Halluin, Bijnens, Rijmen, Preneel,
"Attack on six rounds of CRYPTON,"
Presented at Fast Software Encryption '99, Rome. - [_Test_] NIST,
CRYPTON v0.5 Test Values,
http://www-08.nist.gov/encryption/aes/round1/testvals/crypton-vals.zip
Comment:
"CRYPTON: A New 128-bit Block Cipher - Specification and Analysis" contains an error in the description of the byte permutation phi: on the right hand side of figure 4, b33 should be b03.
Key length:
Minimum 64, maximum 256, multiple of 32 bits; default 128 bits.
Block size:
16 bytes.
Security comments:
- [[need reference to key schedule attacks]]
- CRYPTON-0.5 has been superceded by CRYPTON-1.0.
Designer:
Published:
December 1998
Alias:
"CRYPTONv10" (use for identifiers)
Description:
This is version 1.0 of CRYPTON (the current version, at time of writing).
References:
- [_Def, An_] Chae Hoon Lim, Hyo Sun Hwang,
CRYPTON: A New 128-bit Block Cipher - Specification and Analysis (Version 1.0),
http://crypt.future.co.kr/~chlim/pub/cryptonv10.ps. - [_Inf, Test_] The CRYPTON: A new 128-bit block cipher page.
http://crypt.future.co.kr/~chlim/crypton.html - [_An_] Marine Minier, Henri Gilbert,
"Stochastic Cryptanalysis of Crypton,"
Presented at Fast Software Encryption 2000, New York.
Key length:
Minimum 0, maximum 256, multiple of 8 bits; default 128 bits.
(Note that this is different from CRYPTON-0.5.)
Block size:
16 bytes.
Designers:
Published:
1998
References:
- [_Def, An, Test, Impl_] Serge Vaudenay, Jacques Stern,
"CS-Cipher,"
Presented at Fast Software Encryption '98, Paris, France. Lecture Notes in Computer Science No. 1372, pp. 189-205, Springer-Verlag, 1998.
http://lasecwww.epfl.ch/query.msql?ref=SV98 - [_An_] Serge Vaudenay,
"On the Security of CS-Cipher,"
Presented at Fast Software Encryption '99, Rome. To appear in Lecture Notes in Computer Science, Springer-Verlag.
http://lasecwww.epfl.ch/query.msql?ref=Vau99b - [_An_] Bart van Rompey, Vincent Rijmen, Jorge Nakahara Jr.,
"A First Report on CS-Cipher, Hierocrypt, Grand Cru, SAFER++ and SHACAL,"
NESSIE Project public report, March 12, 2001.
https://www.cosic.esat.kuleuven.ac.be/nessie/reports/kulwp3-006-1.pdf
Key length:
Minimum 0, maximum 128, multiple of 8 bits; default 128 bits.
Block size:
8 bytes.
Patent status:
CS-Cipher may be subject to patents by the Compagnie des Signaux.
Designer:
Published:
May 1998
References:
- [_Def, An_] Lars Knudsen,
DEAL: A 128-bit Block Cipher, February 1998 (revised May 15, 1998).
http://www.ii.uib.no/~larsr/newblock.html
(Note: this paper contains an error; see the comments below.) - [_An_] Stefan Lucks,
On the Security of the 128-Bit Block Cipher DEAL.
http://th.informatik.uni-mannheim.de/m/lucks/papers.html - [_An_] John Kelsey, Bruce Schneier,
"Key-Schedule Cryptanalysis of DEAL,"
Sixth Annual Workshop on Selected Areas in Cryptography,
Springer-Verlag, August 1999, to appear.
http://www.counterpane.com/deal.html - [_Test_] NIST,
DEAL Test Values,
http://www-08.nist.gov/encryption/aes/round1/testvals/deal-vals.zip
Key length:
128, 192 or 256 bits; default 128 bits.
Block size:
16 bytes.
Comment:
The paper "DEAL: A 128-bit Block Cipher" contains an error in the description of key scheduling: the three occurrences of "<4>" should be replaced by "<3>", and the two occurrences of "<8>" should be replaced by "<4>". In other words, the constants to be XOR'd with the input keys are 0x8000000000000000, 0x4000000000000000, 0x2000000000000000 and 0x1000000000000000.
Security comments:
- The paper "On the Security of the 128-Bit Block Cipher DEAL," describes some certificational weaknesses of DEAL with a key size of 192 bits; these attacks are impractical.
- John Kelsey of Counterpane Systems has found some related-key attacks and equivalent keys for DEAL (described in the DEAL AES forum onNIST's web site, and in the paper "Key-Schedule Cryptanalysis of DEAL"). These appear to be impractical when DEAL is used as a cipher (as opposed to a hash function using a construction such as Davies-Meyer).
Designers:
Don Coppersmith, Horst Feistel, Walt Tuchmann,U.S. National Security Agency
Published:
1976
References:
- [_Def_] U.S. National Institute of Standards and Technology,
NIST FIPS PUB 46-2 (supercedes FIPS PUB 46-1), "Data Encryption Standard", U.S. Department of Commerce, December 1993.
http://www.itl.nist.gov/div897/pubs/fip46-2.htm - [Inf, _Test_] U.S. National Institute of Standards and Technology,
NIST FIPS PUB 74, "Guidelines for Implementing and Using the NBS Data Encryption Standard". - [_Inf_] Bruce Schneier,
"Chapter 12 Data Encryption Standard,"
Applied Cryptography, Second Edition, John Wiley & Sons, 1996. - [Inf, _Test_] A. Menezes, P.C. van Oorschot, S.A. Vanstone,
"Section 7.4 DES,"
Handbook of Applied Cryptography, CRC Press, 1997.
http://www.cacr.math.uwaterloo.ca/hac/about/chap7.pdf,.ps - [_An_] Eli Biham, Adi Shamir,
"Differential Cryptanalysis of the Full 16-Round DES,"
CS 708, Proceedings of CRYPTO '92, Volume 740 of Lecture Notes in Computer Science, December 1991.
http://www.cs.technion.ac.il/users/wwwb/cgi-bin/tr-get.cgi/1991/CS/CS0708.ps - [_An_] Eli Biham, Adi Shamir,
"Differential cryptanalysis of DES-like cryptosystems,"
Technical report CS90-16, Weizmann Institute of Science.
Advances in Cryptology - CRYPTO '90 Proceedings and
Journal of Cryptology, Vol. 4, No. 1, pp. 3-72, 1991.
http://www.cs.technion.ac.il/~biham/Reports/Weizmann/cs90-16.ps.gz - [_An_] Eli Biham, Adi Shamir,
Differential Cryptanalysis of the Data Encryption Standard,
Springer-Verlag, 1993. - [_An_] M. Matsui,
"Linear cryptanalysis method for DES cipher,"
Advances in Cryptology - EUROCRYPT '93 Proceedings, Volume 765 of Lecture Notes in Computer Science (T. Helleseth, ed.), pp. 386-397. Springer-Verlag, 1994. - [_An_] M. Matsui,
"The First Experimental Cryptanalysis of the Data Encryption Standard,"
Advances in Cryptology - CRYPTO '94 Proceedings, Volume 839 of Lecture Notes in Computer Science, Springer-Verlag, 1994. - [_An_] M. Matsui,
"On Correlation Between the Order of S-boxes and the Strength of DES,"
Advances in Cryptology - EUROCRYPT '94 Proceedings, Volume 950 of Lecture Notes in Computer Science, Springer-Verlag, 1995. - [_An_] Eli Biham, A. Biryukov,
"An Improvement of Davies' Attack on DES,"
CS 817, EUROCRYPT '94 Proceedings (May 1994), Volume 950 of Lecture Notes in Computer Science (A. De Santis, ed.), Springer Verlag, 1995, and
Journal of Cryptology, Vol. 10, No. 3, pp. 195-206, 1997.
http://www.cs.technion.ac.il/users/wwwb/cgi-bin/tr-get.cgi/1994/CS/CS0817.ps - [_An_] Lars Knudsen,
"New potentially weak keys for DES and LOKI,"
Advances in Cryptology - EUROCRYPT '94 Proceedings, Volume 950 of Lecture Notes in Computer Science (A. De Santis, ed.), pp. 419-424. Springer Verlag, 1995.
ftp://ftp.esat.kuleuven.ac.be/pub/COSIC/knudsen/potential.ps.Z - [_An_] Lars Knudsen, John Erik Mathiassen,
"A Chosen-Plaintext Linear Attack on DES,"
Proceedings of Fast Software Encryption 2000, Volume 1978 of Lecture Notes in Computer Science. Springer-Verlag, 2001.
http://link.springer.de/link/service/series/0558/bibs/1978/19780262.htm
(requires subscription) - [_Test_] U.S. National Institute of Science and Technology,
NIST Special Publication 800-17, pp. 124 et seq.
http://csrc.nist.gov/nistpubs/800-17.pdf
Key length:
64 bits as encoded; 56 bits excluding parity bits.
Block size:
8 bytes.
Comment:
Implementations MUST ignore (i.e. not check) the parity bits of keys. KeyGenerators for DES MUST, however, output keys with correct parity.
Security comment:
The fixed 56-bit effective key length is too short to prevent brute-force attacks.
Designers:
Whitfield Diffie, Martin Hellman, Walt Tuchmann
Published:
1978-79
Aliases:
- "DES-EDE2" (always 2-key)
- "DES-EDE3", "OpenPGP.Cipher.2" (always 3-key)
- "TripleDES", "3DES" (default key length implemented inconsistently by different providers)
References:
- [_Def_] U.S. National Institute of Standards and Technology,
DRAFT FIPS PUB 46-3, "Data Encryption Standard",
U.S. Department of Commerce, 1999.
http://csrc.nist.gov/cryptval/des/fr990115.htm - [_Inf_] Walt Tuchman,
"Hellman Presents No Shortcut Solutions To DES,"
IEEE Spectrum, v. 16, n. 7, July 1979, pp. 40-41. - [_Inf_] U.S. National Institute of Standards and Technology,
NIST FIPS PUB 46-2, "Data Encryption Standard",
U.S. Department of Commerce, December 1993.
http://www.itl.nist.gov/div897/pubs/fip46-2.htm - [_Inf_] Bruce Schneier,
"Chapter 12 Data Encryption Standard," and "Section 15.2 Triple Encryption,"
Applied Cryptography, Second Edition, John Wiley & Sons, 1996. - [_Inf, An_] Ralph C. Merkle,
Secrecy, authentication, and public key systems,
UMI Research Press, Ann Arbor, Michigan, 1979. - [_Inf, An_] Ralph C. Merkle, Martin Hellman,
"On the Security of Multiple Encryption,"
Communications of the ACM, vol. 24 no. 7, 1981, pp. 465-467. - [_An_] Paul van Oorshot, Michael Wiener,
"A Known-Plaintext Attack on Two-Key Triple Encryption,"
Advances in Cryptology - EUROCRYPT '90 Proceedings, Volume 473 of Lecture Notes in Computer Science (I.B. Damgård, ed.), pp. 318-325. Springer-Verlag, 1991. - [_An_] John Kelsey, Bruce Schneier, David Wagner,
"Key-Schedule Cryptanalysis of 3-WAY, IDEA, G-DES, RC4, SAFER, and Triple-DES".
http://www.counterpane.com/key_schedule.html - [_An_] Stefan Lucks,
"Attacking Triple Encryption,"
Fast Software Encryption '98,
Volume 1372 of Lecture Notes in Computer Science (Serge Vaudenay, ed.), Springer-Verlag, 1998.
http://th.informatik.uni-mannheim.de/m/lucks/papers.html - [_An_] Helena Handschuh, Bart Preneel,
"On the security of double and 2-key triple modes of operation."
Fast Software Encryption 6,
Volume 1636 of Lecture Notes in Computer Science (L. Knudsen, ed.), Springer-Verlag, 1999.
http://perso.enst.fr/~handschu/fse6.ps - [_Test_] U.S. National Institute of Standards and Technology,
Modes of Operation Validation System for the Triple Data Encryption Algorithm (TMOVS): Requirements and Procedures,
NIST Special Publication 800-20, April 2000.
http://csrc.nist.gov/publications/nistpubs/800-20/800-20.pdf - [_Test_] U.S. National Institute of Standards and Technology,
Triple DES Test Vectors,
http://csrc.nist.gov/cryptval/des/tripledes-vectors.zip
Key length:
128 or 192 bits, as encoded (112 or 168 bits excluding parity). The default key length depends on the name of the KeyGenerator: 128 bits for DES-EDE2, and 192 bits for DES-EDE3 or OpenPGP.Cipher.2.
The default key length for DESede and the other aliases is implemented inconsistently between different providers, and therefore if an application needs to create a specific length of DESede key in a way that is guaranteed to work across providers, it should explicitly create a SecretKeySpec.
Block size:
8 bytes.
Comments:
- If the key length is 128 bits including parity (i.e. two-key triple DES), the first 8 bytes of the encoding represent the key used for the two outer DES operations, and the second 8 bytes represent the key used for the inner DES operation.
- If the key length is 192 bits including parity (i.e. three-key triple DES), then three independent DES keys are represented, in the order in which they are used for encryption.
- Implementations MUST ignore (i.e. not check) the parity bits of keys. KeyGenerators for DESede MUST, however, output keys with correct parity.
Security comment:
Quoting from the paper "Attacking Triple Encryption" cited above:
[A]bout 2108 steps of computation are sufficient to break three-key triple DES. If one concentrates on the number of single DES operations and assumes the other operations to be much faster, 290 of these are enough.
Better attacks than this are available against two-key triple DES (which should only be used for backward compatibility, if at all).
Designer:
Description:
If K, K1 and K2 are the subkeys encoded as described below, then encryption and decryption are defined by:
EDESX[K, K1, K2](P) = EDES[K](P XOR K1) XOR K2
DDESX[K, K1, K2](C) = DDES[K](C XOR K3) XOR K2
If the user key length is 24 bytes, the first 8 bytes represent the key K used for the DES operation, and the two subsequent blocks of 8 bytes represent the "whitening" keys K1 and K2, in that order.
If the user key length is 16 bytes, the first 8 bytes represent the key K used for the DES operation, the second 8 bytes represent the whitening key K1, and K2 is derived from K and K1 as specified in the first reference below.
References:
- [_Def_] Mark Riordan,
Subject: Re: Ladder DES.
Posting to Usenet newsgroup sci.crypt, 1 Mar 1994.
(Message-ID: 2ku9uc$sr8@msuinfo.cl.msu.edu)
Archived at ftp://ftp.replay.com/pub/replay/mirror/ftp.cryptography.org/DESX/ desx.algorithm.description - [_An_] Joe Kilian, Phillip Rogaway,
"How to protect DES against exhaustive key search,"
Earlier version in Advances in Cryptology - CRYPTO '96, Volume 1109 of Lecture Notes in Computer Science (N. Koblitz, ed.), pp. 252-267. Springer-Verlag, 1996.
Full version: http://wwwcsif.cs.ucdavis.edu/~rogaway/papers/desx.ps - [_Inf_] U.S. National Institute of Standards and Technology,
NIST FIPS PUB 46-2 (supercedes FIPS PUB 46-1), "Data Encryption Standard", U.S. Department of Commerce, December 1993.
http://www.itl.nist.gov/div897/pubs/fip46-2.htm - [_Inf_] Bruce Schneier,
"Chapter 12 Data Encryption Standard,"
Applied Cryptography, Second Edition, John Wiley & Sons, 1996. - [_An_] John Kelsey, Bruce Schneier, David Wagner,
"Related-Key Cryptanalysis of 3-WAY, Biham-DES, CAST, DES-X, NewDES, RC2, and TEA",
ICICS '97 Proceedings, Springer-Verlag, November 1997.
http://www.counterpane.com/related-key_cryptanalysis.html
Key length:
128 or 192 bits; default 192 bits, as encoded. See security comments for the effective key length.
Block size:
8 bytes.
Comments:
- Implementations MUST ignore (i.e. not check) the parity bits of the single-DES key. KeyGenerators for DESX SHOULD generate entirely random keys (possibly avoiding DES weak keys). In the case of a 16-byte key, the input to the "hash procedure" which generates K2 is the original user key, without any adjustment to parity.
- There do not appear to be any "official" test vectors for DESX, so for reference we provide the following (the first was calculated using Mark Riordan's C implementation, and the second by hand based on official DES test data):
key = <0123456789ABCDEF1011121314151617>
plaintext = <4445535864657378>
ciphertext =
key = <01010101010101010123456789ABCDEF1011121314151617>
plaintext = <94DBE082549A14EF>
ciphertext = <9011121314151617>
Security comments:
- The paper "How to protect DES against exhaustive key search" proves that attacks on DESX that assume a "black-box" model for DES require a work factor of 2118. This does not take into account any possible weaknesses of DES, apart from the key complementation property. In particular, DESX is no more secure than DES against linear and differential cryptanalysis.
- DESX is vulnerable to related-key attacks, and therefore it should only be used with keys that are generated by a strong RNG, or by a source of bits that are sufficiently uncorrelated (such as the output of a hash function).
Designers:
Henri Gilbert, Marc Girault, Philippe Hoogvorst,Fabrice Noilhan,Thomas Pornin,Guillaume Poupard,Jacques Stern,Serge Vaudenay
Published:
May 1998
References:
- [_Def, An_] Henri Gilbert, Marc Girault, Philippe Hoogvorst, Fabrice Noilhan, Thomas Pornin, Guillaume Poupard, Jacques Stern, Serge Vaudenay,
Decorrelated Fast Cipher: an AES Candidate,
http://lasecwww.epfl.ch/query.msql?ref=GG%2B98b
(also see errata at the DFC home page) - [_Inf_] The Decorrelated Fast Cipher Home Page,
http://lasecwww.epfl.ch/dfc.shtml. - [_Inf_] Serge Vaudenay,
"The Decorrelation Technique,"
http://lasecwww.epfl.ch/decorrelation.shtml - [_An_] Lars Knudsen, Vincent Rijmen,
"On the decorrelated fast cipher (DFC) and its theory,"
Presented at Fast Software Encryption '99, Rome. - [_Patent_] Serge Vaudenay,
"Procédé de décorrélation des données,"
French patent application num. 96 13411. Requested on 4 November 1996. (Extension to other countries in process.) - [_Test_] NIST,
DFC Test Values,
http://www-08.nist.gov/encryption/aes/round1/testvals/dfc-vals.zip
Key length:
Minimum 0, maximum 256 bits, multiple of 8 bits; default 128 bits.
Block size:
16 bytes.
Patent status:
DFC itself is unpatented, but the decorrelation technique it uses may be covered by the patent application referenced above.
| DFCv2-128(rounds,s) | Block Cipher |
|---|
Designers:
Louis Granboulan, Phong Nguyen,Fabrice Noilhan,Serge Vaudenay
Published:
August 2000
References:
- [_Def, An, Test_] Louis Granboulan, Phong Nguyen, Fabrice Noilhan, Serge Vaudenay,
"DFCv2,"
In Selected Areas in Cryptography - Proceedings of SAC '2000 (D. Stinson and S. Tavares, eds.), Waterloo, Ontario, Canada, August 14-15 2000. To appear in Lecture Notes in Computer Science, Springer-Verlag.
http://www.di.ens.fr/~granboul/recherche/publications/ - [_Inf_] The Decorrelated Fast Cipher Home Page,
http://lasecwww.epfl.ch/dfc.shtml. - [_Inf_] Serge Vaudenay,
"The Decorrelation Technique,"
http://lasecwww.epfl.ch/decorrelation.shtml - [_Inf_] Olivier Baudron, Henri Gilbert, Louis Granboulan, Helena Handschuh, Robert Harley, Antoine Joux, Phong Nguyen, Fabrice Noilhan, David Pointcheval, Thomas Pornin, Guillaume Poupard, Jacques Stern, Serge Vaudenay,
"DFC Update,"
Presented at the 2nd AES Conference.
http://lasecwww.epfl.ch/query.msql?ref=BG%2B99b - [_An_] Lars Knudsen, Vincent Rijmen,
"On the decorrelated fast cipher (DFC) and its theory,"
Presented at Fast Software Encryption '99, Rome. - [_Patent_] Serge Vaudenay,
"Procédé de décorrélation des données,"
French patent application num. 96 13411. Requested on 4 November 1996. (Extension to other countries in process.)
Parameters:
Integer rounds[creation/read, no default] - the number of rounds to be performed (minimum 8, default 12, multiple of 2)Integer s[creation/read] - adjustment to key scheduling (minimum 4, default 4?)
Key length:
128, 192 or 256 bits; default 128 bits.
Block size:
16 bytes.
Comments:
Note that DFCv2 is not the same as the algorithm defined in the "DFC Update" paper (which did not have a sufficiently well-specified key schedule). That paper is included in the references only for comparison.
Patent status:
DFCv2 itself is unpatented, but the decorrelation technique it uses may be covered by the patent application referenced above.
| Diamond2(rounds) | Block Cipher |
|---|
Designer:
Michael Paul Johnson
Published:
1995
References:
- [_Def_] Michael Paul Johnson,
"The Diamond2 Block Cipher,"diamond2.{ps,doc}in ftp://ftp.zedz.com/pub/cryptoI/mirror/ftp.cryptography.org/libraries/dlock2.zip - [_Inf_] Michael Paul Johnson,
"Beyond DES: Data Compression and the MPJ Encryption Algorithm,"
Master's Thesis at the University of Colorado at Colorado Springs, 1989.thesis.txtin ftp://ftp.zedz.com/pub/cryptoI/mirror/ftp.cryptography.org/libraries/dlock2.zip
(Note: this describes an earlier version of Diamond, not Diamond2.) - [_Impl, Test_] Michael Paul Johnson,
Diamond2 reference implementation (in C++),
ftp://ftp.zedz.com/pub/cryptoI/mirror/ftp.cryptography.org/libraries/dlock2.zip
Parameters:
Integer rounds[creation/read, no default] - the number of rounds to be performed (minimum 10)
Key length:
Minimum 8, maximum 65536, multiple of 8 bits; default 128 bits.
Block size:
16 bytes.
Comments:
- The paper "The Diamond2 Block Cipher" does not appear to specify a recommended number of rounds, only a minimum number of rounds. For that reason, the rounds parameter has been made mandatory.
- The "Diamond2 Lite" variant does not have a standard name.
Designers:
Kazumaro Aoki, Masayuki Kanda, Tsutomu Matsumoto, Shiho Moriai, Kazuo Ohta, Miyako Ookubo, Youichi Takashima, Hiroki Ueda
Published:
June 1998
References:
- [_Def, An_] Specification of E2 - a 128-bit Block Cipher,
http://info.isl.ntt.co.jp/e2/E2spec.pdf - [_Inf_] The E2 Home Page,
http://info.isl.ntt.co.jp/e2/ - [_Inf_] Supporting Document on E2,
(corrected version, April 16 1999)
http://info.isl.ntt.co.jp/e2/E2support.pdf - [_Inf_] Kazumaro Aoki, Hiroki Ueda,
"Optimized Software Implementations of E2,"
Presented at the 2nd AES Conference.
http://csrc.nist.gov/encryption/aes/round1/conf2/papers/aoki.pdf - [_Inf_] Kazumaro Aoki, Hiroki Ueda,
"Optimized Software Implementations of E2,"
Revised April 15, 1999.
http://info.isl.ntt.co.jp/e2/RelDocs/implE2.pdf - [_Def, An_] M. Kanda, Y. Takashima, T. Matsumoto, K. Aoki, K. Ohta,
"A Strategy for Constructing Fast Round Functions with Practical Security against Differential and Linear Cryptanalysis,"
Presented at the 5th annual workshop on Selected Areas in Cryptography (SAC '98) in August, 1998. - [_An_] Makoto Sugita, Kazukuni Kobara, Hideki Imai,
"Pseudorandomness and Maximum Average of Differential Probability of Block Ciphers with SPN-Structures like E2,"
Presented at the 2nd AES Conference.
http://csrc.nist.gov/encryption/aes/round1/conf2/papers/sugita.pdf - [_An_] Yuji Hori, Toshinobu Kaneko,
"A study of E2 by higher order differential attack,"
Technical report of IEICE. ISEC98-39, Science University of Tokyo
(in Japanese - brief English summaryhere). - [_An_] Mitsuru Matsui, Toshio Tokita,
"On cryptanalysis of a byte-oriented cipher,"
The 1999 Symposium on Cryptography and Information Security, SCIS99-W2-1.5
(in Japanese - brief English summaryhere). - [_An_] Mitsuru Matsui, Toshio Tokita,
"Cryptanalysis of a Reduced Version of the Block Cipher E2,"
Fast Software Encryption '99 (March 1999), pp. 70-79 (abstract here). - [_An_] NTT Laboratories,
"Security of E2 aginst Truncated Differential Cryptanalysis (in progress),"
April 15 1999.
http://info.isl.ntt.co.jp/e2/RelDocs/E2trunc.pdf - [_An_] Makoto Sugita, Kazukuni Kobara, Kazuhiro Uehara, Shuji Kubota, Hideki Imai,
"Relationships among Differential, Truncated Differential, Impossible Differential Cryptanalyses against Word-Oriented Block Ciphers like Rijndael, E2,"
Presented at the 3rd AES Candidate Conference.
http://csrc.nist.gov/encryption/aes/round2/conf3/papers/32-msugita.pdf - [_An_] Matsui, Tokita,
"Cryptanalysis of block cipher E2,"
Presented at Fast Software Encryption '99, Rome. - [_Patent_] NTT (assignee),
"Data Randomize Device and Symmetric Cipher Devices (translated),"
Japanese Patent Application JP 173672/1997. - [_Patent_] NTT (assignee),
[[need patent titles]]
Japanese Patent Application JP 013572/1998.
Japanese Patent Application JP 013573/1998.
Japanese Patent Application JP 153066/1998.
Japanese Patent Application JP 147479/1998.
(Corresponding applications will be filed in other countries.) - [_Test_] NIST,
E2 Test Values,
http://www-08.nist.gov/encryption/aes/round1/testvals/e2-vals.zip
Key length:
128, 192 or 256 bits; default 128 bits.
Block size:
16 bytes.
Patent status:
NTT has several patents pending on E2 (see references).
| ? FROG[(blockSize_[,rounds_])] | Block Cipher |
|---|
Designers:
Dianelos Georgoudis, Damian Leroux, Billy Simón Chaves
Published:
1998
References:
- [_Def, An, Impl_] Dianelos Georgoudis, Damian Leroux, Billy Simón Chaves,
The "FROG" Encryption Algorithm,
June 15, 1998.
http://www.tecapro.com/aesfrog.htm - [_An_] F. Koeune, G.F. Piret, J.J. Quisquater,
Our first few comments about FROG,
August 1998.
http://www.dice.ucl.ac.be/crypto/CAESAR/frog.html - [_An_] David Wagner, Niels Ferguson, Bruce Schneier,
Cryptanalysis of FROG,
Corrected version, March 16, 1999. Presented at the 2nd AES Conference.
http://www.cs.berkeley.edu/~daw/papers/frog-final.ps
(slides: http://www.cs.berkeley.edu/~daw/papers/frog-slides.ps)
[Also see: http://www.counterpane.com/frog.html - is this the earlier version?] - [_Test_] NIST,
FROG Test Values,
http://www-08.nist.gov/encryption/aes/round1/testvals/frog-vals.zip
Parameters:
Integer blockSize[creation/read, default 16] - the length of a block in bytes (8 to 128)Integer rounds[creation/read, default 8] - the number of rounds to be performed (minimum 8)
Key length:
Minimum 40, maximum 1000, multiple of 8 bits; default 128 bits.
Block size:
As given by the blockSize parameter (in bytes).
Missing information:
Test vectors for block sizes other than 16 bytes.
Comment:
The original C reference code uses an unconventional byte order when printing test vectors (the order of bytes is reversed across the whole block). The correct byte order is that defined by the Java reference implementation, and by the NIST test vectors referenced above.
Security comment:
The paper "Cryptanalysis of FROG" describes the following attacks on weak keys:
- A differential attack requiring 258 chosen plaintexts and very little time for the analysis; it works for about 2-33.0 of the keyspace.
- A linear attack that uses 256 known texts and works for 2-31.8 of the keyspace.
- A ciphertext-only linear attack using 264 ciphertexts (also for 2-31.8 of the keyspace).
- A differential attack on the decryption function that requires 236 chosen ciphertexts and works for 2-29.3 of the keyspace.
Alias:
"GOST-28147-89"
Published:
1989
References:
- [_Def_] GOST, Gosudarstvennyi Standard 28147-89,
"Cryptographic Protection for Data Processing Systems,"
Government Committee of the USSR for Standards, 1989 (in Russian). - [_Def, Inf_] Bruce Schneier,
"Section 14.1 GOST,"
Applied Cryptography, Second Edition, John Wiley & Sons, 1996. - [_Inf_] J. Pieprzyk, L. Tombak,
"Soviet Encryption Algorithm,"
Preprint 94-10, Department of Computer Science, The University of Wollongong, 1994.
ftp://ftp.cs.uow.edu.au/pub/papers/1994/tr-94-10.ps.Z - [_An_] Markku-Juhani Saarinen,
A chosen key attack against the secret S-boxes of GOST,
http://www.cc.jyu.fi/~mjos/gost_cka.ps - [_An_] C. Charnes, L. O'Connor, J. Pieprzyk, R. Savafi-Naini, Y. Zheng,
"Comments on Soviet encryption algorithm,"
Advances in Cryptology - EUROCRYPT '94 Proceedings, Volume 950 of Lecture Notes in Computer Science (A. De Santis, ed.), pp. 433-438. Springer Verlag, 1995. - [_An_] C. Charnes, L. O'Connor, J. Pieprzyk, R. Safavi-Naini, Y. Zheng,
"Further comments on GOST encryption algorithm,"
Preprint 94-9, Department of Computer Science, The University of Wollongong, 1994.
ftp://ftp.cs.uow.edu.au/pub/papers/1994/tr-94-9.ps.Z - [_An_] John Kelsey, Bruce Schneier, David Wagner,
"Key-schedule cryptanalysis of IDEA, G-DES, GOST, SAFER, and triple-DES,"
Advances in Cryptology - CRYPTO '96 Proceedings. Springer-Verlag, August 1996.
http://www.cs.berkeley.edu/~daw/papers/keysched-crypto96.ps - [_Inf_] Markku-Juhani Saarinen,
C implementation and test vectors for GOST hash function,
http://www.tcs.hut.fi/~mjos/gosthash.tar.gz
[The implementation is of GOST-Hash, but this archive also contains a draft translation into English of the GOST 28147-89 standard.]
Parameters:
byte[][] sboxes[write only, default as given in Applied Cryptography] - the S-boxes to be used by this cipher instance.sboxes[i-1][j]represents the output of S-box i, for an input value j.
The implementation may or may not copy the contents of arrays used to set this parameter. If any such arrays are subsequently changed, the output of the cipher is undefined (it is therefore the responsibility of the caller to make sure that references to these arrays are not accessible to untrusted code). Setting this parameter will reset the current key and feedback vector, if applicable.
Key length:
256 bits.
Block size:
8 bytes.
Missing information:
Test vectors.
Security comment:
The paper "A chosen key attack against the secret S-boxes of GOST" cited above describes how to recover the S-boxes in about 232 encryptions. The main significance of this is on tamperproof hardware implementations where the S-boxes were assumed to be secret; for a software implementation, they should be assumed to be public in any case.
| HPC-1(blockSize_[,backup_]) | Block Cipher |
|---|
Designer:
Published:
1998
Description:
This is the original HPC cipher submitted as a first round AES candidate.
References:
- [_Def_] Rich Schroeppel, Hilarie Orman,
Specification for the Hasty Pudding Cipher,
http://www.cs.arizona.edu/~rcs/hpc/hpc-spec - [_Inf, Test_] Rich Schroeppel,
The Hasty Pudding Cipher page,
http://www.cs.arizona.edu/~rcs/hpc/ - [_An_] David Wagner,
Equivalent keys for HPC,
Rump session talk at the 2nd AES Conference.
Slides at: http://www.cs.berkeley.edu/~daw/papers/hpc-aes99-slides.ps - [_An_] Carl D'Halluin, Gert Bijnens, Bart Preneel, Vincent Rijmen,
Equivalent keys of HPC,
Katholieke Universiteit Leuven, ESAT-COSIC.
http://www.esat.kuleuven.ac.be/~rijmen/pub99.html - [_Inf_] Rich Schroeppel,
"The Hasty Pudding Cipher: One Year Later,"
June 12, 1999.
http://www.cs.arizona.edu/~rcs/hpc/hpc-oneyearlater - [_Test_] NIST,
HPC Test Values,
http://www-08.nist.gov/encryption/aes/round1/testvals/hpc-vals.zip
Parameters:
Integer blockSize[creation/read, default 16] - the length of a block in bytes (minimum 1)Integer backup[creation/read, default 0] - a parameter that can be increased to make the cipher more conservative, at the cost of speed (minimum 0)long[] spice[write, default all-zeroes] - an array of 8 64-bit words containing a diversifier.
The implementation may or may not copy the contents of arrays used to set this parameter. If any such array is subsequently changed, the output of the cipher is undefined, unless the parameter is set again immediately (it is therefore the responsibility of the caller to make sure that a reference to this array is not accessible to untrusted code). Setting this parameter will not reset the current key and feedback vector.
Key length:
Minimum 0, maximum 65536 bits; default 128 bits.
Block size:
As given by the blockSize parameter (in bytes). Note that while HPC supports block sizes that are not a multiple of 8 bits, the JCE API does not.
Comment:
The convention for encoding keys that are not a multiple of 8 bits in length, is for the last (effectiveBitLength % 8) bits of the key to be packed in the high-order bits of the last byte of the encoding. Any unused low-order bits of the last byte are ignored. For example, the key given by the 11-bit sequence <01010101 010>2, would be encoded as the byte array{ 0x55, 0x40 | junk }, wherejunk & 0xE0 == 0. The value of the key's effectiveBitLength parameter is used to determine how many bits of the encoding are significant.
Security comments:
- The paper "Equivalent keys of HPC" by D'Halluin et al, describes an attack which, for 128-bit keys, has an expected work factor of 289, and works for 1/256 of the keyspace. The analysis is extended to HPC with a 192-bit key and a 256-bit key, with similar results. For some other key lengths (including 56 bits), all keys are shown to be weak. The "tweak" described in "Tweaking the Hasty Pudding Cipher," (see HPC-2) is intended to correct this problem, but has not yet had a significant amount of analysis.
- Also note that with the default all-zeroes spice value, much of the work being done by the cipher has no cryptographic effect.
| ? HPC-2(blockSize_[,backup_]) | Block Cipher |
|---|
Designer:
Published:
June 1999
Description:
This is the "tweaked" version of HPC, with a modified key schedule.
References:
- [_Def_] Rich Schroeppel,
"Tweaking the Hasty Pudding Cipher,"
http://www.cs.arizona.edu/~rcs/hpc/tweak - [_Inf_] Rich Schroeppel,
"The Hasty Pudding Cipher: One Year Later,"
June 12, 1999.
http://www.cs.arizona.edu/~rcs/hpc/hpc-oneyearlater - [see references for HPC-1]
Parameters:
Integer blockSize[creation/read, default 16] - the length of a block in bytes (minimum 1)Integer backup[creation/read, default 0] - a parameter that can be increased to make the cipher more conservative, at the cost of speed (minimum 0)long[] spice[write, default all-zeroes] - an array of 8 64-bit words containing a diversifier.
The implementation may or may not copy the contents of arrays used to set this parameter. If any such array is subsequently changed, the output of the cipher is undefined, unless the parameter is set again immediately (it is therefore the responsibility of the caller to make sure that a reference to this array is not accessible to untrusted code). Setting this parameter will not reset the current key and feedback vector.
Key length:
Minimum 0, maximum 65536 bits; default 128 bits.
Block size:
As given by the blockSize parameter (in bytes). Note that while HPC supports block sizes that are not a multiple of 8 bits, the JCE API does not.
Missing information:
Test vectors.
Comment:
[see comment for HPC-1]
Security comment:
- Note that with the default all-zeroes spice value, much of the work being done by the cipher has no cryptographic effect.
Designer:
Published:
1997
References:
- [_Def, Test_] Matthew Kwan,
"The Design of the ICE Encryption Algorithm,"
Proceedings of Fast Software Encryption - Fourth International Workshop, Haifa, Israel, pp. 69-82. Springer-Verlag, 1997.
http://www.darkside.com.au/ice/paper.html - [_Inf, Impl_] The ICE Home Page,
http://www.darkside.com.au/ice/ - [_An_] Matthew Kwan,
Cryptanalysis of ICE,
http://www.darkside.com.au/ice/cryptanalysis.html - [_An_] B. Van Rompay, Lars Knudsen, Vincent Rijmen,
"Differential cryptanalysis of the ICE encryption algorithm,"
Fast Software Encryption, Volume 1372 of Lecture Notes in Computer Science (Serge Vaudenay, ed.), pp. 270-283. Springer-Verlag, 1998.
ftp://ftp.esat.kuleuven.ac.be/pub/COSIC/vrompay/fse98.ps.gz
Key length:
Minimum 64, multiple of 64 bits; default 128 bits.
Block size:
8 bytes.
Comment:
The length of the key defines the "level" parameter (note that the "Thin ICE" variant is not included).
Security comment:
The paper "Differential cryptanalysis of the ICE encryption algorithm" describes several differential attacks, including an attack against a variant reduced to 15 rounds, with 256 work and at most 256 chosen plaintexts. (The full algorithm has n/4 rounds when the key length is n bits.) The paper concludes:
[...] The main conclusion of this paper is that keyed permutation does not prevent differential cryptanalysis. Although the analysis is more complicated and becomes key dependent, in our opinion the intention of the design has not been reached. The best 3-round iterative characteristic that can be used in our attack has a probability of 2-13, which is higher than the probability of 2-16 of the best 3-round characteristic for LOKI91 (a similar block cipher that makes use of four identical 12 to 8-bit S-boxes).
These attacks are probably not practical when the number of rounds is 32 or higher (i.e. the key is 128 bits or longer). However, in that case ICE is slower than DES.
Designers:
Xuejia Lai, James Massey
Published:
1992
Alias:
"OpenPGP.Cipher.1"
Object Identifiers:
- 1.3.6.1.4.1.188.7.1.1.1 for IDEA/ECB
- 1.3.6.1.4.1.188.7.1.1.2 for IDEA/CBC
- 1.3.6.1.4.1.188.7.1.1.3 for IDEA/CFB
- 1.3.6.1.4.1.188.7.1.1.4 for IDEA/OFB
(source for OIDs)
References:
- [_Def, An_] X. Lai,
"On the design and security of block ciphers",
ETH Series in Information Processing (J.L. Massey, ed.), Vol. 1, Hartung-Gorre Verlag, Konstanz Technische Hochschule (Zurich), 1992. - [_Inf, An_] X. Lai, J.L. Massey, S. Murphy,
"Markov Ciphers and Differential Cryptanalysis,"
Advances in Cryptology - EUROCRYPT '91, Volume 547 of Lecture Notes in Computer Science (D.W. Davies, ed.), pp. 17-38. Springer-Verlag, 1991. - [_Inf_] The IDEA Algorithm page.
http://www.mediacrypt.com/
Older version archived at http://web.archive.org/web/20000816173927/http://www.ascom.ch/infosec/idea/oid.html - [_Inf_] Bruce Schneier,
"Section 13.9 IDEA,"
Applied Cryptography, Second Edition, John Wiley & Sons, 1996.
(Note: there is an error in the description; the diagram is correct.) - [_Inf_] A. Menezes, P.C. van Oorschot, S.A. Vanstone,
"Section 7.6 IDEA,"
Handbook of Applied Cryptography, CRC Press, 1997.
http://www.cacr.math.uwaterloo.ca/hac/about/chap7.pdf,.ps - [_An_] Joan Daemen, René Govaerts, Joos Vandewalle,
"Weak Keys of IDEA,"
Advances in Cryptology - CRYPTO '93 Proceedings, Volume 773 of Lecture Notes in Computer Science (D. Stinson, ed.), pp. 224-231. Springer-Verlag, 1994.
http://www.esat.kuleuven.ac.be/~cosicart/ps/JD-9304.ps.gz - [_An_] Joan Daemen, René Govaerts, Joos Vandewalle,
"Cryptanalysis of 2.5 Rounds of IDEA,"
ESAT-COSIC Technical Report 93/1, 1993.
http://www.esat.kuleuven.ac.be/~cosicart/ps/JD-9306.ps.gz - [_An_] J. Borst, L. Knudsen, V. Rijmen,
"Two attacks on reduced IDEA,"
Advances in Cryptology - EUROCRYPT '97 Proceedings, Volume 1233 of Lecture Notes in Computer Science (W. Fumy, ed.), pp. 1-13. Springer-Verlag, 1997.
ftp://ftp.esat.kuleuven.ac.be/pub/COSIC/rijmen/idea.ps.gz - [_An_] L. Knudsen, V. Rijmen,
"Truncated Differentials of IDEA,"
ESAT-COSIC Technical Report 97-1.
ftp://ftp.esat.kuleuven.ac.be/pub/COSIC/knudsen/idea_trunc.ps.Z - [_An_] John Kelsey, Bruce Schneier, David Wagner,
"Key-Schedule Cryptanalysis of 3-WAY, IDEA, G-DES, RC4, SAFER, and Triple-DES".
http://www.counterpane.com/key_schedule.html - [_An_] Phillip Hawkes,
"Differential-Linear Weak Key Classes of IDEA,"
Advances in Cryptology - EUROCRYPT '98 Proceedings, pp. 112-126, Springer-Verlag, 1998. - [_An_] E. Biham, A. Biruykov, A. Shamir,
"Miss in the middle attacks on IDEA, Khufu and Khafre,"
Presented at Fast Software Encryption '99, Rome. - [_An_] John Kelsey, Bruce Schneier, David Wagner, Chris Hall,
"Side Channel Cryptanalysis of Product Ciphers",
ESORICS '98 Proceedings pp. 97-110, Springer-Verlag, September 1998.
http://www.counterpane.com/side_channel.html - [_Inf, An_] Ascom Systec, Ltd.
"Side Channel Attack Hardening of the IDEATM Cipher,"
Ascom Systec White Paper (corrected version, May 1999).
http://web.archive.org/web/20000823133119/www.ascom.ch/infosec/downloads/sidechannel.pdf - [_An_] Jorge Nakahara Jr., Paulo Barreto, Bart Preneel, Joos Vandewalle, Hae Y. Kim,
"SQUARE Attacks on Reduced-Round PES and IDEA Block Ciphers,"
NESSIE Project phase 2 public report, 19 November 2001.
https://www.cosic.esat.kuleuven.ac.be/nessie/reports/phase2/nessie-idea.pdf - [_An_] Alex Biryukov, Jorge Nakahara Jr., Bart Preneel, Joos Vandewalle,
"New Weak Key Classes of IDEA,"
NESSIE Project phase 2 public report, 29 June 2002.
https://www.cosic.esat.kuleuven.ac.be/nessie/reports/phase2/keyidea5.pdf - [_Patent_] James Massey, Xuejia Lai,
"Device for Converting a Digital Block and the Use Thereof",
International Patent WO09118459A2, filed May 16 1991, issued November 28 1991. - [_Patent_] James Massey, Xuejia Lai,
"Device for Converting a Digital Block and the Use Thereof,"
European Patent EP00482154A1, filed May 16 1991, issued April 29 1992. - [_Patent_] James Massey, Xuejia Lai,
"Device for Converting a Digital Block and the Use Thereof,"
European Patent EP00482154B1, filed May 16 1991, issued June 30 1993. - [_Patent_] James Massey, Xuejia Lai,
"Device for the Conversion of a Digital Block and Use of Same",
U.S. Patent 5,214,703, filed January 7 1992, issued May 25 1993. - [_Patent_] James Massey, Xuejia Lai,
[[filed Japanese Patent Application No. 508119/1991]] - [_Impl, Test_] Ascom Systec, Ltd.
IDEA C Source Code and Test Data (corrected version, May 1999).
http://web.archive.org/web/20000816173624/www.ascom.ch/infosec/downloads.html
Key length:
128 bits.
Block size:
8 bytes.
Comments:
- A version of the IDEA C reference code available in April and early May 1999 contained a bug in the code for multiplication mod 216+1, which occurs when multiplying two zero words; this bug is not caught by the standard test vectors. An additional test vector that does catch the bug (and incidentally demonstrates a weakness of IDEA's key schedule, but that's beside the point) is:
key = <00000000000000000000000000000000>
plaintext = <0000000000000000>
ciphertext = <0001000100000000> - The test vectors, reference implementation and papers that were previously available from the Ascom web site (including the important paper on side channel attack hardening) have all disappeared from that site. Congratulations to Ascom, iT_Security, Mediacrypt, or whatever its name is this week, for providing an excellent example of how not to handle web site reorganisations. Fortunately all of these files were recoverable fromweb.archive.org (thanks to Jason Harris for pointing this out).
Security comment:
IDEA is vulnerable to key schedule attacks, and therefore it should only be used with keys that are generated by a strong RNG, or by a source of bits that are sufficiently uncorrelated (such as the output of a hash function).
Patent status:
IDEA is patented in the U.S and 9 European countries by Ascom Systec Ltd., with a patent pending in Japan.
Designer:
Published:
1996
References:
- [_Def, An_] Robert J. Jenkins Jr.,
ISAAC and RC4,
http://www.burtleburtle.net/bob/rand/isaac.html - [Inf, An, Test, _Impl_] Robert J. Jenkins Jr.,
ISAAC: a fast cryptographic random number generator,
http://www.burtleburtle.net/bob/rand/isaacafa.html - [_Inf_] Robert J. Jenkins Jr.,
"ISAAC,"
Fast Software Encryption, Third International Workshop, Volume 1039 of Lecture Notes in Computer Science (D. Gollman, ed.), pp. 41-49. Springer-Verlag, 1996.
Key length:
?
Missing information:
ISAAC does not appear to have a standard key schedule; this would need to be specified for it to be usable as a SCAN algorithm. Test vectors would also be needed.
Designer:
Published:
1996
References:
[see references for ]
Key length:
?
Missing information:
[see ]
| × ISAAC-64-BE | Stream Cipher |
|---|
Designer:
Published:
1996
References:
- [_Def, An_] Robert J. Jenkins Jr.,
ISAAC and RC4,
http://www.burtleburtle.net/bob/rand/isaac.html
Key length:
?
Missing information:
ISAAC-64 does not appear to have a standard key schedule; this would need to be specified for it to be usable as a SCAN algorithm. Test vectors would also be needed.
| × ISAAC-64-LE | Stream Cipher |
|---|
Designer:
Published:
1996
References:
[see references for ]
Key length:
?
Missing information:
[see ]
Designers:
Hervé Chabanne, Emmanuel Michon
Published:
1998
Description:
This algorithm refers to JEROBOAM version 2.0.
Alias:
"JEROBOAM-2.0"
References:
- [_Def, An_] Hervé Chabanne, Emmanuel Michon,
"JEROBOAM",
Fast Software Encryption '98, Volume 1372 of Lecture Notes in Computer Science (Serge Vaudenay, ed.), pp. 49-59. Springer-Verlag, 1998. - [_Def, An_] Emmanuel Michon,
Rapport de stage d'option scientifique: étude cryptologique du chiffreur JEROBOAM,
Ecole Polytechnique, June 1997.
Key length:
128 or 248 bits
Missing information:
I have not yet read either of the referenced papers, so I don't know whether byte-order is specified, status of test vectors, etc.
| × LEVIATHAN-BE | Stream Cipher |
|---|
Designers:
David McGrew, Scott Fluhrer
Published:
October 2000
Description:
This is LEVIATHAN using big-endian byte order, when XORing the keystream with the plaintext for encryption.
References:
- [_Def, An_] David McGrew, Scott Fluhrer,
The Stream Cipher LEVIATHAN - Specification and Supporting Documentation,
Presented at the First Open NESSIE Workshop, November 2000.
https://www.cosic.esat.kuleuven.ac.be/nessie/workshop/submissions/leviathan.zip - [_Def, An_] Paul Crowley,
Analysis of LEVIATHAN,
http://www.cluefactory.org.uk/paul/crypto/leviathan.html
Key length:
128 or 256 bits
Security comment:
The output of LEVIATHAN can be distinguished from a random stream given about ??? MBytes of output.
| × LEVIATHAN-LE | Stream Cipher |
|---|
Designers:
David McGrew, Scott Fluhrer
Published:
October 2000
Description:
This is LEVIATHAN using little-endian byte order, when XORing the keystream with the plaintext for encryption.
References:
[see references for LEVIATHAN-BE]
Key length:
128 or 256 bits
Security comment:
[see Security comment for LEVIATHAN-BE]
Designers:
Laurence Brown,Matthew Kwan, Josef Pieprzyk,Jennifer Seberry
Published:
1991-92
References:
- [_Def, An_] Laurence Brown, Matthew Kwan, Josef Pieprzyk, Jennifer Seberry,
"Improving Resistance to Differential Cryptanalysis and the Redesign of LOKI,"
Advances in Cryptology - ASIACRYPT '91 Proceedings, Springer-Verlag, 1993, pp. 36-50. - [_Inf_] Bruce Schneier,
"Section 13.6 LOKI,"
Applied Cryptography, Second Edition, John Wiley & Sons, 1996. - [_An_] Eli Biham,
"New Types of Cryptanalytic Attacks Using Related Keys,"
CS 753, Computer Science Department, Technion -- Israel Institute of Technology, September 1992.
http://www.cs.technion.ac.il/users/wwwb/cgi-bin/tr-get.cgi/1992/CS/CS0753.ps - [_An_] Lars Knudsen,
"Cryptanalysis of LOKI91,"
Volume 718 of Lecture Notes in Computer Science, pp. 196-208. Springer-Verlag, 1992.
ftp://ftp.esat.kuleuven.ac.be/pub/COSIC/knudsen/loki91.ps.Z - [_An_] Lars Knudsen,
"Block ciphers - analysis, design and applications,"
PhD. Thesis, DAIMI PB 485, Aarhus University, 1994. - [_An_] Toshio Tokita, Tohru Sorimachi, Mitsuru Matsui,
"Linear cryptanalysis of LOKI and S2DES,"
Volume 917 of Lecture Notes in Computer Science, pp. 293-306. Springer-Verlag, 1994. - [_An_] Lars Knudsen, M.J.B. Robshaw,
"Non-linear Approximations in Linear Cryptanalysis,"
Volume 1070 of Lecture Notes in Computer Science, pp. 224-236. Springer-Verlag, 1996.
ftp://ftp.esat.kuleuven.ac.be/pub/COSIC/knudsen/nonlinear.ps.Z - [_An_] Kouichi Sakurai, Souichi Furuya,
"Improving Linear Cryptanalysis of LOKI91 by Probabalistic Counting Method,"
Volume ??? of Lecture Notes in Computer Science. Springer-Verlag, 1997. - [_An_] Lars Knudsen,
"New potentially weak keys for DES and LOKI,"
Advances in Cryptology - EUROCRYPT '94 Proceedings, Volume 950 of Lecture Notes in Computer Science (A. De Santis, ed.), pp. 419-424. Springer Verlag, 1995.
ftp://ftp.esat.kuleuven.ac.be/pub/COSIC/knudsen/potential.ps.Z
Key length:
64 bits.
Block size:
8 bytes.
Security comments:
- LOKI91 is vulnerable to related-key attacks, with a work factor of about 260 operations, and therefore it should only be used with keys that are generated by a strong RNG, or by a source of bits that are sufficiently uncorrelated (such as the output of a hash function).
- The attacks cited above based on Linear Cryptanalysis, are effective against reduced-round variants of LOKI91 with up to 12 rounds (the full cipher has 16 rounds).
- The fixed 64-bit key length is too short to prevent brute-force attacks.
Designers:
Laurence Brown, Josef Pieprzyk,Jennifer Seberry
Published:
1997
References:
- [_Def, An_] Laurence Brown, Josef Pieprzyk,
Introducing the new LOKI97 Block Cipher,
http://www.adfa.oz.au/~lpb/research/loki97/loki97spec.ps - [_Inf, Impl_] Laurence Brown,
The LOKI97 Block Cipher page,
http://www.adfa.oz.au/~lpb/research/loki97/ - [_An_] Vincent Rijmen, Lars Knudsen,
Weaknesses in LOKI97,
ftp://ftp.esat.kuleuven.ac.be/pub/COSIC/rijmen/loki97.pdf - [_Test_] NIST,
LOKI97 Test Values,
http://www-08.nist.gov/encryption/aes/round1/testvals/loki97-vals.zip
Key length:
128, 192 or 256 bits; default 128 bits.
Block size:
16 bytes.
Security comment:
The paper "Weaknesses in LOKI97" describes an attack using Differential Cryptanalysis, estimated as requiring at most 256 chosen plaintexts, and an attack using Linear Cryptanalysis, estimated as requiring at most 256 known plaintexts.
Designers:
Michael Jacobson Jr., Klaus Huber
Published:
August 1998
References:
- [_Def, An_] M.J. Jacobson Jr., K. Huber,
The MAGENTA Block Cipher Algorithm,
http://www.gel.ulaval.ca/~klein/maitrise/aes/magenta.pdf - [_An_] Eli Biham, Alex Biryukov, Niels Ferguson, Lars Knudsen, Bruce Schneier, Adi Shamir,
"Cryptanalysis of Magenta,"
Distributed at the first AES conference, August 20, 1998.
http://www.counterpane.com/magenta.html - [_Patent_] [[need patent title]]
German Patent DE 44 25 158 A1, [[need date]]. - [_Test_] NIST,
MAGENTA Test Values,
http://www-08.nist.gov/encryption/aes/round1/testvals/magenta-vals.zip
Key length:
128, 256, or 256 bits; default 128 bits.
Block size:
16 bytes.
Security comment:
The paper "Cryptanalysis of Magenta" describes a chosen plaintext attack using 264 chosen plaintexts, and 264 work. It also notes that "given a ciphertext, one can decrypt it by swapping its two halves, re-encrypting the result, and swapping again". This would be a fatal weakness for some applications, even though it does not allow obtaining the key.
Patent status:
MAGENTA may be patented (see references).
Designers:
Carolynn Burwick, Don Coppersmith, Edward D'Avignon,Rosario Gennaro,Shai Halevi, Charanjit Jutla, Stephen M. Matyas Jr., Luke O'Connor, Mohammad Peyravian, David Safford, Nevenko Zunicof
Published:
August? 1999
Description:
This is the "tweaked" version of MARS submitted as a second round AES candidate.
Alias:
"MARS-2"
References:
- [_Def, An_] Carolynn Burwick, Don Coppersmith, Edward D'Avignon, Rosario Gennaro, Shai Halevi, Charanjit Jutla, Stephen M. Matyas Jr., Luke O'Connor, Mohammad Peyravian, David Safford, Nevenko Zunicof,
"MARS - A candidate cipher for AES," (corrected version).
Available from http://www.research.ibm.com/security/mars.html
[Note that the key schedule described here (in mars.pdf/.ps) is for the initial version of MARS submitted as a first round AES candidate.] - [_Def_] Shai Halevi,
"MARS key setup,"
http://www.research.ibm.com/security/key-setup.txt - [_An_] Scott Contini, Yiqun Lisa Yin,
"On Differential Properties of Data-Dependent Rotations and Their Use in MARS and RC6,"
Presented at the 2nd AES Conference.
http://csrc.nist.gov/encryption/aes/round1/conf2/papers/contini.pdf - [_An_] John Kelsey, Bruce Schneier,
"MARS Attacks! Preliminary Cryptanalysis of Reduced-Round MARS Variants,"
Presented at the 3rd AES Candidate Conference.
http://www.counterpane.com/mars-attacks.html - [_An_] Eli Biham, Vladimir Furman,
"Impossible Differential on 8-Round MARS' Core,"
March 15, 2000. Presented at the 3rd AES Candidate Conference.
http://csrc.nist.gov/encryption/aes/round2/conf3/papers/07-ebiham.pdf - [_An_] L. Burnett, G. Carter, E. Dawson, W. Millan,
"Efficient methods for generating MARS-like S-boxes,"
Presented at Fast Software Encryption 2000. - [_An_] L. Knudsen, H. Raddum,
"Linear Approximations to MARS S-Box,"
Submitted to NIST as an AES comment, April 2000.
http://csrc.nist.gov/encryption/aes/round2/comments/20000407-lknudsen.pdf - [_An_] M. Robshaw, Y. Lin,
"Potential Flaws in the Conjectured Resistance of MARS to Linear Cryptanalysis,"
Submitted to NIST as an AES comment, May 2000.
http://csrc.nist.gov/encryption/aes/round2/comments/20000502-mrobshaw.pdf - [_An_] B. Preneel, A. Bosselaers, V. Rijmen, B. Van Rompay, L. Granboulan, J. Stern, S. Murphy, M. Dichtl, P. Serf, E. Biham, O. Dunkelman, V. Furman, F. Koeune, G. Piret, J-J. Quisquater, L. Knudsen, H. Raddum,
"Comments by the NESSIE Project on the AES Finalists,"
Submitted to NIST as an AES comment, May 2000.
http://csrc.nist.gov/encryption/aes/round2/comments/20000524-bpreneel.pdf - [_An_] IBM MARS Team,
"Comments on MARS's linear analysis,"
Submitted to NIST as an AES comment, May 2000.
http://csrc.nist.gov/encryption/aes/round2/comments/20000515-ibm-2.pdf - [_An_] Tetsu Iwata, Kaoru Kurosawa,
"On the Pseudorandomness of AES Finalists - RC6, Serpent, MARS and Twofish,"
Presented at Fast Software Encryption 2000, New York. - [_An_] John Kelsey, Tadayoshi Kohno, Bruce Schneier,
"Amplified Boomerang Attacks Against Reduced-Round MARS and Serpent,"
Presented at Fast Software Encryption 2000, New York.
http://www.counterpane.com/boomerang.html - [_Patent_] [[need patent title and date]]
U.S. Patent Application: IBM application CR998021. - [_Test_] IBM Corporation,
New MARS Test Vectors,
http://www.research.ibm.com/security/test-vectors/
Key length:
Minimum 128, maximum 448, multiple of 32 bits; default 128 bits.
Block size:
16 bytes.
Patent status:
IBM has a patent pending on MARS. It has said that "... we are making MARS available on a royalty-free basis, worldwide, regardless of AES outcome." (See this press release.) However, it is not clear whether "royalty-free" excludes the possibility of up-front license fees.
Designer:
Peter Gutmann
Published:
October 1992
References:
- [_Def_] Peter Gutmann,
Subject: MDC cipher code (long),
ftp://ftp.zedz.com/pub/crypto/libraries/mdc/mdc-gutmann.c.gz - [_Impl_] Peter Gutmann,
MDC reference implementation (in C),
ftp://ftp.zedz.com/pub/crypto/libraries/mdc/
Key length:
Minimum 64, maximum 640, multiple of 8 bits; default 128 bits.
Missing information:
Test vectors.
Comments:
- With regard to buffering and use of IVs, MDC behaves identically to the CFB mode of a block cipher. The length of the initialisation vector is 16 bytes. Implementations MUST support immediate processing of individual bytes.
- MDC has nothing to do with the cipher constructions MDC-2 and MDC-4 designed at IBM (which do not have SCAN standard names).
Security comment:
A new random IV should be used for each message encrypted under a given key.
| MISTY1[(rounds)] | Block Cipher |
|---|
Designer:
M. Matsui
Published:
January 1997
References:
- [_Def_] M. Matsui,
"New Block Encryption Algorithm MISTY,"
4th Fast Software Encryption Workshop, January 1997.
http://www.mitsubishi.com/ghp_japan/misty/misty_e_b.pdf,.ps - [_Inf_] Mitsubishi Electric,
MISTY home page,
http://www.mitsubishi.com/ghp_japan/misty/200misty.htm - [_Inf_] M. Matsui,
"Block Encryption Algorithm MISTY," (in Japanese)
Technical Report of IEICE, ISEC96-11 (1996-07).
http://www.mitsubishi.com/ghp_japan/misty/misty_j_b.pdf,.ps - [_Inf_] M. Matsui,
"New Structure of Block Ciphers with Provable Security against Differential and Linear Cryptanalysis,"
3rd Fast Software Encryption Workshop, February 1996.
Parameters:
Integer rounds[creation/read, default 8] - the number of rounds to be performed (minimum 8, multiple of 4)
Key length:
128 bits.
Block size:
8 bytes.
| ? MISTY2[(rounds)] | Block Cipher |
|---|
Designer:
M. Matsui
Published:
January 1997
References:
- [_Def_] M. Matsui,
"New Block Encryption Algorithm MISTY,"
4th Fast Software Encryption Workshop, January 1997.
http://www.mitsubishi.com/ghp_japan/misty/misty_e_b.pdf,.ps - [_Inf_] Mitsubishi Electric,
MISTY home page,
http://www.mitsubishi.com/ghp_japan/misty/200misty.htm - [_Inf_] M. Matsui,
"Block Encryption Algorithm MISTY," (in Japanese)
Technical Report of IEICE, ISEC96-11 (1996-07).
http://www.mitsubishi.com/ghp_japan/misty/misty_j_b.pdf,.ps - [_Inf_] M. Matsui,
"New Structure of Block Ciphers with Provable Security against Differential and Linear Cryptanalysis,"
3rd Fast Software Encryption Workshop, February 1996.
Parameters:
Integer rounds[creation/read, default 12] - the number of rounds to be performed (minimum 12, multiple of 4)
Key length:
128 bits.
Block size:
8 bytes.
Missing information:
Test vectors.
| Noekeon[(rounds)] | Block Cipher |
|---|
Designers:
Joan Daemen, Michaël Peeters, Gilles van Assche,Vincent Rijmen
Published:
November 2000
References:
- [_Def, An_] Joan Daemen, Michaël Peeters, Gilles van Assche, Vincent Rijmen,
The Noekeon Block Cipher,
Presented at the First Open NESSIE Workshop, November 2000.
https://www.cosic.esat.kuleuven.ac.be/nessie/workshop/submissions/noekeon.zip - [_Inf_] Proton World,
Research: Noekeon, a 128-bit block cipher,
http://www.protonworld.com/research/noekeon/ - [_Test_] Joan Daemen, Michaël Peeters, Gilles van Assche, Vincent Rijmen,
Noekeon Test Values,
https://www.cosic.esat.kuleuven.ac.be/nessie/workshop/submissions/noekeon.zip
Parameters:
Integer rounds[creation/read, default 16] - the number of rounds to be performed (minimum 16)
Key length:
128 bits.
Block size:
16 bytes.
| Noekeon-Direct[(rounds)] | Block Cipher |
|---|
Designers:
Joan Daemen, Michaël Peeters, Gilles van Assche,Vincent Rijmen
Published:
November 2000
Description:
This is the "direct-key" variant of Noekeon, i.e. where the working key is provided directly. This key should be generated at random, or as the output of a hash or PRF.
References:
- [_Def, An_] Joan Daemen, Michaël Peeters, Gilles van Assche, Vincent Rijmen,
The Noekeon Block Cipher,
http://www.cryptonessie.org/submissions/noekeon/noekeon.zip - [_Inf, Test_] Joan Daemen, Vincent Rijmen,
The Noekeon Page,
http://www.esat.kuleuven.ac.be/~rijmen/noekeon/ - [_Test_] NIST,
Noekeon Test Values,
http://www.cryptonessie.org/submissions/noekeon/noekeon.zip
Parameters:
Integer rounds[creation/read, default 16] - the number of rounds to be performed (minimum 16)
Key length:
128 bits.
Block size:
16 bytes.
Designers:
Published:
1998
References:
- [_Def, An_] Joan Daemen, Craig Clapp,
"Fast Hashing and Stream Encryption with Panama,"
Fast Software Encryption '98, Volume 1372 of Lecture Notes in Computer Science (Serge Vaudenay, ed.), pp. 60-74. Springer-Verlag, 1998.
http://standard.pictel.com/ftp/research/security/panama.pdf - [_Inf_] Joan Daemen,
Panama reference implementation (in C),
http://www.esat.kuleuven.ac.be/~rijmen/daemen/panama.zip
Key length:
256 bits.
Missing information:
Test vectors (panama.zip only contains test vectors for hashing).
Comment:
Panama makes use of a "diversification parameter" that is appended to the key. This is handled by treating the diversification parameter as an IV (which can be set in the same way as would be used for a block cipher).
Note that this implies that an implementation must save the user key (or the state of the cipher after loading this key), in order to ensure that more than one call to setIV can be made without having to reinitialise the cipher object.
Designers:
Chang-Hyi Lee, Jeong-Soo Kim
References:
- [_Def, An_] Chang-Hyi Lee, Jeong-Soo Kim,
"The New Block Cipher Rainbow,"RB_paper.psin http://www.ii.uib.no/~larsr/papers/rainbow.zip - [_Impl_] Chang-Hyi Lee, Jeong-Soo Kim,
Rainbow reference implementation (in C),
http://www.ii.uib.no/~larsr/papers/rainbow.zip
Key length:
Minimum 128, maximum 256, multiple of 32 bits; default 128 bits.
Block size:
16 bytes.
Missing information:
Test vectors.
Comment:
Only the 128-bit block version is defined as a SCAN algorithm.
Designer:
Published:
1998
References:
- [_Def_] Ron Rivest,
"A Description of the RC2(r) Encryption Algorithm,"
RFC 2268, March 1998. - [_An_] L.R. Knudsen, V. Rijmen, R.L. Rivest, M.J.B. Robshaw,
"On the design and security of RC2,"
Fast Software Encryption, Volume 1372 of Lecture Notes in Computer Science (Serge Vaudenay, ed.), pp. 206-221. Springer-Verlag, 1998.
http://www.esat.kuleuven.ac.be/~cosicart/ps/VR-9800.ps.gz - [_An_] John Kelsey, Bruce Schneier, David Wagner,
"Related-Key Cryptanalysis of 3-WAY, Biham-DES, CAST, DES-X, NewDES, RC2, and TEA",
ICICS '97 Proceedings, Springer-Verlag, November 1997.
http://www.counterpane.com/related-key_cryptanalysis.html
Key length:
Minimum 0; maximum 1024, multiple of 8 bits; default 128 bits.
Block size:
8 bytes.
Comment:
The value of the key's effectiveBitLength parameter may be different from 8 * (length of key encoding in bytes), to allow compatibility with other RC2 implementations. However, RC2 KeyGenerators should always generate keys such that the length of the encoding is equal to (effectiveBitLength + 7) / 8 bytes. (To create keys that do not satisfy this constraint, an application has to construct a SecretKey object directly.)
Note that the table given in section 6 of RFC 2268 plays no part in determining the number of effective bits (and also, the default key length is 128 bits,not 32 as implied by that section).
Security comment:
RC2 is vulnerable to related-key attacks, and therefore it should only be used with keys that are generated by a strong RNG, or by a source of bits that are sufficiently uncorrelated (such as the output of a hash function).
Designer:
Published:
September 1994 (see Comment section below)
Alias:
"ARCFOUR"
References:
- [_Def_] Bruce Schneier,
"Section 17.1 RC4,"
Applied Cryptography, Second Edition, John Wiley & Sons, 1996. - [_Def_] Anonymous,
Subject: RC4 Algorithm revealed,
Posting to Usenet newsgroups sci.crypt, alt.security, comp.security.misc, and alt.privacy, September 14 1994 (reposting of a message to the cipherpunks mailing list).
Message-ID: sternCvKL4B.Hyy@netcom.com
Archived at ftp://idea.sec.dsi.unimi.it/pub/security/crypt/code/rc4.revealed.gz - [_An_] Hal Finney,
Subject: An RC4 cycle that can't happen,
Posting to sci.crypt, 18 September 1994.
Message-ID: 35hq1u$c72@news1.shell - [_An_] David Wagner,
Subject: Re: Weak Keys in RC4,
Posting to sci.crypt, 26 September 1995.
Message-ID: 447o1l$cbj@cnn.Princeton.EDU
Archived at http://www.cs.berkeley.edu/~daw/my-posts/my-rc4-weak-keys - [_An_] Andrew Roos andrewr@vironix.co.za,
A Class of Weak Keys in the RC4 Stream Cipher,
November 1997.
http://www.tik.ee.ethz.ch/~mwa/RC4/WeakKeys.txt
(Also two postings to sci.crypt in 1995; Message-IDs 43u1eh$1j3@hermes.is.co.za and 44ebge$llf@hermes.is.co.za.) - [_An_] John Kelsey, Bruce Schneier, David Wagner,
"Key-Schedule Cryptanalysis of 3-WAY, IDEA, G-DES, RC4, SAFER, and Triple-DES".
http://www.counterpane.com/key_schedule.html - [_An_] Jovan Goli
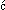 ,
,
"Linear Statistical Weakness of Alleged RC4 Keystream Generator,"
Advances in Cryptology - EUROCRYPT '97 Proceedings, Volume 1233 of Lecture Notes in Computer Science (W. Fumy, ed.) Springer-Verlag, 1997.
http://www.wisdom.weizmann.ac.il/~itsik/RC4/Golic.PDF - [_An_] Lars Knudsen, Willi Meier, Bart Preneel, Vincent Rijmen, Sven Verdoolaege,
"Analysis Methods for (Alleged) RC4,"
Advances in Cryptology - ASIACRYPT '98 Proceedings, Volume 1514 of Lecture Notes in Computer Science (K. Ohta, D. Pei, eds.), pp. 327-341. Springer-Verlag, 1998.
http://www.wisdom.weizmann.ac.il/~itsik/RC4/Knudsen.ps or
http://www.esat.kuleuven.ac.be/~cosicart/ps/VR-9801.ps.gz - [_An_] Serge Mister,
"Cryptanalysis of RC4-like Ciphers,"
Master's Thesis, Queen's University, Kingston, Ontario, Canada. May 1998. - [_An_] Serge Mister, Stafford Tavares,
"Cryptanalysis of RC4-like Ciphers,"
Workshop Record of the Workshop on Selected Areas in Cryptography (SAC '98), August 17-18 1998, pp. 136-148.
Abstract only at http://www.ncf.carleton.ca/~cf744/pub.html - [_An_] Alexander L. Grosul, Dan S. Wallach,
"A Related-Key Cryptanalysis of RC4,"
Rice University TR00-358, June 2000.
http://www.wisdom.weizmann.ac.il/~itsik/RC4/GrosulWallach.ps - [_An_] Scott Fluhrer, David McGrew,
"Statistical Analysis of the Alleged RC4 Keystream Generator,"
Presented at Fast Software Encryption 2000, New York.
http://www.mindspring.com/~dmcgrew/rc4-03.pdf - [_An_] Itsik Mantin, Adi Shamir,
"A Practical Attack on Broadcast RC4,"
Presented at Fast Software Encryption 2001.
http://www.wisdom.weizmann.ac.il/~itsik/RC4/bc_rc4.ps - [_An_] Scott Fluhrer, Itsik Mantin, Adi Shamir,
"Weaknesses in the Key Scheduling Algorithm of RC4,"
In Proceedings of SAC 2001, Eighth Annual Workshop on Selected Areas in Cryptography (Toronto, Ontario, Canada, August 2001), pp. 1-24.
http://www.crypto.com/papers/others/rc4_ksaproc.ps - [_An_] Itsik Mantin,
"Analysis of the stream cipher RC4,"
Master's Thesis, Weizmann Insitute, Israel, 2001. - [_An_] G. Durfee,
"Distinguishers for the RC4 stream cipher,"
Manuscript, 2001. - [_An_] Ilya Mironov,
"(Not So) Random Shuffles of RC4 (full version),"
IACR e-print 2002/067.
http://eprint.iacr.org/2002/067/
Key length:
Minimum 8, maximum 2048, multiple of 8 bits; default 128 bits.
Comment:
For the purposes of SCAN, "RC4" will refer to the cipher described in the "RC4 Algorithm revealed" article and inApplied Cryptography, even in the unlikely event that differences are found between that cipher, and RSA Security, Inc.'s proprietary cipher of the same name.
Security comments:
- There are small biases at the start of the RC4 keystream; see the paper by Ilya Mironov, and the security comments forRC4-drop for further discussion.
- The RC4 keystream is distinguishable from random given about 2 Gbytes of the stream.
- RC4 is vulnerable to related-key attacks, and therefore it should only be used with keys that are generated by a strong RNG, or by a source of bits that are sufficiently uncorrelated (such as the output of a hash function).
| RC4-drop[(nbytes)] | Stream Cipher |
|---|
Description:
This algorithm is the same as RC4, except that the first nbytes bytes of keystream are discarded after key scheduling.
Alias:
"MARK-4" is an alias for RC4-drop(256).
References:
- [see references for RC4]
- [_An_] Ilya Mironov,
"(Not So) Random Shuffles of RC4 (full version),"
IACR e-print 2002/106.
http://eprint.iacr.org/2002/106/
Parameters:
Integer nbytes[creation/read, default 768] - the number of bytes to be dropped after key scheduling (minimum 0, maximum 65536)
Key length:
Minimum 8, maximum 2048, multiple of 8 bits; default 128 bits.
Comments:
- For the purposes of SCAN, "RC4-drop" will be based on the "RC4" cipher described in in the "RC4 Algorithm revealed" article and inApplied Cryptography, even in the unlikely event that differences are found between that cipher, and RSA Security, Inc.'s proprietary cipher of the same name.
- The alias "MARK-4" for RC4-drop(256) was apparently suggested by Bryan Olson, in a posting to sci.crypt. In SCAN 1.0.15, "MARK-4" was a standard name rather than an alias; this is technically an incompatible change.
Security comments:
- The RC4 keystream is distinguishable from random given about 2 Gbytes of the stream (independent of how many bytes are dropped).
- The paper by Ilya Mironov says:
Our most conservative recommendation is based on the experimental data on the tail probability of the strong uniform time T (Section 5.5). This means that discarding the initial 12 × 256 bytes most likely eliminates the possibility of a strong attack.
Dumping several times more than 256 bytes from the output stream (twice or three times this number) appears to be just as reasonable a precaution. We recommend doing so in most applications.
I.e. the "most conservative" recommendation is to use RC4-drop(3072), but RC4-drop(768) "appears to be just as reasonable". The latter is the default for this algorithm. - Unmodified RC4 is vulnerable to related-key and other key scheduling attacks. Despite the fact that discarding the first 768 bytes of keystream appears to prevent the known attacks, it is still recommended to use RC4-drop only with keys that are generated by a strong RNG, or by a source of bits that are sufficiently uncorrelated (such as the output of a hash function).
| RC5[(rounds)] | Block Cipher |
|---|
Designer:
Published:
January 1995
Alias:
"RC5-32"
References:
- [_Inf_] Ron Rivest,
"The RC5 Encryption Algorithm,"
Dr. Dobb's Journal, vol. 20 no. 1, pp. 146-148. January 1995. - [_Def_] Ron Rivest,
"The RC5 Encryption Algorithm,"
Revised 20 March 1997.
http://theory.lcs.mit.edu/~rivest/publications.html
(Postscript,PDF,correction note) - [Def, _Test_] Ron Rivest,
"The RC5, RC5-CBC, RC5-CBC-Pad, and RC5-CTS Algorithms,"
RFC 2040, October 1996. - [_Inf_] A. Menezes, P.C. van Oorschot, S.A. Vanstone,
"Section 7.7.2 RC5,"
Handbook of Applied Cryptography, CRC Press, 1997.
http://www.cacr.math.uwaterloo.ca/hac/about/chap7.pdf,.ps - [_Patent_] RSA Security, Inc. (assignee),
"Block Encryption Algorithm with Data-Dependent Rotations,"
U.S. Patent 5,724,428, filed November 1 1995, issued March 3 1998. - [_Patent_] RSA Security, Inc. (assignee),
"Block Encryption Algorithm with Data-Dependent Rotations,"
U.S. Patent 5,835,600, filed April 21 1997, issued November 10 1998. - [_An_] B.S. Kaliski, Y.L. Yin,
"On Differential and Linear Cryptanalysis of the RC5 Encryption Algorithm",
Advances in Cryptology - CRYPTO '95, pp. 171-184. Springer-Verlag, 1995. - [_An_] Lars Knudsen, W. Meier,
"Improved differential attack on RC5,"
Advances in Cryptology - CRYPTO '96 Proceedings, Volume 1109 of Lecture Notes in Computer Science (N. Koblitz, ed.), pp. 216-228. Springer-Verlag, 1996.
ftp://ftp.esat.kuleuven.ac.be/pub/COSIC/knudsen/rc5.ps.Z - [_An_] Howard Heys,
"Linearly Weak Keys of RC5,"
IEE Electronics Letters, vol. 33, no. 10, pp. 836-838, 1997.
http://www.engr.mun.ca/~howard/PAPERS/rc5_letter.ps - [_An_] A. Biryukov, E. Kushilevitz,
"Improved Cryptanalysis of RC5,"
Advances in Cryptology - EuroCrypt '98.
http://www.cs.technion.ac.il/~eyalk/alex.ps.Z - [_An_] A. A. Selcuk,
"New results in linear cryptanalysis of RC5,"
Fast Software Encryption - Fifth International Workshop, Paris, France, LNCS. Springer-Verlag, 1998. - [_An_] Helena Handschuh, Howard Heys
"A Timing Attack on RC5,"
Workshop on Selected Areas in Cryptography - SAC '98, Queen's University, Kingston, Ontario, Aug. 1998.
To be published by Springer-Verlag.
http://www.enst.fr/~handschu/rc5.ps - [_An_] B.S. Kaliski Jr., Y.L. Yin,
"On the Security of the RC5 Encryption Algorithm,"
RSA Laboratories Technical Report TR-602, 1998.
ftp://ftp.rsasecurity.com/pub/rsalabs/rc5/rc5-report.pdf - [_An_] Takeshi Shimoyama, Kiyofumi Takeuchi, Juri Hayakawa,
"Correlation Attack to the Block Cipher RC5 and the Simplified Variants of RC6,"
Presented at the 3rd AES Candidate Conference.
http://csrc.nist.gov/encryption/aes/round2/conf3/papers/36-tshimoyama.pdf - [_An_] Borst, Preneel, Vandewalle,
"Linear cryptanalysis of RC5 and RC6,"
Presented at Fast Software Encryption '99, Rome. - [_An_] John Kelsey, Bruce Schneier, David Wagner,
"Mod n cryptanalysis, with applications against RC5P and M6,"
Presented at Fast Software Encryption '99, Rome.
Parameters:
Integer rounds[creation/read, default 12] - the number of rounds to be performed (minimum 12, multiple of 2)
Key length:
Minimum 0; maximum 2040, multiple of 8 bits; default 128 bits.
Block size:
8 bytes.
Comments:
- The block size could have been specified as a parameter; however it is unlikely that RC5 could be efficiently implemented with multiple block sizes sharing the same code, and therefore two different algorithms are specified (RC5 and RC5-64). Also note that the default (and minimum) number of rounds is different (12 vs 16).
- The maximum key length is restricted to 2040 bits (see theRSA Labs FAQ entry for RC5); this is an incompatible change since SCAN 1.0.11.
Security comment:
The paper "On the Security of the RC5 Encryption Algorithm" cited above gives an overview of cryptanalysis results against RC5 up to 1998.
Patent status:
RC5 and RC5-64 are patented by RSA Security, Inc.
| ? RC5-64[(rounds)] | Block Cipher |
|---|
Designer:
Published:
January 1995
References:
[see references for RC5]
Parameters:
Integer rounds[creation/read, default 16] - the number of rounds to be performed (minimum 16, multiple of 2)
Key length:
Minimum 0; maximum 2040, multiple of 8 bits; default 128 bits.
Block size:
16 bytes.
Missing information:
Test vectors.
Comments:
- The block size could have been specified as a parameter; however it is unlikely that RC5 could be efficiently implemented with multiple block sizes sharing the same code, and therefore two different algorithms are specified (RC5 and RC5-64). Also note that the default (and minimum) number of rounds is different (12 vs 16).
- The maximum key length is restricted to 2040 bits (see theRSA Labs FAQ entry for RC5); this is an incompatible change since SCAN 1.0.11.
Patent status:
RC5 and RC5-64 are patented by RSA Security, Inc.
| RC6[(rounds)] | Block Cipher |
|---|
Designers:
Ron Rivest,Matthew Robshaw,Raymond Sidney,Yiqun Lisa Yin
Published:
1998?
Alias:
"RC6-32"
References:
- [_Def, An_] Ron Rivest, Matthew Robshaw, Raymond Sidney, Yiqun Lisa Yin,
The RC6 Block Cipher,
http://theory.lcs.mit.edu/~rivest/rc6.pdf - [_An_] Ron Rivest,
Further notes on RC6,
http://theory.lcs.mit.edu/~rivest/rc6-notes.txt - [_An_] Scott Contini, Ron Rivest, Matthew Robshaw, Yiqun Lisa Yin,
The Security of RC6,
http://www.rsasecurity.com/rsalabs/aes - [_An_] Scott Contini, Yiqun Lisa Yin,
"On Differential Properties of Data-Dependent Rotations and Their Use in MARS and RC6,"
Presented at the 2nd AES Conference.
http://csrc.nist.gov/encryption/aes/round1/conf2/papers/contini.pdf - [_An_] Markku-Juhani Saarinen,
"A note regarding the hash function use of MARS and RC6,"
http://www.cc.jyu.fi/~mjos/sshnote.pdf - [_An_] Willi Meier, Lars Knudsen,
"Correlations in RC6,"
July 29, 1999.
http://www.ii.uib.no/~larsr/papers/rc6.ps or http://csrc.nist.gov/encryption/aes/round2/comments/19990812-lknudsen.pdf - [_An_] Takeshi Shimoyama, Kiyofumi Takeuchi, Juri Hayakawa,
"Correlation Attack to the Block Cipher RC5 and the Simplified Variants of RC6,"
Presented at the 3rd AES Candidate Conference.
http://csrc.nist.gov/encryption/aes/round2/conf3/papers/36-tshimoyama.pdf - [_An_] Contini, Rivest, Robshaw, Yin,
"Improved analysis of some simplified variants of RC6,"
Presented at Fast Software Encryption '99, Rome. - [_An_] Borst, Preneel, Vandewalle,
"Linear cryptanalysis of RC5 and RC6,"
Presented at Fast Software Encryption '99, Rome. - [_An_] Henri Gilbert, Helena Handschuh, Antoine Joux, Serge Vaudenay,
"A Statistical Attack on RC6,"
Presented at Fast Software Encryption 2000, New York. - [_An_] Tetsu Iwata, Kaoru Kurosawa,
"On the Pseudorandomness of AES Finalists - RC6, Serpent, MARS and Twofish,"
Presented at Fast Software Encryption 2000, New York. - [_Patent_] RSA Security, Inc. (assignee),
"Block Encryption Algorithm with Data-Dependent Rotations,"
U.S. Patent 5,724,428, filed November 1 1995, issued March 3 1998. - [_Patent_] RSA Security, Inc. (assignee),
"Block Encryption Algorithm with Data-Dependent Rotations,"
U.S. Patent 5,835,600, filed April 21 1997, issued November 10 1998. - [_Patent_] RSA Security, Inc. (assignee),
"Enhanced Block Encryption Algorithm with Data-Dependent Rotations,"
U.S. Patent Application 09/094,649. Filed June 15, 1998. - [_Test_] NIST,
RC6 Test Values,
http://www-08.nist.gov/encryption/aes/round1/testvals/rc6-vals.zip
Parameters:
Integer rounds[creation/read, default 20] - the number of rounds to be performed (minimum 8, multiple of 4)
Key length:
Minimum 0; maximum 2040, multiple of 8 bits; default 128 bits.
Block size:
16 bytes.
Comments:
The block size could have been specified as a parameter; however it is unlikely that RC6 could be efficiently implemented with multiple block sizes sharing the same code, and therefore two different algorithms are specified (RC6 and RC6-64).
Patent status:
RSA Security, Inc., has several patents pending on RC6 (covering all versions).
| ? RC6-64[(rounds)] | Block Cipher |
|---|
Designers:
Ron Rivest,Matthew Robshaw,Raymond Sidney,Yiqun Lisa Yin
Published:
1998?
References:
[see references for RC6]
Parameters:
Integer rounds[creation/read, default 20] - the number of rounds to be performed (minimum 8, multiple of 4)
Key length:
Minimum 0; maximum 2040, multiple of 8 bits; default 128 bits.
Block size:
32 bytes.
Missing information:
Test vectors.
Comments:
The block size could have been specified as a parameter; however it is unlikely that RC6 could be efficiently implemented with multiple block sizes sharing the same code, and therefore two different algorithms are specified (RC6 and RC6-64).
Patent status:
RSA Security, Inc., has several patents pending on RC6 (covering all versions).
Designers:
Published:
November 1998
Description:
This is Rijndael with a 128-bit block size. The number of rounds is 6 + max(Nk, Nb), where Nb = 4, and Nk is the number of 32-bit words in the key.
References:
- [_Def, An_] Joan Daemen, Vincent Rijmen,
AES Proposal: Rijndael (corrected version),
http://www.esat.kuleuven.ac.be/~rijmen/rijndael/rijndaeldocV2.zip - [_An_] Joan Daemen, Vincent Rijmen,
Annex to AES Proposal: Rijndael,
http://www.esat.kuleuven.ac.be/~rijmen/rijndael/PropCorr.PDF - [_An_] Stefan Lucks,
"Attacking Seven Rounds of Rijndael under 192-bit and 256-bit Keys,"
Presented at the 3rd AES Candidate Conference.
http://csrc.nist.gov/encryption/aes/round2/conf3/papers/04-slucks.pdf - [_An_] Henri Gilbert, Marine Minier,
"A collision attack on 7 rounds of Rijndael,"
Presented at the 3rd AES Candidate Conference.
http://csrc.nist.gov/encryption/aes/round2/conf3/papers/11-hgilbert.pdf - [_An_] Makoto Sugita, Kazukuni Kobara, Kazuhiro Uehara, Shuji Kubota, Hideki Imai,
"Relationships among Differential, Truncated Differential, Impossible Differential Cryptanalyses against Word-Oriented Block Ciphers like Rijndael, E2,"
Presented at the 3rd AES Candidate Conference.
http://csrc.nist.gov/encryption/aes/round2/conf3/papers/32-msugita.pdf - [_An_] Eli Biham, Nathan Keller,
"Cryptanalysis of Reduced Variants of Rijndael,"
Presented at the 3rd AES Candidate Conference.
http://csrc.nist.gov/encryption/aes/round2/conf3/papers/35-ebiham.pdf - [_An_] Niels Ferguson, John Kelsey, Stefan Lucks, Bruce Schneier, Mike Stay, David Wagner, Doug Whiting,
"Improved Cryptanalysis of Rijndael,"
Proceedings of FSE 2000.
http://www.counterpane.com/rijndael.html - [_An_] Sean Murphy, Matt Robshaw,
"New observations on Rijndael,"
August 7, 2000.
http://www.isg.rhbnc.ac.uk/~mrobshaw/rijndael.html
http://www.cs.rhbnc.ac.uk/~sean/ - [_An_] Joan Daemen, Vincent Rijmen,
"Answer to 'new observations on Rijndael',"
http://www.esat.kuleuven.ac.be/~rijmen/rijndael/answer.pdf - [_An_] Sean Murphy, Matt Robshaw,
"Further Comments on the Structure of Rijndael,"
http://www.cs.rhbnc.ac.uk/~sean/ - [_An_] Joan Daemen, Vincent Rijmen,
"The AES second round Comments of the Rijndael Team,"
Submitted to NIST as an AES comment, May 2000.
http://csrc.nist.gov/encryption/aes/round2/comments/20000512-jdaemen.pdf - [_An_] F. Koeune, J.-J. Quisquater,
"A timing attack against Rijndael,"
UCL/DICE Crypto Group Technical Report CG-1999/1.
http://www.dice.ucl.ac.be/crypto/techreports.html#1999 - [_An_] L. Keliher, I. Meijer, S. Tavares,
"Improving the upper bound on the maximum average linear hull probability for Rijndael,"
To be presented at Selected Areas in Cryptography 2001, Toronto, Ontario, Canada. - [_An_] Niels Ferguson, Richard Schroeppel, Doug Whiting,
"A simple algebraic representation of Rijndael,"
To be presented at Selected Areas in Cryptography 2001, Toronto, Ontario, Canada.
Draft at http://www.xs4all.nl/~vorpal/pubs/rdalgeq.html - Nicolas Courtois, Josef Pieprzyk,
"Cryptanalysis of Block Ciphers with Overdefined Systems of Equations,"
IACR e-print 2002/044, 23 July 2002.
http://eprint.iacr.org/2002/044/ - Eric Filiol,
"A New Statistical Testing for Symmetric Ciphers and Hash Functions,"
IACR e-print 2002/099, 23 July 2002.
http://eprint.iacr.org/2002/099/ - [_An_] Joanne Fuller, William Millan,
"On Linear Redundancy in the AES S-Box,"
IACR e-print 2002/111, 5 August 2002.
http://eprint.iacr.org/2002/111/ - [_An_] Sean Murphy, Matt Robshaw,
"Essential Algebraic Structure within the AES,"
June 5, 2002.
http://www.isg.rhbnc.ac.uk/~mrobshaw/rijndael.html - [_An_] R. Wernsdorf,
"The round functions of Rijndael generate the alternating group,"
In Proceedings of Fast Software Encryption (Vincent Rijmen, ed.) LNCS, Springer-Verlag, to appear. - [_Inf_] www.minrank.org,
The XSL attack on AES/Rijndael (collection of links to relevant papers),
http://www.minrank.org/aes/ - [_Inf, Test_] Joan Daemen, Vincent Rijmen,
The Rijndael Page,
http://www.esat.kuleuven.ac.be/~rijmen/rijndael/ - [_Test_] NIST,
Rijndael Test Values,
http://www-08.nist.gov/encryption/aes/round1/testvals/rijndael-vals.zip - [_Test_] Brian Gladman,
aesdvec.zip(Rijndael test vectors for all block and key sizes),
http://fp.gladman.plus.com/cryptography_technology/rijndael/
Key length:
Minimum 128, maximum 256, multiple of 32 bits; default 128 bits.
Block size:
16 bytes.
Comments:
- The range of specified key lengths has been extended since SCAN 1.0.12 (which only specified 128, 192 and 256 bits). This is an incompatible change for the key lengths that were not previously supported.
- Rijndael is pronounced approximately as "Rhine-dahl".
| Rijndael-160 | Block Cipher |
|---|
Designers:
Published:
November 1998
Description:
This is Rijndael with a 160-bit block size. The number of rounds is 6 + max(Nk, Nb), where Nb = 5, and Nk is the number of 32-bit words in the key.
References:
[see references for Rijndael]
Key length:
Minimum 128, maximum 256, multiple of 32 bits; default 128 bits.
Block size:
20 bytes.
Comments:
[see comments for Rijndael]
| Rijndael-192 | Block Cipher |
|---|
Designers:
Published:
November 1998
Description:
This is Rijndael with a 192-bit block size. The number of rounds is 6 + max(Nk, Nb), where Nb = 6, and Nk is the number of 32-bit words in the key.
References:
[see references for Rijndael]
Key length:
Minimum 128, maximum 256, multiple of 32 bits; default 128 bits.
Block size:
24 bytes.
Comments:
[see comments for Rijndael]
| Rijndael-224 | Block Cipher |
|---|
Designers:
Published:
November 1998
Description:
This is Rijndael with a 224-bit block size. The number of rounds is 6 + max(Nk, Nb), where Nb = 7, and Nk is the number of 32-bit words in the key.
References:
[see references for Rijndael]
Key length:
Minimum 128, maximum 256, multiple of 32 bits; default 128 bits.
Block size:
28 bytes.
Comments:
[see comments for Rijndael]
| Rijndael-256 | Block Cipher |
|---|
Designers:
Published:
November 1998
Description:
This is Rijndael with a 256-bit block size. The number of rounds is always 14.
References:
[see references for Rijndael]
Key length:
Minimum 128, maximum 256, multiple of 32 bits; default 128 bits.
Block size:
32 bytes.
Comments:
[see comments for Rijndael]
| SAFER-K[(rounds)] | Block Cipher |
|---|
Designer:
James Massey
Published:
December 1993.
Description:
This algorithm refers to the original version of SAFER, designed in 1993.
References:
- [_Def_] Massey, J. L.,
"SAFER K-64: A Byte-Oriented Block Ciphering Algorithm",
Fast Software Encryption (Ross Anderson, ed.), Proceedings of the Cambridge Security Workshop, Cambridge, U.K., December 9-11, 1993, pp. 1-17.
Volume 809 of Lecture Notes in Computer Science, Springer, 1994. - [_Inf_] Massey, J. L.,
"SAFER K-64: One Year Later",
Preliminary manuscript of a paper presented at the K. U. Leuven Workshop on Cryptographic Algorithms, December 14-16, 1994.
To be published in the Proceedings of this workshop by Springer. - [_Inf_] A. Menezes, P.C. van Oorschot, S.A. Vanstone,
"Section 7.7.1 SAFER,"
Handbook of Applied Cryptography, CRC Press, 1997.
http://www.cacr.math.uwaterloo.ca/hac/about/chap7.pdf,.ps - [_Inf, Test, Impl_] Richard De Moliner,
SAFER toolkit V1.2. Includes C implementation, additional notes, test data, test program.
ftp://ftp.isi.ee.ethz.ch/pub/simpl/safer.V1.2.tar.Z - [_An_] Lars Knudsen,
"A Key-Schedule Weakness in SAFER K-64",
Advances in Cryptology - CRYPTO '95 Proceedings, Volume 963 of Lecture Notes in Computer Science, Springer-Verlag, 1995.
ftp://ftp.esat.kuleuven.ac.be/pub/COSIC/knudsen/saferkey.ps.Z
(appendix with corrections: ftp://ftp.esat.kuleuven.ac.be/pub/COSIC/knudsen/tillaeg.ps.Z) - [_An_] John Kelsey, Bruce Schneier, David Wagner,
"Key-Schedule Cryptanalysis of 3-WAY, IDEA, G-DES, RC4, SAFER, and Triple-DES".
http://www.counterpane.com/key_schedule.html - [also see cryptanalysis references for SAFER-SK]
Parameters:
Integer rounds[creation/read, default null (indicating key-length-dependent)] - the number of rounds to be performed (minimum 6). When the value of this property is null, 6 rounds are used for a 64-bit key, and 10 rounds for a 128-bit key.
Key length:
64 or 128 bits; default 128 bits.
Block size:
8 bytes.
Comment:
Conventionally, the key length for SAFER is included in the algorithm name, e.g. "SAFER K-64", "SAFER K-128", etc. Because a SCAN algorithm may have variable-length keys, all of these are referred to as "SAFER-K".
Security comment:
As a result of the key schedule attack by Lars Knudsen cited above, SAFER-K has been superceded by SAFER-SK.
| SAFER-SK[(rounds)] | Block Cipher |
|---|
Designer:
James Massey
Published:
September 1995.
Description:
This algorithm refers to the version of SAFER with a strengthened key schedule, designed in 1995 (see SAFER_SK.TXT, cited below).
Alias:
"OpenPGP.Cipher.6" for SAFER-SK(13).
References:
- [Def (excluding key schedule)] Massey, J. L.,
"SAFER K-64: A Byte-Oriented Block Ciphering Algorithm",
Fast Software Encryption (Ross Anderson, ed.), Proceedings of the Cambridge Security Workshop, Cambridge, U.K., December 9-11, 1993, pp. 1-17.
Volume 809 of Lecture Notes in Computer Science, Springer, 1994. - [_Def_] Massey, J. L.,
"Announcement of a Strengthened Key Schedule for the Cipher SAFER",
September 9, 1995, (see file 'SAFER_SK.TXT' included in the SAFER toolkit, below). - [_Inf, Test, Impl_] Richard De Moliner,
SAFER toolkit V1.2. Includes C implementation, additional notes, test data, test program.
ftp://ftp.isi.ee.ethz.ch/pub/simpl/safer.V1.2.tar.Z - [_An_] C. Harpes,
"A Generalization of Linear Cryptanalysis Applied to SAFER,"
Internal report, Signal and Information Processing Lab., Swiss Federal Institute of Technology, Zurich, March 9, 1995.
http://www.isi.ee.ethz.ch/~harpes/GLCsafer.ps - [_An_] Serge Vaudenay,
"On the need for multipermutations: cryptanalysis of MD4 and SAFER,"
Fast Software Encryption, Leuven Workshop, Volume 1008 of Lecture Notes in Computer Science, pp. 286-297. Springer-Verlag, 1995. - [_An_] Lars Knudsen, T.A. Berson,
"Truncated differentials of SAFER,"
Fast Software Encryption, Volume 1039 of Lecture Notes in Computer Science (D. Gollmann, ed.), pp. 15-26. Springer-Verlag, 1996.
ftp://ftp.esat.kuleuven.ac.be/pub/COSIC/knudsen/trunc_dif_saf.ps.Z - [_An_] John Kelsey, Bruce Schneier, David Wagner,
"Key-Schedule Cryptanalysis of 3-WAY, IDEA, G-DES, RC4, SAFER, and Triple-DES".
http://www.counterpane.com/key_schedule.html - [_An_] Jorge Nakahara Jr., Bart Preneel, Joos Vandewalle,
"Linear Cryptanalysis of Reduced-Round Versions of the SAFER Block Cipher Family,"
Presented at Fast Software Encryption 2000, New York.
Parameters:
Integer rounds[creation/read, default null (indicating key-length-dependent)] - the number of rounds to be performed (minimum 8). When the value of this property is null, 8 rounds are used for a 64-bit key, and 10 rounds for a 128-bit key.
Key length:
64 or 128 bits; default 128 bits.
Block size:
8 bytes.
Comments:
- Conventionally, the key length for SAFER with strengthened key schedule is included in the algorithm name, e.g. "SAFER SK-64", "SAFER SK-128", etc. Because a SCAN algorithm may have variable-length keys, all of these are referred to as "SAFER-SK".
- SAFER_SK.TXT suggests a maximum of 10 rounds for a 64-bit key, and 12 rounds for a 128-bit key; however here we do not specify any limit on the number of rounds. Also note that because the number of rounds can be given in the algorithm name before the key length is known, it is possible to use a 128-bit key with 8 or 9 rounds (i.e. less than the default), but this is definitely not recommended.
- A 40-bit key schedule has also been specified for SAFER-SK; this is not required to be implemented, and application designers should not assume that a SAFER-SK implementation will support 40-bit keys.
Designers:
James Massey, Gurgen Khachatrian, Melsik Kuregian
Description:
This is the original SAFER+ cipher submitted as a first round AES candidate (not the "tweaked" version).
Aliases:
- "SAFERp1" (use for identifiers)
- "SAFER+-1"
References:
- [_Def, An_] Prof. James Massey, Prof. Gurgen Khachatrian, Dr. Melsik Kuregian,
Nomination of SAFER+ as Candidate Algorithm for the Advanced Encryption Standard (AES),
http://www.cylink.com/library2/downloadbody.htm
(but link appears to be broken) - [_An_] Prof. James Massey,
"On the Optimality of SAFER+ Diffusion,"
Presented at the 2nd AES Conference.
http://csrc.nist.gov/encryption/aes/round1/conf2/papers/massey.pdf - [_An_] John Kelsey, Bruce Schneier, David Wagner,
"Key Schedule Weaknesses in SAFER+,"
Presented at the 2nd AES Conference.
http://csrc.nist.gov/encryption/aes/round1/conf2/papers/kelsey.pdf - [_Test_] NIST,
SAFER+ Test Values,
http://www-08.nist.gov/encryption/aes/round1/testvals/saferpls-vals.zip - [also see cryptanalysis references for SAFER++]
Key length:
128, 192 or 256 bits; default 128 bits.
Block size:
16 bytes.
Comments:
- The original C reference code uses an unconventional byte order when printing test vectors (the order of bytes is reversed across the whole block). The correct byte order is that defined by the Java reference implementation, and by the NIST test vectors referenced above.
- The "tweaked" version of SAFER+, which was included in SCAN 1.0.13 under the name "SAFER+-2", is no longer included because it has no well-defined test vectors, and has been obsoleted by SAFER++. This is an incompatible change.
Security comment:
The paper "Key Schedule Weaknesses in SAFER+," describes some certificational weaknesses (meet-in-the-middle attacks) for SAFER+ with key sizes of 192 and 256 bits. These are claimed to be corrected by the modified key schedule used in <SAFER++>.
Designers:
James Massey, Gurgen Khachatrian, Melsik Kuregian
Published:
November 2000
Alias:
"SAFERpp" (use for identifiers)
Description:
This is the variant of SAFER++ with a 128-bit block size.
References:
- [_Def, An, Test_] James Massey, Gurgen Khachatrian, Melsik Kuregian,
"Nomination of SAFER++ as Candidate Algorithm for the New European Schemes for Signatures, Integrity, and Encryption (NESSIE),"
Presented at the First Open NESSIE Workshop, November 2000.
https://www.cosic.esat.kuleuven.ac.be/nessie/workshop/submissions/safer++.zip - [_An_] Prof. James Massey,
"On the Optimality of SAFER+ Diffusion,"
Presented at the 2nd AES Conference.
http://csrc.nist.gov/encryption/aes/round1/conf2/papers/massey.pdf
(This applies to SAFER+, but the diffusion properties of SAFER++ are similar.) - [_An_] Jorge Nakahara Jr., Bart Preneel, Joos Vandewalle,
"Linear Cryptanalysis of Reduced-Round Versions of the SAFER Block Cipher Family,"
Presented at Fast Software Encryption 2000, New York.
http://www.esat.kuleuven.ac.be/~nakahara/safer.ps.gz - [_An_] Bart van Rompey, Vincent Rijmen, Jorge Nakahara Jr.,
"A First Report on CS-Cipher, Hierocrypt, Grand Cru, SAFER++ and SHACAL,"
NESSIE Project public report, March 12, 2001.
https://www.cosic.esat.kuleuven.ac.be/nessie/reports/kulwp3-006-1.pdf - [_An_] Jorge Nakahara Jr., Bart Preneel, Joos Vandewalle,
"Linear Cryptanalysis of Reduced-Round SAFER++,"
Second NESSIE Workshop, September 12-13, 2001. http://www.esat.kuleuven.ac.be/~nakahara/spp.ps.gz
Key length:
128 or 256 bits; default 128 bits.
Block size:
16 bytes.
Designers:
James Massey, Gurgen Khachatrian, Melsik Kuregian
Published:
November 2000
Alias:
"SAFERpp64" (use for identifiers)
Description:
This is the "legacy" variant of SAFER++, with a 64-bit block size and 128-bit key.
References:
[see references for SAFER++]
Key length:
128 bits.
Block size:
8 bytes.
| Sapphire-II | Stream Cipher |
|---|
Designer:
Michael Paul Johnson
Published:
January? 1995
References:
- [_Def_] Michael Paul Johnson,
"The Sapphire II Stream Cipher,"sapphire.{ps,txt,doc}in ftp://ftp.zedz.com/pub/crypto/libraries/sapphire/sapphire.zip - [_Impl_] Michael Paul Johnson,
Sapphire II reference implementation (in C++),
ftp://ftp.zedz.com/pub/crypto/libraries/sapphire/sapphire.zip
Key length:
Minimum 8, maximum 2040, multiple of 8 bits; default 128 bits.
Missing information:
Test vectors.
Designers:
Ran Canetti, Don Coppersmith, Rosario Gennaro, Shai Halevi, Nick Howgrave-Graham, Charanjit Jutla, Tal Rabin, J. R. Rao
Published:
February 2002
References:
- [_Def, Test_] Don Coppersmith, Shai Halevi, Charanjit Jutla,
"Scream: a software-efficient stream cipher" (revised 25 February 2002).
http://eprint.iacr.org/2002/019/ - [_An_] Don Coppersmith, Shai Halevi, Charanjit Jutla,
"Cryptanalysis of stream ciphers with linear masking." http://eprint.iacr.org/2002/020/
Key length:
128 bits.
Designers:
Ran Canetti, Don Coppersmith, Rosario Gennaro, Shai Halevi, Nick Howgrave-Graham, Charanjit Jutla, Tal Rabin, J. R. Rao
Published:
February 2002
References:
[see references for Scream]
Key length:
128 bits.
| SEAL-3.0-BE[(Lbytes)] | Stream Cipher |
|---|
Designers:
Phillip Rogaway, Don Coppersmith
Published:
September 1997
Alias:
"SEALv3BE" (use for identifiers)
Description:
This is version 3.0 of SEAL, using big-endian byte order when XORing the keystream with the plaintext for encryption. See the Comment section below.
References:
- [_Def, Test_] P. Rogaway, D. Coppersmith,
"A Software-Optimized Encryption Algorithm," (revised September 1997).
http://www.cs.ucdavis.edu/~rogaway/papers/seal-abstract.html - [_Inf_] Bruce Schneier,
"Section 17.2 SEAL,"
Applied Cryptography, Second Edition, John Wiley & Sons, 1996. - [_Inf_] A. Menezes, P.C. van Oorschot, S.A. Vanstone,
"Section 6.4.1 SEAL,"
Handbook of Applied Cryptography, CRC Press, 1997.
http://www.cacr.math.uwaterloo.ca/hac/about/chap6.pdf,.ps - [_Patent_] P. Rogaway, D. Coppersmith,
"Software-efficient pseudorandom function and the use thereof for encryption,"
U.S. Patent 5,454,039, filed December 6 1993, issued September 26 1995. - [_Patent_] P. Rogaway, D. Coppersmith,
"Software-efficient pseudorandom function and the use thereof for encryption,"
U.S. Patent 5,675,652, filed June 7 1995, issued October 7 1997. - [_An_] Helena Handschuh, Henri Gilbert,
" 2 Cryptanalysis of the SEAL Encryption Algorithm,"
2 Cryptanalysis of the SEAL Encryption Algorithm,"
Fast Software Encryption - FSE4, Volume 1267 of Lecture Notes in Computer Science, pp. 1-12, 1997.
http://www.enst.fr/~handschu/seal.ps - [_An_] Scott Fluhrer,
"Cryptanalysis of the SEAL 3.0 pseudorandom function family,"
In Proceedings of the Fast Software Encryption Workshop (FSE '01), 2001.
Parameters:
Integer Lbytes[creation/read, default 4096] - the number of bytes of output generated for each position index (minimum 32, maximum 65536, multiple of 32). This is equal to L/8 where L is as defined in the SEAL paper.
Key length:
160 bits.
Comments:
- The internal operation of SEAL is endian-neutral, and is intentionally left unspecified in the paper "A software-optimized encryption algorithm." We therefore define two different algorithm names: SEAL-3.0-BE for big-endian operation, and SEAL-3.0-LE for little-endian operation.
Note that big-endian order is consistent with SHA-1 (which is used by the SEAL key scheduling algorithm), with common practice for Internet protocols, and with Wei Dai's Crypto++ library. For some applications these considerations may be outweighed by speed on little-endian processors (or as suggested by Rogaway and Coppersmith, the ciphertext could be labelled with the byte-order that has been used). - The Lbytes parameter was added in SCAN 1.0.13.
Security comment:
Note that the paper by Handschuh and Gilbert cryptanalyses SEAL 1.0 or 2.0 (which do not have SCAN algorithm names). SEAL 3.0 has been designed to prevent the attack described in that paper. The attack by Scott Fluhrer distinguishes the output stream from random after about 244 bytes.
Patent status:
SEAL is patented in the United States by IBM.
| SEAL-3.0-LE | Stream Cipher |
|---|
Designers:
Phillip Rogaway, Don Coppersmith
Published:
September 1997
Alias:
"SEALv3LE" (use for identifiers)
Description:
This is version 3.0 of SEAL, using little-endian byte order when XORing the keystream with the plaintext for encryption. See the Comment section for<SEAL-3.0-BE>.
References:
[see references for SEAL-3.0-BE]
Parameters:
Integer Lbytes[creation/read, default 4096] - the number of bytes of output generated for each position index (minimum 32, maximum 65536, multiple of 32). This is equal to L/8 where L is as defined in the SEAL paper.
Key length:
160 bits.
Comment:
[see comment for SEAL-3.0-BE]
Patent status:
[see patent status for SEAL-3.0-BE]
Designers:
Ross Anderson,Eli Biham,Lars Knudsen
Published:
1998?
References:
- [_Def, An_] Ross Anderson, Eli Biham, Lars Knudsen,
Serpent: A Proposal for the Advanced Encryption Standard,
http://www.cl.cam.ac.uk/ftp/users/rja14/serpent.pdf - [_Inf_] Ross Anderson,
Serpent home page,
http://www.cl.cam.ac.uk/~rja14/serpent.html - [_Inf_] Eli Biham,
Serpent page at Technion University,
http://www.cs.technion.ac.il/~biham/Reports/Serpent/ - [_Inf_] Dag Arne Osvik,
"Speeding up Serpent,"
March 13, 2000. Presented at the 3nd AES Candidate Conference.
http://csrc.nist.gov/encryption/aes/round2/conf3/papers/26-daosvik.pdf - [_Inf_] Jun Yajima, Masahiko Takenaka, Naoya Torii, Kouichi Itoh,
"Results of New Boolean Functions Search for Serpent S-boxes,"
Submitted to NIST as an AES comment, May 2000.
http://csrc.nist.gov/encryption/aes/round2/comments/20000511-jyajima.pdf - [_An_] Orr Dunkelman,
"An Analysis of Serpent-p and Serpent-p-ns,"
2nd AES Conference.
http://csrc.nist.gov/encryption/aes/round1/conf2/papers/dunkelman.pdf - [_An_] T. Shimoyama,
"The nonlinear order of the Serpent S-boxes,"
Presented at the recent result session of AES2. - [_An_] John Kelsey, Tadayoshi Kohno, Bruce Schneier,
"Preliminary Cryptanalysis of Reduced-Round Serpent,"
3rd AES Candidate Conference, 2000.
http://www.counterpane.com/serpent-aes.html - [_An_] Tetsu Iwata, Kaoru Kurosawa,
"On the Pseudorandomness of AES Finalists - RC6, Serpent, MARS and Twofish,"
Presented at Fast Software Encryption 2000, New York. - [_An_] Joan Daemen, Michael Peeters, Gilles Van Assche,
"Bitslice Ciphers and Power Analysis Attacks,"
Presented at Fast Software Encryption 2000, New York. - [_An_] Ralph Wernsdorf,
"The Round Functions of SERPENT Generate the Alternating Group,"
Submitted to NIST as an AES comment, May 2000
http://csrc.nist.gov/encryption/aes/round2/comments/20000512-rwernsdorf.pdf - [_An_] John Kelsey, Tadayoshi Kohno, Bruce Schneier,
"Amplified Boomerang Attacks Against Reduced-Round MARS and Serpent,"
Presented at Fast Software Encryption 2000, New York.
http://www.counterpane.com/boomerang.html - [_Patent_] Ross Anderson, Eli Biham, Lars Knudsen,
"Fast Block Cipher,"
U.K. Patent Application 9722798.9. Filed October 30, 1997. - [_Impl_] Frank Stajano, Markus Kuhn,
Serpent reference implementations (in C, Python and Ada),
http://www.cl.cam.ac.uk/~rja14/serpent.html - [_Test_] NIST,
Serpent Test Values,
http://www-08.nist.gov/encryption/aes/round1/testvals/serpent-vals.zip
Key length:
Minimum 0, maximum 256, multiple of 8 bits; default 128 bits.
Block size:
16 bytes.
Comments:
- The original C reference code uses an unconventional byte order when printing test vectors (the order of bytes is reversed across the whole block). The correct byte order is that defined by the Java reference implementation, and by the NIST test vectors referenced above (i.e. little-endian order).
- The range of specified key lengths has been extended since SCAN 1.0.12 (which only specified 128, 192 and 256 bits). This is an incompatible change for the key lengths that were not previously supported.
- [[need to list implementations that use reversed order?]]
Patent status:
A patent has been applied for on Serpent (see references). However, quoting from the Serpent home page:
Serpent is now completely in the public domain, and we impose no restrictions on its use. This was announced on the 21st August 1998 at the AES conference.
Designers:
Vincent Rijmen,Joan Daemen,Bart Preneel Antoon Bosselaers,Erik De Win
Designers:
This is the "Affine Transformation" variant of SHARK.
References:
- [_Def, An_] Vincent Rijmen, Joan Daemen, Bart Preneel, Antoon Bosselaers, Erik De Win,
"The Cipher SHARK,"
ftp://ftp.esat.kuleuven.ac.be/pub/COSIC/rijmen/shark/paper.ps - [_Impl_] Vincent Rijmen, Joan Daemen, Bart Preneel, Antoon Bosselaers, Erik De Win,
SHARK reference implementation (in C),
ftp://ftp.esat.kuleuven.ac.be/pub/COSIC/rijmen/shark/ - [_An_] Thomas Jakobsen, Lars Knudsen,
"The Interpolation Attack on Block Ciphers,"
Proceedings of Fast Software Encryption '97.
ftp://ftp.esat.kuleuven.ac.be/pub/COSIC/knudsen/interpol.ps
Key length:
128 bits.
Block size:
8 bytes.
Missing information:
Test vectors.
Security comment:
"The Interpolation Attack on Block Ciphers" analyses a "variant of SHARK, which deviates only slightly from the proposed SHARK", reduced to 5 rounds. SHARK normally has 6 rounds.
Designers:
Vincent Rijmen,Joan Daemen,Bart Preneel Antoon Bosselaers,Erik De Win
Designers:
This is the "Exor" variant of SHARK.
References:
- [_Def, An_] Vincent Rijmen, Joan Daemen, Bart Preneel, Antoon Bosselaers, Erik De Win,
"The Cipher SHARK,"
ftp://ftp.esat.kuleuven.ac.be/pub/COSIC/rijmen/shark/paper.ps - [_Impl_] Vincent Rijmen, Joan Daemen, Bart Preneel, Antoon Bosselaers, Erik De Win,
SHARK reference implementation (in C),
ftp://ftp.esat.kuleuven.ac.be/pub/COSIC/rijmen/shark/ - [_An_] Thomas Jakobsen, Lars Knudsen,
"The Interpolation Attack on Block Ciphers,"
Proceedings of Fast Software Encryption '97.
ftp://ftp.esat.kuleuven.ac.be/pub/COSIC/knudsen/interpol.ps - [_Test_] Wei Dai,
Crypto++ 3.0, file sharkval.dat
http://www.eskimo.com/~weidai/cryptlib.html
Key length:
128 bits.
Block size:
8 bytes.
Security comment:
"The Interpolation Attack on Block Ciphers" analyses a "variant of SHARK, which deviates only slightly from the proposed SHARK", reduced to 5 rounds. SHARK normally has 6 rounds.
Designer:
Published:
June 1998
References:
- [Def, _Test_] U.S. National Institute of Standards and Technology,
SKIPJACK and KEA Specifications, May 1998.
http://csrc.nist.gov/encryption/skipjack/skipjack.pdf
HTML version (test vectors corrected 10 February 1999). - [_An_] Eli Biham, Alex Biryukov, Orr Dunkelman, Eran Richardson, Adi Shamir,
"Observations on the SkipJack Encryption Algorithm,"
http://www.cs.technion.ac.il/~biham/Reports/SkipJack/ - [_An_] Eli Biham, Alex Biryukov, Orr Dunkelman, Eran Richardson, Adi Shamir,
"Cryptanalysis of Skipjack Reduced to 31 Rounds using Impossible Differentials,"
http://www.cs.technion.ac.il/users/wwwb/cgi-bin/tr-get.cgi/1998/CS/CS0947.ps - [_An_] Lars R. Knudsen, M.J.B. Robshaw, David Wagner,
"Truncated differentials and Skipjack,"
Proceedings of CRYPTO '99.
http://www.cs.berkeley.edu/~daw/papers/skipjack-crypto99.ps - [_An_] Louis Granboulan,
"Flaws in differential cryptanalysis of Skipjack,"
In Proceedings of Fast Software Encryption: 8th International Workshop, Yokohama, Japan, 2-4 April 2001. To appear in Lecture Notes in Computer Science, Springer-Verlag.
http://www.di.ens.fr/~granboul/recherche/publications/
Key length:
80 bits.
Block size:
8 bytes.
Security comment:
The "Observations on the SkipJack Encryption Algorithm" pages cited above describe the following attack, among others:
This note summarizes our first week of analysis. The main result is an attack on a variant, which we call SkipJack-3XOR (SkipJack minus 3 XORs). The only difference between SkipJack and SkipJack-3XOR is the removal of 3 out of the 320 XOR operations. The attack uses the ciphertexts derived from about 500 plaintexts which are identical except for the second 16 bit word. Its total running time is equivalent to about one million SkipJack encryptions, which can be carried out in seconds on a personal computer.
This is still a preliminary result, but it reiterates our earlier comment that SkipJack does not have a conservative design with a large margin of safety.
Designer:
?
Published:
November 2000
References:
- [_Def, An_] ?
- [_Inf, Impl, Test_] Patrick Ekdahl,
SNOW Home Page,
http://www.it.lth.se/cryptology/snow/ - [_An_] ?
Key length:
Minimum ?, maximum ?, multiple of ? bits; default 128 bits.
Designer:
?
Published:
November 2000
References:
- [_Def, An_] ?
- [_Inf, Impl, Test_] QUALCOMM Australia,
SOBER Reference implementation and test vectors,
http://www.home.aone.net.au/qualcomm/ - [_An_] ?
Key length:
Minimum ?, maximum ?, multiple of ? bits; default 128 bits.
Designer:
?
Published:
November 2000
References:
[see references for SOBER-t16]
Key length:
Minimum ?, maximum ?, multiple of ? bits; default 128 bits.
| SPEED-64[(rounds)] | Block Cipher |
|---|
Designer:
Published:
February 1997
References:
- [_Def, An_] Yuliang Zheng,
"The SPEED Cipher,"
Proceedings of Financial Cryptography - First International Conference FC'97, Volume 1318 of Lecture Notes in Computer Science, pp. 71-89. Springer-Verlag.
Available from http://www.sis.uncc.edu/~yzheng/src/ - [_Inf, Impl, Test_] Yuliang Zheng,
SPEED reference implementation (in C),
Available from http://www.sis.uncc.edu/~yzheng/src/ - [_An_] Chris Hall, John Kelsey, Bruce Schneier, David Wagner,
"Cryptanalysis of SPEED",
Fifth Annual Workshop on Selected Areas in Cryptography, Springer-Verlag, August 1998.
http://www.counterpane.com/speed-sac.html
Parameters:
Integer rounds[creation/read, default 64] - the number of rounds to be performed (minimum 64, multiple of 4)
Key length:
Minimum 48, maximum 256, multiple of 16 bits; default 128 bits.
Block size:
8 bytes.
Security comment:
The "Cryptanalysis of SPEED" paper cited above breaks a reduced round variant of SPEED with 28 rounds, using 231 chosen plaintexts, and argues that variants of SPEED with sufficient rounds to resist the attacks given in the paper, are slower than many other ciphers with comparable security.
| SPEED-128[(rounds)] | Block Cipher |
|---|
Designer:
Published:
February 1997
References:
[see references for SPEED-64]
Parameters:
Integer rounds[creation/read, default 64] - the number of rounds to be performed (minimum 48, multiple of 4)
Key length:
Minimum 48, maximum 256, multiple of 16 bits; default 128 bits.
Block size:
16 bytes.
Security comment:
[see security comment for SPEED-64]
| SPEED-256[(rounds)] | Block Cipher |
|---|
Designer:
Published:
February 1997
References:
[see references for SPEED-64]
Parameters:
Integer rounds[creation/read, default 64] - the number of rounds to be performed (minimum 48, multiple of 4)
Key length:
Minimum 48, maximum 256, multiple of 16 bits; default 128 bits.
Block size:
32 bytes.
Security comment:
[see security comment for SPEED-64]
| Square[(rounds)] | Block Cipher |
|---|
Designers:
Published:
1997
References:
- [_Def, An_] Joan Daemen, Lars Knudsen, Vincent Rijmen,
"The Block Cipher Square,"
Fast Software Encryption, Volume 1267 of Lecture Notes in Computer Science (E. Biham, ed.), pp. 149-165. Springer-Verlag, 1997.
http://www.esat.kuleuven.ac.be/~cosicart/ps/VR-9700.ps.gz (PDF version). - [_Inf, Impl_] Joan Daemen, Lars Knudsen, Vincent Rijmen,
The Square Page,
http://www.esat.kuleuven.ac.be/~rijmen/square/ - [_Test_] Paulo Barreto,
Validation data set for Square v1.0,
http://www.esat.kuleuven.ac.be/~rijmen/downloadable/square/vdata
Parameters:
Integer rounds[creation/read, default 8] - the number of rounds to be performed (minimum 8, multiple of 2)
Key length:
128 bits.
Block size:
16 bytes.
Designers:
David Wheeler,Roger Needham
Published:
1994
References:
- [_Def, Impl_] David Wheeler, Roger Needham,
"TEA, a Tiny Encryption Algorithm,"
Fast Software Encryption, Cambridge Security Workshop Proceedings, Volume 809 of Lecture Notes in Computer Science (Ross Anderson, ed.), pp. 363-366. Springer-Verlag, 1994.
http://www.cl.cam.ac.uk/ftp/users/djw3/tea.ps (PDF version) - [_An_] John Kelsey, Bruce Schneier, David Wagner,
"Related-Key Cryptanalysis of 3-WAY, Biham-DES, CAST, DES-X, NewDES, RC2, and TEA,"
ICICS '97 Proceedings, Springer-Verlag, November 1997.
http://www.counterpane.com/related-key_cryptanalysis.html - [_An_] Roger Fleming, David Wagner,
Subject: "An attack on a weakened version of TEA"
sci.crypt thread, October 1996.
Link to Google groups
Key length:
128 bits.
Block size:
8 bytes.
Missing information:
Test vectors.
Comment:
- Big-endian byte order is used when converting the plaintext, ciphertext, and key to 32-bit words. Note that this may not match some other TEA implementations.
- The algorithm "XTEA" (sometimes called "tean") was intended to be a modification of TEA resistant to related key attacks. However, that algorithm is not well-defined (it was implemented inconsistently, due to an ambiguity in the paper describing it [PS,PDF]), and is not included in SCAN.
- "Block TEA" is also not included in SCAN, and neither isthis correction to Block TEA.
Security comment:
TEA is vulnerable to related-key attacks, and therefore it should only be used with keys that are generated by a strong RNG, or by a source of bits that are sufficiently uncorrelated (such as the output of a hash function).
Designers:
Bruce Schneier, John Kelsey, Doug Whiting,David Wagner, Chris Hall, Niels Ferguson
Published:
1998
Alias:
"OpenPGP.Cipher.10" [[implies 256-bit key]]
References:
- [_Def, An_] Bruce Schneier, John Kelsey, Doug Whiting, David Wagner, Chris Hall, Niels Ferguson,
"Twofish: A 128-bit Block Cipher,"
15 June 1998. Presented at the 1st AES Conference.
http://www.counterpane.com/twofish-paper.html
[[see comment]] - [_Inf, Test, Impl_] Bruce Schneier, John Kelsey, Doug Whiting, David Wagner, Chris Hall, Niels Ferguson,
The Twofish: A New Block Cipher Page,
http://www.counterpane.com/twofish.html - [_Inf_] Bruce Schneier, Doug Whiting,
"Improved Twofish Implementations,"
December 2, 1998.
http://www.counterpane.com/twofish-speed.html - [_An_] Niels Ferguson,
"Upper Bounds on Differential Characteristics in Twofish,"
Twofish Technical Report #1, August 17, 1998.
http://www.counterpane.com/twofish-differential.html - [_An_] Doug Whiting, David Wagner,
"Empirical Verification of Twofish Key Uniqueness Properties,"
Twofish Technical Report #2, September 22, 1998.
http://www.counterpane.com/twofish-keys.html - [_An_] Bruce Schneier, John Kelsey, Doug Whiting, David Wagner, Chris Hall, Niels Ferguson,
"On the Twofish Key Schedule,"
Twofish Technical Report #3, Fifth Annual Workshop on Selected Areas in Cryptography, Springer Verlag, August 1998.
http://www.counterpane.com/twofish-keysched.html - [_An_] Fauzan Mirza, Sean Murphy,
"An Observation on the Key Schedule of Twofish,"
Presented at the 2nd AES Conference.
http://csrc.nist.gov/encryption/aes/round1/conf2/papers/mirza.pdf - [_An_] Bruce Schneier, John Kelsey, Doug Whiting, David Wagner, Chris Hall, Niels Ferguson,
"Further Observations on the Key Schedule of Twofish,"
Twofish Technical Report #4, March 16, 1999.
http://www.counterpane.com/twofish-ks2.html - [_An_] Niels Ferguson,
"Impossible Differential Attack of Simplified Twofish,"
Twofish Technical Report #5, October 1999.
http://www.counterpane.com/twofish-impossible.html - [_An_] Bruce Schneier, John Kelsey, Doug Whiting, Niels Ferguson,
"A Twofish Retreat: Related-Key Attacks Against Reduced-Round Twofish,"
Twofish Technical Report #6, February 2000.
http://www.counterpane.com/twofish-related.html - [_An_] Sean Murphy,
"The Key Separation of Twofish,"
March 15, 2000. Presented at the 3rd AES Candidate Conference.
http://csrc.nist.gov/encryption/aes/round2/conf3/papers/10-smurphy.pdf - [_An_] John Kelsey,
"Key Separation in Twofish,"
Twofish Technical Report #7, April 7 2000.
http://www.counterpane.com/twofish-tr7.html - [_An_] Sean Murphy,
"Differential Distributions for Twofish S-Boxes,
Submitted to NIST as an AES comment, May 2000.
http://csrc.nist.gov/encryption/aes/round2/comments/20000524-smurphy.pdf - [_An_] Sean Murphy, Matt Robshaw,
"Differential Cryptanalysis, Key-Dependent S-Boxes, and Twofish,"
Submitted to NIST as an AES comment, May 2000.
http://csrc.nist.gov/encryption/aes/round2/comments/20000515-smurphy.pdf - [_An_] Lars Knudsen,
"Trawling Twofish (revisited)," http://www.ii.uib.no/~larsr/papers/traw-revisited.ps or http://csrc.nist.gov/encryption/aes/round2/comments/20000515-lknudsen-2.pdf - [_An_] Bruce Schneier, John Kelsey, Doug Whiting, Niels Ferguson,
"A Second Twofish Retreat,"
Presented at the recent result session of AES3. - [_An_] K. Daemen,
"Cryptanalysis of Twofish,"
Thesis, KU Leuven, 2000. - [_An_] B. Preneel, A. Bosselaers, V. Rijmen, B. Van Rompay, L. Granboulan, J. Stern, S. Murphy, M. Dichtl, P. Serf, E. Biham, O. Dunkelman, V. Furman, F. Koeune, G. Piret, J-J. Quisquater, L. Knudsen, H. Raddum,
"Comments by the NESSIE Project on the AES Finalists,"
Submitted to NIST as an AES comment, May 2000.
http://csrc.nist.gov/encryption/aes/round2/comments/20000524-bpreneel.pdf - [_An_] Tetsu Iwata, Kaoru Kurosawa,
"On the Pseudorandomness of AES Finalists - RC6, Serpent, MARS and Twofish,"
Presented at Fast Software Encryption 2000, New York. - [_Test_] NIST,
Twofish Test Values,
http://www-08.nist.gov/encryption/aes/round1/testvals/twofish-vals.zip
Key length:
Minimum 8, maximum 256, multiple of 8 bits; default 128 bits.
Block size:
16 bytes.
Comment:
The C and Java reference implementations differ from the specification in "Twofish: A 128-bit Block Cipher," for key lengths between 8 and 64 bits inclusive. A strict reading of the specification would zero-pad these keys to 128 bits, and use k = 2; the reference implementations zero-pad them to 64 bits, and use k = 1. This algorithm follows the reference implementations (however, the use of keys this small is definitely NOT RECOMMENDED).
| ? WAKE-CFB-BE | Stream Cipher |
|---|
Designer:
David Wheeler
Published:
1993
Description:
This is WAKE in CFB mode, using big-endian byte order. See the Comments section below.
References:
- [_Def, Impl_] David Wheeler,
"A Bulk Data Encryption Algorithm,"
Fast Software Encryption, Cambridge Security Workshop Proceedings, Volume 809 of Lecture Notes in Computer Science (Ross Anderson, ed.), pp. 127-134. Springer-Verlag, 1994.
http://www.cl.cam.ac.uk/Research/Security/docs/wake.ps (PDF,HTML versions). - [_Inf_] Keith Lockstone, David Wheeler
WAKE - questions and answers,
http://www.cix.co.uk/~klockstone/wakeqna.htm
Key length:
128 bits.
Missing information:
Test vectors.
Comments:
- The internal operation of WAKE is endian-neutral, and is intentionally left unspecified in the paper "A Bulk Data Encryption Algorithm." We therefore define two different algorithm names for WAKE in CFB mode: WAKE-CFB-BE for big-endian operation, and WAKE-CFB-LE for little-endian operation. Note that this applies only to the byte order of the keystream words to be exclusive-or'd with the plaintext and ciphertext, not to the input key.
- The initial values of the four feedback registers are given directly by the key. Each key word is represented in big-endian order (which is consistent with the implementation in Wei Dai's Crypto++ library).
Security comments:
- WAKE is insecure against a chosen-plaintext or chosen-ciphertext attack.
- If a section of plaintext [[of what length?]] is zero, 32 bits of the key are revealed.
| ? WAKE-CFB-LE | Stream Cipher |
|---|
Designer:
David Wheeler
Published:
1993
Description:
This is WAKE in CFB mode, using little-endian byte order. See the Comments section for WAKE-CFB-BE.
References:
[see the references for WAKE-CFB-BE]
Key length:
128 bits.
Missing information:
Test vectors.
Comments:
- [see comments for ]
- There has an incompatible change in this algorithm since SCAN version 1.0.7; the input key words are now always interpreted as big-endian.
Security comments:
[see security comments for ]
| WiderWake4+1-BE | Stream Cipher |
|---|
Designer:
Craig Clapp (based on WAKE, by David Wheeler)
Published:
January 1997
Alias:
"WiderWake41BE" (use for identifiers)
Description:
This is the 4+1 variant of WiderWake, using big-endian byte order. See the Comments section below.
References:
- [_Def, Impl, Test_] Craig Clapp,
Optimizing a Fast Stream Cipher for VLIW, SIMD, and Superscalar Processors,
Presented at the 4th annual Fast Software Encryption Workshop, January 20-22, 1997, Haifa, Israel.
http://standard.pictel.com/ftp/research/security/widerwake.pdf
Key length:
128 bits.
Comments:
- There are two variants of WiderWake: 4+1, which is designed for speed on processors with few registers, and 4+3, which is slightly more conservative. The reference implementation and test vectors in the paper "Optimizing a Fast Stream Cipher for VLIW, SIMD, and Superscalar Processors," are for WiderWake4+1.
- The internal operation of WiderWake is endian-neutral, and is intentionally left unspecified in the paper cited above. We therefore define two different algorithm names for each variant of WiderWake: WiderWake4+1-BE and WiderWake4+3-BE for big-endian operation, and WiderWake4+1-LE and WiderWake4+3-LE for little-endian operation. Note that this applies to the byte order of the keystream words to be exclusive-or'd with the plaintext and ciphertext, and to the IV. The 128-bit input key is always represented in big-endian order.
- WiderWake has a resynchronisation procedure, which uses an 8-byte IV to randomise the feedback words. This IV is represented as two 32-bit words, each using the same byte order as the keystream words (see above). The IV can be set in the same way as would be used for a block cipher; a resynchronisation is done whenever it is set. Note that a resynchronisation is also always done before encrypting the first byte of data, or when the cipher is reset (using a random IV, if one has not been set explicitly).
- There have been incompatible changes in these algorithms since SCAN version 1.0.7; the input key words are now always interpreted as big-endian, and support for resynchronisation has been added.
| WiderWake4+1-LE | Stream Cipher |
|---|
Designer:
Craig Clapp (based on WAKE, by David Wheeler)
Published:
January 1997
Alias:
"WiderWake41LE" (use for identifiers)
Description:
This is the 4+1 variant of WiderWake, using little-endian byte order. See the Comments section for WiderWake4+1-BE.
References:
[see references for WiderWake4+1-BE]
Key length:
128 bits.
Comments:
[see comments for WiderWake4+1-BE]
| ? WiderWake4+3-BE | Stream Cipher |
|---|
Designer:
Craig Clapp (based on WAKE, by David Wheeler)
Published:
January 1997
Alias:
"WiderWake43BE" (use for identifiers)
Description:
This is the 4+3 variant of WiderWake, using big-endian byte order. See the Comments section for WiderWake4+1-BE.
References:
[see references for WiderWake4+1-BE]
Key length:
128 bits.
Missing information:
Test vectors.
Comments:
[see comments for WiderWake4+1-BE]
| ? WiderWake4+3-LE | Stream Cipher |
|---|
Designer:
Craig Clapp (based on WAKE, by David Wheeler)
Published:
January 1997
Alias:
"WiderWake43LE" (use for identifiers)
Description:
This is the 4+3 variant of WiderWake, using little-endian byte order. See the Comments section for WiderWake4+1-BE.
References:
[see references for WiderWake4+1-BE]
Key length:
128 bits.
Missing information:
Test vectors.
Comments:
[see comments for WiderWake4+1-BE]
| × PBE-PKCS5(digestName,DES/CBC) | Block Cipher Construction |
|---|
Designers:
Aliases:
- "pbeWithMD2AndDES-CBC" and "PBEWithMD2AndDES" for PBE-PKCS5(MD2,DES/CBC).
- "pbeWithMD5AndDES-CBC" and "PBEWithMD5AndDES" for PBE-PKCS5(MD5,DES/CBC).
Object Identifiers:
- 1.2.840.113549.1.5.1 for PBE-PKCS5(MD2,DES/CBC).
- 1.2.840.113549.1.5.3 for PBE-PKCS5(MD5,DES/CBC).
Description:
The passphrase-based encryption algorithm specified in version 1.5 of PKCS #5. For the Java mapping, the key MUST be an instance of PBEKeySpec, or a subclass of PBEKeySpec.
Note that these algorithms are only specified for compatibility with Sun's JCE 1.2. The preferred way of doing passphrase-based encryption in SCAN is described in the documentation for PassphraseHash.
References:
- [_Def_] PKCS #5: Password-Based Encryption Standard,
An RSA Laboratories Technical Note, Version 1.5. Revised November 1, 1993. ftp://ftp.rsa.com/pub/pkcs/ascii/pkcs-5.asc
Parameters:
String digestName[creation/read, no default] - the name of the message digest to be used to generate the key and IV.
Key length:
64 bits as encoded, 56 bits excluding parity bits.
Block size:
8 bytes.
Comment:
The method described in PKCS #5 v1.5 cannot easily be generalised to support ciphers other than DES. However, DES/CBC MUST still be specified as if it were a parameter, for consistency with the names of other passphrase-based cipher constructions.
Security comment:
The 56-bit effective key length is too short to prevent brute-force attacks.
| × PBE-PKCS12(digestName,cipherName [,_keyLength_]) | Cipher Construction |
|---|
Designers:
Aliases:
- "pbeWithSHAAnd128BitRC4" for PBE-PKCS12(SHA-1,RC4,128).
- "pbeWithSHAAnd40BitRC4" for PBE-PKCS12(SHA-1,RC4,40).
- "pbeWithSHAAnd3-KeyTripleDES-CBC" for PBE-PKCS12(SHA-1,DESede/CBC,168).
- "pbeWithSHAAnd2-KeyTripleDES-CBC" for PBE-PKCS12(SHA-1,DESede/CBC,112).
- "pbeWithSHAAnd128BitRC2-CBC" for PBE-PKCS12(SHA-1,RC2/CBC,128).
- "pbeWithSHAAnd40BitRC2-CBC" for PBE-PKCS12(SHA-1,RC2/CBC,40).
Object Identifiers:
- 1.2.840.113549.1.12.1.1 for PBE-PKCS12(SHA-1,RC4,128).
- 1.2.840.113549.1.12.1.2 for PBE-PKCS12(SHA-1,RC4,40).
- 1.2.840.113549.1.12.1.3 for PBE-PKCS12(SHA-1,DESede/CBC,168).
- 1.2.840.113549.1.12.1.4 for PBE-PKCS12(SHA-1,DESede/CBC,112).
- 1.2.840.113549.1.12.1.5 for PBE-PKCS12(SHA-1,RC2/CBC,128).
- 1.2.840.113549.1.12.1.6 for PBE-PKCS12(SHA-1,RC2/CBC,40).
Description:
The passphrase-based encryption algorithm specified in version 1.0 of PKCS #12. For the Java mapping, the key MUST be an instance of PBEKeySpec, or a subclass of PBEKeySpec.
Note that these algorithms are only specified for compatibility with Sun's JCE 1.2. The preferred way of doing passphrase-based encryption in SCAN is described in the documentation for PassphraseHash.
References:
- [_Def_] PKCS #12: Personal Information Exchange Syntax Standard,
Version 1.0, with Technical Corrigendum.
http://www.rsalabs.com/pkcs/pkcs-12/
Parameters:
String digestName[creation/read, no default] - the name of the message digest to be used to generate the key and (if needed) the IV.String cipherName[creation/read, no default] - the name of the cipher to be used for encryption/decryption.Integer keyLength[creation/read, default equal to the default key length of the cipher given by _cipherName_] - the effective bit length (i.e. excluding parity bits) to be used for the key.
Key length:
Same as the value of the keyLength property.
Block size:
Same as the block size of the cipher given by cipherName.
Security comment:
PBE-PKCS12 does not define any way to iterate the hashing operation in order to slow down a dictionary attack against the passphrase. It will therefore become more vulnerable than necessary to attacks against weak passphrases, as the performance of computing hardware increases.
Description:
A "no-op" algorithm, for which the ciphertext is identical to the plaintext.
Key length:
0 bits.
Security comment:
This algorithm provides no security. (Note that its existance is not in itself a security weakness; even without a no-op algorithm, it would not be valid for applications to assume that an arbitrary Cipher object or algorithm will provide adequate security.)
Block Cipher Modes
Symmetric block cipher modes fall into two categories: block-oriented and byte-oriented. For block-oriented modes, the plaintext or ciphertext can only be processed one block at a time. This means that a "padding scheme" is needed to specify how to handle the last block of a message, i.e. the standard algorithm name will be of the form "cipher/mode/padding". If messages are always an exact number of blocks in length, "NoPadding" may be specified as the padding scheme.
For byte-oriented modes, the plaintext or ciphertext can be processed one byte at a time (by use of internal buffering if necessary). This means that a padding scheme is not required, i.e. the standard name will be of the form "cipher/mode". For backward compatibility, however, any of the forms "cipher/mode", "cipher/mode/NoPadding", and "cipher/mode/NONE" should be accepted when the mode is byte-oriented. The last two of these are deprecated.
Description:
Electronic Codebook Mode, as defined in NBS FIPS PUB 81.
References:
- [_Inf_] U.S. National Bureau of Standards (now NIST),
"DES Modes of Operation,"
NBS FIPS PUB 81, U.S. Department of Commerce, December 1980.
http://www.itl.nist.gov/div897/pubs/fip81.htm - [_Inf_] Bruce Schneier,
"Section 9.1 Electronic Codebook Mode,"
Applied Cryptography, Second Edition, John Wiley & Sons, 1996. - [_Inf_] sci.crypt FAQ, "Part 5: Product Ciphers,"
ftp://ftp.rtfm.mit.edu/pub/usenet/news.answers/cryptography-faq/part05
Comment:
If a padding scheme is not specified (i.e. the algorithm name is given in the form "cipherName/ECB"), then NoPadding MUST be assumed (note that this is intentionally different to CBC and PCBC modes, for which PKCSPadding would be used). The standard name always specifies which padding method is used, i.e. it always has three components.
Security comment:
ECB mode will always encrypt identical plaintext blocks to identical ciphertexts. This can be a weakness when the plaintext is not random, uniformly distributed, and a multiple of the block size. If these conditions are not satisfied, a different mode should probably be used.
Description:
Cipher Block Chaining Mode, as defined in NBS FIPS PUB 81.
References:
- [_Inf_] U.S. National Bureau of Standards (now NIST),
"DES Modes of Operation,"
NBS FIPS PUB 81, U.S. Department of Commerce, December 1980.
http://www.itl.nist.gov/div897/pubs/fip81.htm - [_Inf_] Bruce Schneier,
"Section 9.3 Cipher Block Chaining Mode,"
Applied Cryptography, Second Edition, John Wiley & Sons, 1996. - [_Inf_] sci.crypt FAQ, "Part 5: Product Ciphers,"
ftp://ftp.rtfm.mit.edu/pub/usenet/news.answers/cryptography-faq/part05 - [_Inf_] M. Bellare, A. Desai, E. Jokipii, P. Rogaway,
"A Concrete Security Treatment of Symmetric Encryption: Analysis of the DES Modes of Operation,"
http://www-cse.ucsd.edu/users/mihir/papers/sym-enc.html
Comment:
If a padding scheme is not specified (i.e. the algorithm name is given in the form "cipherName/CBC"), then PKCSPadding MUST be assumed. The standard name always specifies which padding method is used, i.e. it always has three components.
Description:
Propagating Cipher Block Chaining Mode.
References:
- [_Inf_] Bruce Schneier,
"Section 9.10 Other Block Cipher Modes,"
Applied Cryptography, Second Edition, John Wiley & Sons, 1996. - [_Inf_] sci.crypt FAQ, "Part 5: Product Ciphers."
ftp://ftp.rtfm.mit.edu/pub/usenet/news.answers/cryptography-faq/part05
Comment:
If a padding scheme is not specified (i.e. the algorithm name is given in the form "cipherName/PCBC"), then PKCSPadding MUST be assumed. The standard name always specifies which padding method is used, i.e. it always has three components.
| CFB[(feedbackBits)] | Byte-oriented Mode |
|---|
Description:
Cipher Feedback Mode, as defined in NBS FIPS PUB 81, with a feedback vector of length feedbackBits bits.
Aliases:
"CFB_n_", where n is an integer, can be used as a deprecated alias for "CFB(n)".
The values of n that may need to be supported for backward compatibility are 8 and 64.
References:
- [_Inf_] U.S. National Bureau of Standards (now NIST),
"DES Modes of Operation,"
NBS FIPS PUB 81, U.S. Department of Commerce, December 1980.
http://www.itl.nist.gov/div897/pubs/fip81.htm - [_Inf_] Bruce Schneier,
"Section 9.6 Cipher-Feedback Mode,"
Applied Cryptography, Second Edition, John Wiley & Sons, 1996. - [_Inf_] sci.crypt FAQ, "Part 5: Product Ciphers,"
ftp://ftp.rtfm.mit.edu/pub/usenet/news.answers/cryptography-faq/part05
Parameters:
Integer feedbackBits[creation/read, default equal to the number of bits in a block] - the length of the feedback vector in bits (from 1 bit, to the number of bits in a block)
Comment:
The value of feedbackBits does not affect the granularity of data that can be encrypted or decrypted. Implementations MUST support immediate processing of individual bytes, in a similar fashion to a stream cipher. This means that it is never necessary to specify a padding scheme (and therefore the standard name always has two components).
Description:
Output Feedback Mode, as defined in NBS FIPS PUB 81, except that the feedback vector is restricted to be the same size as a block.
References:
- [_Inf_] U.S. National Bureau of Standards (now NIST),
"DES Modes of Operation,"
NBS FIPS PUB 81, U.S. Department of Commerce, December 1980.
http://www.itl.nist.gov/div897/pubs/fip81.htm - [_Inf_] Bruce Schneier,
"Section 9.8 Output-Feedback Mode,"
Applied Cryptography, Second Edition, John Wiley & Sons, 1996. - [_Inf_] sci.crypt FAQ, "Part 5: Product Ciphers,"
ftp://ftp.rtfm.mit.edu/pub/usenet/news.answers/cryptography-faq/part05 - [_An_] Robert R. Jueneman,
"Analysis of Certain Aspects of Output Feedback Mode,"
Advances in Cryptology - CRYPTO '82 Proceedings (D. Chaum, R. Rivest and A. Sherman, ed.), Plenum Press, 1983, pp. 99-127. - [_An_] D.W. Davies, G.I.P. Parkin,
"The Average Size of the Key Stream in Output Feedback Mode,"
Cryptography, Proceedings of the Workshop on Cryptography, Burg-Feuerstein, Germany, March 29-April 2, 1982, Springer-Verlag, 1983, pp. 263-279.
Also in Advances in Cryptology - CRYPTO '82 Proceedings, Plenum Press, 1983, pp. 97-98.
Comments:
- Implementations MUST support immediate processing of individual bytes, in a similar fashion to a stream cipher. This means that it is never necessary to specify a padding scheme (and therefore the standard name always has two components).
- The reason for not supporting feedback sizes less than the block size, is that this greatly reduces the expected period of the keystream (e.g. from about 266 bytes to 234 bytes, for a cipher with a block size of 8 bytes).
| InterleavedCBC(nStreams) | Block-oriented Mode |
|---|
Description:
Interleaved Cipher Block Chaining Mode, with nStreams independent IVs. The length of the IV array required by setIV (or generated randomly) will be nStreams * blockSize bytes.
References:
- [_Inf_] U.S. National Bureau of Standards (now NIST),
"DES Modes of Operation,"
NBS FIPS PUB 81, U.S. Department of Commerce, December 1980.
http://www.itl.nist.gov/div897/pubs/fip81.htm - [_Inf_] Bruce Schneier,
"Section 9.3 Cipher Block Chaining Mode," and "Section 9.12 Interleaving,"
Applied Cryptography, Second Edition, John Wiley & Sons, 1996. - [_Inf_] sci.crypt FAQ, "Part 5: Product Ciphers,"
ftp://ftp.rtfm.mit.edu/pub/usenet/news.answers/cryptography-faq/part05
Parameters:
Integer nStreams[creation/read, no default] - the number of interleaved streams (minimum 1)
If a padding scheme is not specified (i.e. the algorithm name is given in the form "cipherName/InterleavedCBC(nStreams)"), thenPKCSPadding MUST be assumed. The standard name always specifies which padding method is used, i.e. it always has three components.
| InterleavedPCBC(nStreams) | Block-oriented Mode |
|---|
Description:
Interleaved Propagating Cipher Block Chaining Mode, with nStreams independent IVs. The length of the IV array required by setIV (or generated randomly) will be nStreams * blockSize bytes.
References:
- [_Inf_] Bruce Schneier,
"Section 9.10 Other Block Cipher Modes," and "Section 9.12 Interleaving,"
Applied Cryptography, Second Edition, John Wiley & Sons, 1996. - [_Inf_] sci.crypt FAQ, "Part 5: Product Ciphers,"
ftp://ftp.rtfm.mit.edu/pub/usenet/news.answers/cryptography-faq/part05
Parameters:
Integer nStreams[creation/read, no default] - the number of interleaved streams (minimum 1)
Comment:
If a padding scheme is not specified (i.e. the algorithm name is given in the form "cipherName/InterleavedPCBC(nStreams)"), thenPKCSPadding MUST be assumed. The standard name always specifies which padding method is used, i.e. it always has three components.
| InterleavedCFB(nStreams) | Byte-oriented Mode |
|---|
Description:
Interleaved Cipher Feedback Mode, with nStreams independent IVs, and with each feedback vector of equal size to a block. The length of the IV array required by setIV (or generated randomly) will be nStreams * blockSize bytes.
References:
- [_Inf_] U.S. National Bureau of Standards (now NIST),
"DES Modes of Operation,"
NBS FIPS PUB 81, U.S. Department of Commerce, December 1980.
http://www.itl.nist.gov/div897/pubs/fip81.htm - [_Inf_] Bruce Schneier,
"Section 9.6 Cipher-Feedback Mode," and "Section 9.12 Interleaving,"
Applied Cryptography, Second Edition, John Wiley & Sons, 1996. - [_Inf_] sci.crypt FAQ, "Part 5: Product Ciphers,"
ftp://ftp.rtfm.mit.edu/pub/usenet/news.answers/cryptography-faq/part05
Parameters:
Integer nStreams[creation/read, no default] - the number of interleaved streams (minimum 1)
Comment:
Implementations MUST support immediate processing of individual bytes, in a similar fashion to a stream cipher. This means that it is never necessary to specify a padding scheme (and therefore the standard name always has two components).
| Counter-BE | Block-oriented Mode |
|---|
Description:
Counter mode, with big-endian representation of block numbers.
Alias:
"CTR-BE"
References:
- [_Inf_] Bruce Schneier,
"Section 9.9 Counter Mode,"
Applied Cryptography, Second Edition, John Wiley & Sons, 1996. - [_Inf_] sci.crypt FAQ, "Part 5: Product Ciphers,"
ftp://ftp.rtfm.mit.edu/pub/usenet/news.answers/cryptography-faq/part05 - [_An_] Helger Lipmaa, Phillip Rogaway, David Wagner,
"Comments to NIST Concerning AES-modes of Operations: CTR-mode Encryption,"
Symmetric Key Block Cipher Modes of Operation Workshop, Baltimore, Maryland, U.S., 20 October 2000.
http://www.tml.hut.fi/~helger/papers/lrw00/
Comments:
- The block number starts at zero for the first block. It is zero-padded on the left, so that the least significant byte is the last byte of each block. No IV is used.
- If a padding scheme is not specified (i.e. the algorithm name is given in the form "cipherName/Counter-BE"), thenPKCSPadding MUST be assumed. The standard name always specifies which padding method is used, i.e. it always has three components.
Security comment:
Because the keystream depends only on the block number and key, this mode MUST NOT be used to encrypt more than one message with the same key.
| Counter-LE | Block-oriented Mode |
|---|
Description:
Counter mode, with little-endian representation of block numbers.
Alias:
"CTR-LE"
References:
[see references for Counter-BE]
Comments:
- The block number starts at zero for the first block. It is zero-padded on the right, so that the least significant byte is the first byte of each block. No IV is used.
- If a padding scheme is not specified (i.e. the algorithm name is given in the form "cipherName/Counter-LE"), thenPKCSPadding MUST be assumed. The standard name always specifies which padding method is used, i.e. it always has three components.
Security comment:
Because the keystream depends only on the block number and key, this mode MUST NOT be used to encrypt more than one message with the same key.
| × KFB(m) | Byte-oriented Mode |
|---|
Designers:
Johan Håstad, Mats Näslund
Published:
October 2000
Description:
Key Feedback Mode, with m bits of keystream taken for each application of the block cipher. If cipher is a block cipher with block size n bits and key length also n bits, then the SCAN name "cipher/KFB(m)" refers to the keystream generator BMGL_n_,m,L(cipher), where L is the number of bits of output used (L is not included in the cipher name because an arbitrary length of plaintext can be encrypted by a SCAN stream cipher; however, application designers should bear in mind that the security bound depends on this value.) m is the number of bits taken for each iteration of the block cipher; for a given cipher, a lower m gives a better security bound.
References:
- [_Def, An_] Johan Håstad, Mats Näslund,
Key Feedback Mode: A KeyStream Generator with Provable Security,
... - [_Inf, An_] Johan Håstad, Mats Näslund,
BMGL: Synchronous Key-stream Generator with Provable Security,
https://www.cosic.esat.kuleuven.ac.be/nessie/workshop/submissions/bmgl.zip - [_Test_] Johan Håstad, Mats Näslund,
BMGL Test Values,
https://www.cosic.esat.kuleuven.ac.be/nessie/workshop/submissions/bmgl.zip
Key length:
The cipher key length must be the same as its block size.
Security comment:
The security bounds proven for KFB with a 256-bit block cipher and m = 40, in Corollary 13 of Håstad and Mats Näslund's paper, hold provided that less than 230 bits (128 MBytes) of output are used. The "provable security" referred to in the paper is in the sense of a proven reduction from predicting the keystream generator to breaking the cipher as a one-way function.
Block Cipher Padding
Alias:
"CiphertextStealing"
References:
- [_Def_] Bruce Schneier,
"Section 9.1 Electronic Code Book Mode,"
"Figure 9.1 Ciphertext stealing in ECB mode,"
"Section 9.3 Cipher Block Chaining Mode," and
"Figure 9.5 Ciphertext stealing in CBC mode,"
Applied Cryptography, Second Edition, John Wiley & Sons, 1996. - [_Inf, Test_] Ron Rivest,
"The RC5, RC5-CBC, RC5-CBC-Pad, and RC5-CTS Algorithms,"
RFC 2040, October 1996.
Comments:
- CTS is only defined for block ciphers in ECB and CBC modes.
- The "RC5-CTS" mode in RFC 2040 is equivalent to RC5/CBC/CTS; this gives a source of test vectors, at least for one cipher.
- The amount of data that must be buffered by the cipher implementation is increased when ciphertext stealing is used (specifically, up to two blocks can be buffered, for both encryption and decryption).
- If the total length of plaintext or ciphertext, excluding IV, is less than or equal to one block when
doFinalis called, aBadPaddingExceptionwill be thrown. (I.e. the minimum length of plaintext that can be encrypted is one block plus one byte.) - The diagrams in Applied Cryptography do not make clear the behaviour when the plaintext or ciphertext length is an exact number of blocks. In this case the "last" block is considered to be the last complete block, rather than being of zero-length. This matches the specification in section 8 of RFC 2040. Note that in this case the last two blocks of the ciphertext will be interchanged when compared with ECB or CBC mode with NoPadding.
Description:
An algorithm that appends (using big-endian bit order) a single binary 1 bit, followed by as many binary 0 bits as needed to complete a block. Viewed in terms of bytes, this corresponds to a byte of 0x80, followed by as many 0x00 bytes as needed to complete a block.
Aliases:
"PKCS#5", "PKCS#7", "PKCS5Padding"
Description:
The padding scheme described in PKCS #7 section 10.3, note 2 (this is a generalisation of the scheme described in PKCS #5 section 6.2, to block sizes between 1 and 255 bytes inclusive).
References:
- [_Def_] PKCS #7: Cryptographic Message Syntax Standard,
An RSA Laboratories Technical Note, Version 1.5. Revised November 1, 1993. ftp://ftp.rsa.com/pub/pkcs/ascii/pkcs-7.asc - [_Inf_] PKCS #5: Password-Based Encryption Standard,
An RSA Laboratories Technical Note, Version 1.5. Revised November 1, 1993. ftp://ftp.rsa.com/pub/pkcs/ascii/pkcs-5.asc
Comment:
When this algorithm is referenced using the "PKCS#5" or "PKCS5Padding" aliases, it should not be assumed that block sizes other than 8 bytes will be supported.
Description:
Trailing Bit Complement. The data is padded with the complement of the trailing bit (that is, the least significant bit of the last byte) of the unpadded message: if the trailing bit is '1', then '0' bits are appended, and if the trailing bit is '0', then '1' bits are appended. Viewed in terms of bytes, this corresponds to adding between 1 byte and a full block of 0x00 or 0xFF.
References:
- NIST,
Draft Modes Recommendation, July 2001.
http://csrc.nist.gov/encryption/modes/Recommendation/Modes01.pdf
Comment:
TBC is rarely used compared to other padding schemes.
Description:
An algorithm name used to specify that for encryption, aBadPaddingException will be thrown when the plaintext input is not an exact number of blocks, and for decryption, that no unpadding will be done.
Alias:
"NONE"
Other Alleged Padding Schemes
- The SunJCE provider defines SSL3Padding, which is intended to specify the padding method used in the SSL 3.0 protocol. However, that algorithm cannot be used to implement padding in a way that is compliant with SSL 3.0 (since there is no way to correctly support records that use more than the minimum amount of padding).
KeyGenerators
For each symmetric cipher, there is a KeyGenerator with the same standard name and aliases, that can be used to generate random keys for that cipher. Since the valid key lengths, and any comments on the key encoding are given with the cipher descriptions (and there is generally only one valid key encoding for a symmetric cipher), there is no need for each KeyGenerator algorithm to be described separately.
Typically, the default key length for each algorithm is the one that will be used in most cases. For DESede (Triple DES) and AES, more than one key length is, or will be in common use (for example,OpenPGP has three different algorithm numbers for AES, according to key length). For that reason, we specify three key generator names for AES, and two for DESede, with different default key lengths. This should allow a more straightforward mapping between a SCAN name, and the algorithms specified in various standards.
Description:
A KeyGenerator for AES with 128-bit keys.
Alias:
"OpenPGP.Cipher.7"
Object Identifiers:
"2.16.840.1.101.3.4.1.1", "2.16.840.1.101.3.4.1.2", "2.16.840.1.101.3.4.1.3", "2.16.840.1.101.3.4.1.4"
References:
[see references for AES]
Description:
A KeyGenerator for AES with 192-bit keys.
Alias:
"OpenPGP.Cipher.8"
Object Identifiers:
"2.16.840.1.101.3.4.1.21", "2.16.840.1.101.3.4.1.22", "2.16.840.1.101.3.4.1.23", "2.16.840.1.101.3.4.1.24"
References:
[see references for AES]
Description:
A KeyGenerator for AES with 256-bit keys.
Aliases:
"AES", "OpenPGP.Cipher.9"
Object Identifiers:
"2.16.840.1.101.3.4.1.41", "2.16.840.1.101.3.4.1.42", "2.16.840.1.101.3.4.1.43", "2.16.840.1.101.3.4.1.44"
References:
[see references for AES]
Description:
A KeyGenerator for DESede with 2 independent single DES keys (i.e. 128 bits of key material).
References:
[see references for DESede]
Description:
A KeyGenerator for DESede with 3 independent single DES keys (i.e. 192 bits of key material).
Alias:
"OpenPGP.Cipher.2"
References:
[see references for DESede]
Alleged Symmetric Ciphers
- CAST, CAST3 are earlier versions ofCAST-128
- LOKI89 is an earlier version ofLOKI91.
- E0 (used in the Bluetooth protocols).
- FEAL (variable # of rounds) isbroken.
- Khufu and Khafre arebroken.
- Akelarre (several versions) is broken.
- Cipherunicorn.
- Dogfish.
- G-DES.
- NewDES.
- BEAST.
- BEAR, LION, LIONESS are PRP/SPRP constructions (need a new category for these?) Hand ciphers (these often work on a restricted character set rather than bytes):
- Solitaire (a.k.a. "Pontifex" in Neal Stephenson's bookCryptonomicon) isbroken.
- Mirdek is broken
