Two never-before-seen tools, from same group, infect air-gapped devices (original) (raw)
It's hard enough creating one air-gap-jumping tool. GoldenJackal did it 2x in 5 years.
Blue ethernet cable unplugged from socket on laptop Credit: Getty Images
Researchers have unearthed two sophisticated toolsets that a nation-state hacking group—possibly from Russia—used to steal sensitive data stored on air-gapped devices, meaning those that are deliberately isolated from the Internet or other networks to safeguard them from malware.
One of the custom tool collections was used starting in 2019 against a South Asian embassy in Belarus. A largely different toolset created by the same threat group infected a European Union government organization three years later. Researchers from ESET, the security firm that discovered the toolkits, said some of the components in both were identical to those fellow security firm Kaspersky described in research published last year and attributed to an unknown group, tracked as GoldenJackal, working for a nation-state. Based on the overlap, ESET has concluded that the same group is behind all the attacks observed by both firms.
Quite unusual
The practice of air gapping is typically reserved for the most sensitive networks or devices connected to them, such as those used in systems for voting, industrial control, manufacturing, and power generation. A host of malware used in espionage hacking over the past 15 years (for instance, here and here) demonstrate that air gapping isn’t a foolproof protection. It nonetheless forces threat groups to expend significant resources that are likely obtainable only by nation-states with superior technical acumen and unlimited budgets. ESET’s discovery puts GoldenJackal in a highly exclusive collection of threat groups.
“With the level of sophistication required, it is quite unusual that in five years, GoldenJackal managed to build and deploy not one, but two separate toolsets designed to compromise air-gapped systems,” ESET researcher Matías Porolli wrote in Tuesday’s report. “This speaks to the resourcefulness of the group.”
The evolution of the kit from 2019 and the one from three years later underscores a growing sophistication by GoldenJackal developers. The first generation provided a full suite of capabilities, including:
- GoldenDealer, a component that delivers malicious executables to air-gapped systems over USB drives
- GoldenHowl, a backdoor that contains various modules for a mix of malicious capabilities
- GoldenRobo, a file collector and exfiltrator
Within a few weeks of deploying the kit in 2019, ESET said, GoldenJackal started using other tools on the same compromised devices. The newer tools, which Kaspersky documented in its 2023 research, included:
- A backdoor tracked under the name JackalControl
- JackalSteal, a file collector and exfiltrator
- JackalWorm, used to propagate other JackalControl and other malicious components over USB drives
GoldenJackal, ESET said, continued using these tools into January of this year. The basic flow of the attack is, first, infecting an Internet-connected device through a means ESET and Kaspersky have been unable to determine. Next, the infected computer infects any external drives that get inserted. When the infected drive is plugged into an air-gapped system, it collects and stores data of interest. Last, when the drive is inserted into the Internet-connected device, the data is transferred to an attacker-controlled server.
Building a better trap
In the 2022 attack on the European Union governmental organization, GoldenJackal began using a new custom toolkit. Written in multiple programming languages, including Go and Python, the newer version took a much more specialized approach. It assigned different tasks to different types of infected devices and marshaled a much larger array of modules, which could be mixed and matched based on the attacker objects for different infections.
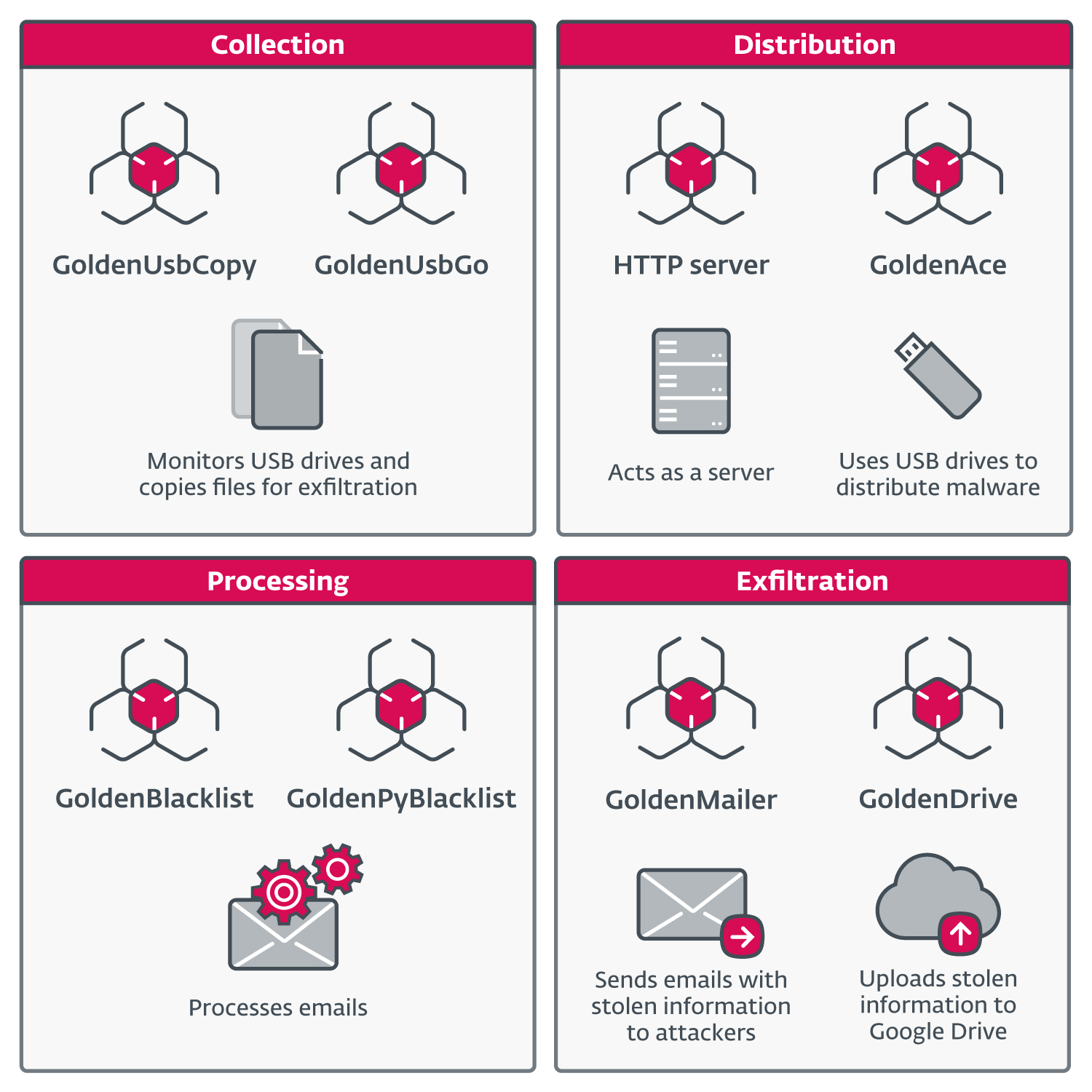
“In the observed attacks, GoldenJackal started to use a highly modular approach, using various components to perform different tasks,” ESET’s Porolli wrote. “Some hosts were abused to exfiltrate files, others were used as local servers to receive and distribute staged files or configuration files, and others were deemed interesting for file collection, for espionage purposes.”
The figure below classifies some of the components specifically:
- GoldenUsbCopy, which monitors for the insertion of USB drives on air-gapped devices and, when found, copies them to an encrypted container that is stored on disk
- GoldenUsbGo, which appears to be an updated version of GoldenUSBCopy
- GoldenAce, a distribution tool for propagating other malicious executables and retrieving files stored on USB drives
- HTTP server, an HTTP server whose precise function isn’t well understood
- GoldenBlacklist, which downloads an encrypted archive from a local server, sifts through received email messages for those of interest, and puts them in an archive for some other component to exfiltrate
- GoldenPyBlacklist, a Python implementation of GoldenBlacklist
- GoldenMailer, which, when connected to an Internet device, exfiltrates files of interest previously stolen from an air-gapped device. The exfiltration occurs by attaching them to emails sent to an attacker-controlled email address
- GoldenDrive, a separate exfiltration tool that, in contrast to GoldenMailer, uploads files of interest to Google Drive.
The components in GoldenJackal’s latest toolset.
Credit: ESET
The components in GoldenJackal’s latest toolset. Credit: ESET
The newly discovered toolkit is composed of many different building blocks, written in multiple languages and capabilities. The overall goal appears to be increased flexibility and resiliency in the event one module is detected by the target.
“Their goal is to get hard to obtain data from air-gapped systems and stay under the radar as much as possible,” Costin Raiu, a researcher who worked at Kaspersky at the time it was researching GoldenJackal, wrote in an interview. “Multiple exfiltration mechanisms indicate a very flexible tool kit that can accommodate all sorts of situations. These many tools indicate it’s a highly customizable framework where they deploy exactly what they need as opposed to a multi purpose malware that can do anything.”
Other new insights offered by the ESET research is GoldenJackal’s interest in targets located in Europe. Kaspersky researchers detected the group targeting Middle Eastern countries.
Based on the information that was available to Kaspersky, company researchers couldn’t attribute GoldenJackal to any specific country. ESET has also been unable to definitively identify the country, but it did find one hint that the threat group may have a tie to Turla, a potent hacking group working on behalf of Russia’s FSB intelligence agency. The tie comes in the form of command-and-control protocol in GoldenHowl referred to as transport_http. The same expression is found in malware known to originate with Turla.
Raiu said the highly modular approach is also reminiscent of Red October, an elaborate espionage platform discovered in 2013 targeting hundreds of diplomatic, governmental, and scientific organizations in at least 39 countries, including the Russian Federation, Iran, and the United States.
While much of Tuesday’s report contains technical analysis that is likely to be too advanced for many people to understand, it provides important new information that furthers insights into malware designed to jump air gaps and the tactics, techniques, and procedures of those who use it. The report will also be useful to people responsible for safeguarding the types of organizations most frequently targeted by nation-state groups.
“I’d say this is mostly interesting for security people working in embassies and government CERTs,” Raiu said. “They need to check for these TTPs and keep an eye on them in the future. If you were previously a victim of Turla or Red October I’d keep an eye on this.”
Dan Goodin is Senior Security Editor at Ars Technica, where he oversees coverage of malware, computer espionage, botnets, hardware hacking, encryption, and passwords. In his spare time, he enjoys gardening, cooking, and following the independent music scene. Dan is based in San Francisco. Follow him at here on Mastodon and here on Bluesky. Contact him on Signal at DanArs.82.