Stakeout: how the FBI tracked and busted a Chicago Anon (original) (raw)
Continuous surveillance, informants, trap-and-trace gear—the FBI spared no …
"Script kiddie"—no hacker worth his salt wants to hear the term used to describe him. Anyone with modest computer skills can cause modest havoc using other people's code fragments, scanners, and infiltration tools, but this is little more than knowing how to point a gun in the right direction and pull the trigger. It lacks art. True hacking requires a deep knowledge of computer and network security, an ability to navigate around obstacles, and the willingness to be careful enough to always hide one's tracks. The script kiddies, they might be easy targets for the feds, but the true hackers? Shadows are their home.
The Anon-affiliated hackers who broke into the private intelligence company Stratfor to release e-mails and steal credit cards certainly didn't think they were script kiddies. In an Internet Relay Chat (IRC) just after the December 2011 hack, one of the Statfor hackers (sup_g) spoke to an unidentified chatroom member (CC-3) about the accomplishment.
CC-3: but this stratfor shit was bigger shit than CC-3: old shits CC-3: at least it deserves no critics @sup_g: oh yes @sup_g: notice no one is throwing around script kiddie comments... CC-3: this time was classy CC-3: and thats perfect CC-3: we produced a cool video CC-3: we announced luzxmas CC-3: we hacked big shit CC-3: we donated by 1000000... CC-3: and we destroyed a big serious intel corp CC-3: actually just a lil bunch of ppl thinks shit on this CC-3: like 3 CC-3: lol @sup_g: they are just mad because of the sheer amount of high profile people in this
The day after Christmas, sup_g had another online chat about the Stratfor hack and about some 30,000 credit card numbers that had been taken from the company. His interlocutor, CW-1, engaged in a bit of gallows humor about what might happen should they all get caught.
CW-1: hows the news looking? @sup_g: I been going hard all night CW-1: I heard we're all over the news papers CW-1: you mother fuckers are going to get me raied [raided] CW-1: HAHAHAAHA @sup_g: we put out 30k cards, the it.stratfor.com dump, and another statement @sup_g: dude it's big.. CW-1: if I get raided anarchaos your job is to cause havok in my honor CW-1: <3 CW-1: sup_g: @sup_g: it shall be so
But the raid had, in fact, already happened. CW-1 was "Sabu," a top Anon/LulzSec hacker who was in real life an unemployed 28-year old living in New York City public housing. His sixth-floor apartment had been visited by the FBI in June 2011, and Sabu had been arrested and "turned." For months, he had been an FBI informant, watched 24 hours a day by an agent and using a government issued laptop that logged everything he did.
The FBI controllers behind Sabu must have found it grimly humorous to tease sup_g with threats of arrest, but they were also using Sabu's chat for a more serious purpose—correlating the many names of sup_g.
In the log above, note how Sabu suddenly addresses sup_g by a new name, "anarchaos." It would turn out that sup_g went by many names, including "anarchaos," "burn," "yohoho," "POW," "tylerknowsthis," and "crediblethreat."
Normally, the attempt to link his various names would have raised the hacker's guard; as he confided to Sabu, someone else had once tried to link the names "yohoho" and "burn," but the hacker "never answered... I think he picked up some language similarities I've worked with [REDACTED] on other ops in the past." But this was Sabu, a sort of hacker demigod in the world of Anonymous. If you couldn't trust him, who could you trust? Sabu had even provided a server to store the stolen Statfor data, so he couldn't be a fed (in reality, he had done so at the FBI's direction).
A document distributed after the Stratfor hack totted up the hack's damage.
"The sheer amount of destruction we wreaked on Stratfor's servers is the digital equivalent of a nuclear bomb," it said. "We rooted box after box on their intranet: dumping their mysql databases, stealing their private ssh keys, and copying hundred[s] of employee e-mail spools... We laid waste to their web server, their mail server, their development server, their clearspace and srm intranet portal and backup archives."
The document also claimed that more than $500,000 had been charged to credit cards and given to "charities and revolutionary organizations."
Usernames and e-mail addresses were also released; people were exhorted to "use and abuse these password lists and credit card information to wreak unholy havoc upon the systems and personal e-mail accounts of these rich and powerful oppressors."
It was vicious, and Stratfor has not in fact fully recovered. Critics of the action, like The Atlantic, called Stratfor a "joke" organization not worth targeting, though the hackers seemed more than pleased with their work; they recently passed the company e-mails to WikiLeaks for distribution.
Whatever else it did, the hack certainly brought renewed attention to hackers like sup_g. But first, the FBI had to find them.
While sup_g may indeed have been a "credible threat," he was in the end no match for the overwhelming federal resources of the FBI agents hunting him down. Over the last month, federal agents staked out his home in Chicago constantly, dug up old police surveillance records, tapped his Internet connection, used directional wireless finders to locate and identify his wireless router, and relied on Sabu back in his New York City apartment to let them know when sup_g went on or offline.
Despite his many precautions taken, the FBI moved into Chicago's Bridgeport neighborhood last night and arrested a 27-year old dreadlocked white guy said to hate racism so much that he had once violently attacked a Holocaust denier. Here's how the feds found him.
Details, details...
To identify sup_g, the Bureau first turned to the voluminous chat logs stored on Sabu's computer. They went through every comment that could be plausibly linked to sup_g or one of his aliases. The goal was to see if the hacker had slipped up at any point and revealed some personal information.
He had. On August 29, 2011 at 8:37 AM, "burn" said in an IRC channel that "some comrades of mine were arrested in St. Louis a few weeks ago... for midwestrising tar sands work." If accurate, this might place "burn" in the Midwest. FBI Chicago agents were able to confirm that an event called Midwest Rising was attended by Chicago resident Jeremy Hammond's twin brother. (Hammond had a history with anarchism and violent protest.)
"Anarchaos" once let slip that he had been arrested in 2004 for protesting at the Republican National Convention in New York City. Much later, "yohoho" noted that he hadn't been to New York "since the RNC," nicely tying both online handles to the same person. The FBI went to New York City police and obtained a list of every individual detained at the 2004 convention; they learned that Jeremy Hammond had in fact been detained, though he had not been arrested. The pieces were starting to fit.
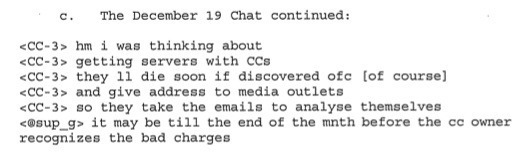
A captured portion of an IRC chat about using stolen credit cards to pay for new servers
"Sup_g" and "burn" both indicated later that they had spent time in prison, with “burn” indicating that he had been at a federal penitentiary. A search of Hammond's criminal records revealed that he had been arrested in March 2005 by the Chicago FBI and had pled guilty to hacking into a “politically conservative website and stealing its computer database, including credit card information,” according to an FBI affidavit. Hammond was sentenced to two years in prison for the action.
Before this 2005 arrest, Hammond had allegedly told friends in Chicago that he intended to use the credit card information from the hack to “make donations to liberal organizations.” Though he did not do so at the time, the idea matched up with the "lulzxmas" plan to distribute gifts and cash using stolen cards from Stratfor.
In yet another chat, "Anarchaos" told Sabu that he had once spent a few weeks in a county jail for possession of marijuana. He also asked Sabu not to tell anybody, “cause it could compromise my identity," and he noted that he was on probation. Both matched Hammond, who was placed on probation in November 2010 after a violent protest against the Olympics coming to Chicago. When the FBI ran a criminal history check on Hammond, it also revealed two arrests for marijuana possession.
The FBI was so thorough that it even followed up on a "POW" comment saying "dumpster diving is all good i'm a freegan goddess." ("Freegans" scavenge unspoiled, wasted food from the trash of grocery stores and restaurants.) The FBI went to Chicago authorities, who had put Hammond under surveillance when they were investigating him back in 2005. As part of that earlier surveillance, “agents have seen Hammond going into dumpsters to get food.”
Now that they had a suspect, it was time to put him under surveillance.
Expect us

The house on Chicago's south side where Hammond lived Credit: Google Maps
Convinced that they had identified the right suspect, agents began continuous physical surveillance of Hammond's two-apartment home on Chicago's South Side on February 29. Their target only used the side entrance to the building, which accessed the rear apartment; using a signal strength meter and directional antennas, FBI agents located his wireless router signal and were able to confirm that it was located in the back apartment.
Watching the WiFi network revealed the Media Access Control (MAC) addresses of each device connected to the network. Most of the time there was only one, an Apple Computer—and sup_g had told Sabu that he used a Macbook.

On March 1, the agents obtained a court order allowing them to use a "pen register/trap and trace" device that could reveal only "addressing information" and not content. In other words, if it worked, agents could see what IP addresses Hammond was visiting, but they would see nothing else.
The FBI describes its device as a "wireless router monitoring device” that captures addressing and signaling information and transmits it wirelessly through the air to FBI agents watching the home. It was installed the same day and was soon showing agents what Hammond was up to online.
His Macbook's MAC address was soon seen connecting to IP addresses known to be part of the Tor anonymizing network. "An FBI Tor network expert analyzed the data from the Pen/Trace and was able to determine that a significant portion of the traffic from the Chicago Residence to the Internet was Tor-related traffic,” said the FBI's affidavit.
And while this definitely sounded like their man, the Bureau went to even greater lengths to double-check their target. The main technique was to observe when Hammond left his home, then to call Sabu in New York and ask if any of Hammond's suspected aliases had just left IRC or the Jabber instant messaging system.
Here, for instance, are two such logs from March 1:
On March 1, 2012, at approximately 5:03 PM CST, Hammond was seen leaving the Chicago Residence. Almost immediately after, CW-1 (in New York) contacted me to report that the defendant was off-line. Pen/Trap data also reflected that Tor network activity and Internet activity from the Chicago Residence stopped at approximately the same time.
Later, also on March 1, 2012, at approximately 6:23 PM CST, Hammond was observed returning to the Chicago Residence. Tor Network traffic resumed from the Chicago Residence approximately a minute or so later. Moreover, CW-1 reported to me that the defendant, using the online alias “yohoho," was back online at approximately the same time as physical surveillance in Chicago showed Hammond had returned to the Chicago Residence.
Surveillance continued right up through March 4, when Sabu had his last online sighting of Hammond at 7:00pm CST. On March 5, the FBI drew up its finalized arrest affidavit and presented it to Judge Ronald Ellis in the lower Manhattan federal courthouse. Later that day, it was acted upon in Chicago.
Arrest and aftermath
Hammond was arrested last night. Residents of the Bridgeport neighborhood took to a Facebook group to figure out what was happening. "There is a big white truck outside now - the evidence wagon?" wrote one. "And more FBI agents." Another said he was told to go back inside and that the FBI had "some huge guns."
"There were a ton of FBI agents taking guys out of this house," said another. "At 8:00 at night. They weren't taking down a flag burner [some had speculated that it was due to Hammond's hippie, anarchic ways]. It's 11:00 now & there are 16 FBI vehicles still out here. I live across the street. I don't know who you're hearing stuff from - but this is BIG!"
"I asked the boyfriend to go out & see if he could get any more info," wrote a commenter. "The FBI guy said this will be out in the news tomorrow. Stay tuned."

A still from video of the FBI raid on Hammond's apartment Credit: Chicago Tribune
Hammond was back in the news—again. He was profiled back in 2007 by Chicago magazine as part of a piece on hacktivism. "That evening, I caught up with Hammond in front of the flower shop," wrote author Stuart Luman. "He bragged about a current scheme involving Kinko's cards, which he had hacked so they would grant free copies. He fanned the cards in front of me as if he were performing a magic trick. Then he pulled from his pocket a San Francisco Bay Area Rapid Transit pass. 'I can clone these so easily,' he boasted."
But Hammond's passion was social change. At a hacking meeetup profiled in the piece, Hammond tells his fellow hackers that he is driven by his hatred of social inequality. "Our civilization is facing a radical, imminent mass change," he said. "The alternative to the hierarchical power structure is based on mutual aid and group consensus. As hackers we can learn these systems, manipulate these systems, and shut down these systems if we need to."
Yesterday's arrest didn't appear to surprise him. As the Chicago Tribune reported, he appeared at a hearing today in federal court and was ordered off to New York to face the charges.
"After the hearing, as he stood in a narrow hallway, Hammond appeared curious," wrote reporters Todd Lighty and Wailin Wong. "He asked deputy marshals if he could keep a copy of the criminal complaint since he had no idea about the charges until his arrest Tuesday morning. His lawyer, James Fennerty, said he considers Hammond a likable man with strongly held beliefs."
Now, those beliefs could land him in serious trouble.


