Rotating your SSL/TLS certificate - Amazon Aurora (original) (raw)
Amazon RDS Certificate Authority certificates rds-ca-2019 expired in August, 2024. If you use or plan to use Secure Sockets Layer (SSL) or Transport Layer Security (TLS) with certificate verification to connect to your RDS DB instances , consider using one of the new CA certificates rds-ca-rsa2048-g1, rds-ca-rsa4096-g1 or rds-ca-ecc384-g1. If you currently do not use SSL/TLS with certificate verification, you might still have an expired CA certificate and must update them to a new CA certificate if you plan to use SSL/TLS with certificate verification to connect to your RDS databases.
Amazon RDS provides new CA certificates as an AWS security best practice. For information about the new certificates and the supported AWS Regions, seeUsing SSL/TLS to encrypt a connection to a DB cluster.
To update the CA certificate for your database, use the following methods:
- Updating your CA certificate by modifying your DB instance
- Updating your CA certificate by applying maintenance
Before you update your DB instances to use the new CA certificate, make sure that you update your clients or applications connecting to your RDS databases.
Considerations for rotating certificates
Consider the following situations before rotating your certificate:
- Amazon RDS Proxy and Aurora Serverless v1 use certificates from the AWS Certificate Manager (ACM). If you're using RDS Proxy, when you rotate your SSL/TLS certificate, you don't need to update applications that use RDS Proxy connections. For more information, seeUsing TLS/SSL with RDS Proxy.
- If you're using Aurora Serverless v1, downloading Amazon RDS certificates isn't required. For more information, see Using TLS/SSL with Aurora Serverless v1.
- If you're using a Go version 1.15 application with a DB instance that was created or updated to the rds-ca-2019 certificate prior to July 28, 2020, you must update the certificate again. Update the certificate tords-ca-rsa2048-g1, rds-ca-rsa4096-g1, or rds-ca-ecc384-g1 depending on your engine.
Use themodify-db-instancecommand , using the new CA certificate identifier. You can find the CAs that are available for a specific DB engine and DB engine version using thedescribe-db-engine-versionscommand.
If you created your database or updated its certificate after July 28, 2020, no action is required. For more information, see Go GitHub issue #39568.
Updating your CA certificate by modifying your DB instance
The following example updates your CA certificate from_rds-ca-2019_ to_rds-ca-rsa2048-g1_. You can choose a different certificate. For more information, see Certificate authorities.
Update your application trust store to reduce any down time associated with updating your CA certificate. For more information about restarts associated with CA certificate rotation, see Automatic server certificate rotation.
To update your CA certificate by modifying your DB instance
- Download the new SSL/TLS certificate as described in Using SSL/TLS to encrypt a connection to a DB cluster.
- Update your applications to use the new SSL/TLS certificate.
The methods for updating applications for new SSL/TLS certificates depend on your specific applications. Work with your application developers to update the SSL/TLS certificates for your applications.
For information about checking for SSL/TLS connections and updating applications for each DB engine, see the following topics:- Updating applications to connect to Aurora MySQL DB clusters using new TLS certificates
- Updating applications to connect to Aurora PostgreSQL DB clusters using new SSL/TLS certificates
For a sample script that updates a trust store for a Linux operating system, see Sample script for importing certificates into your trust store.
Note
The certificate bundle contains certificates for both the old and new CA, so you can upgrade your application safely and maintain connectivity during the transition period. If you are using the AWS Database Migration Service to migrate a database to a DB cluster, we recommend using the certificate bundle to ensure connectivity during the migration.
3. Modify the DB instance to change the CA fromrds-ca-2019 tords-ca-rsa2048-g1. To check if your database requires a restart to update the CA certificates, use thedescribe-db-engine-versions command and check theSupportsCertificateRotationWithoutRestart flag.
Note
Reboot your Babelfish cluster after modifying to update the CA certificate.
Important
If you are experiencing connectivity issues after certificate expiry, use the apply immediately option by specifyingApply immediately in the console or by specifying the --apply-immediately option using the AWS CLI. By default, this operation is scheduled to run during your next maintenance window.
To set an override for your cluster CA that's different from the default RDS CA, use the modify-certificates CLI command.
You can use the AWS Management Console or the AWS CLI to change the CA certificate fromrds-ca-2019 tords-ca-rsa2048-g1 for a DB instance .
Console
- Sign in to the AWS Management Console and open the Amazon RDS console athttps://console.aws.amazon.com/rds/.
- In the navigation pane, chooseDatabases, and then choose the DB instance that you want to modify.
- Choose Modify.
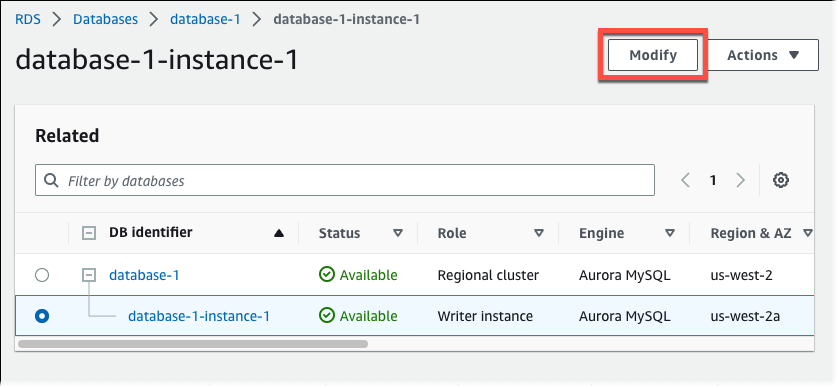
- In the Connectivity section, choose rds-ca-rsa2048-g1.
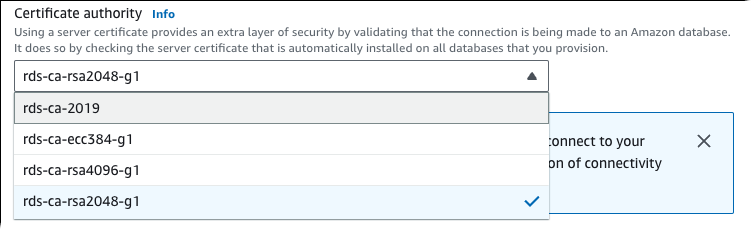
- Choose Continue and check the summary of modifications.
- To apply the changes immediately, chooseApply immediately.
- On the confirmation page, review your changes. If they are correct, choose Modify DB Instance to save your changes.
Important
When you schedule this operation, make sure that you have updated your client-side trust store beforehand.
Or choose Back to edit your changes or Cancel to cancel your changes.
AWS CLI
To use the AWS CLI to change the CA fromrds-ca-2019 tords-ca-rsa2048-g1 for a DB instance , call themodify-db-instance or modify-db-cluster command. Specify the DB instance identifier and the --ca-certificate-identifier option.
Use the --apply-immediately parameter to apply the update immediately. By default, this operation is scheduled to run during your next maintenance window.
Important
When you schedule this operation, make sure that you have updated your client-side trust store beforehand.
The following example modifies mydbinstance by setting the CA certificate tords-ca-rsa2048-g1.
For Linux, macOS, or Unix:
aws rds modify-db-instance \
--db-instance-identifier mydbinstance \
--ca-certificate-identifier rds-ca-rsa2048-g1 For Windows:
aws rds modify-db-instance ^
--db-instance-identifier mydbinstance ^
--ca-certificate-identifier rds-ca-rsa2048-g1Note
If your instance requires reboot, you can use themodify-db-instance CLI command and specify the --no-certificate-rotation-restart option.
Updating your CA certificate by applying maintenance
Perform the following steps to update your CA certificate by applying maintenance.
Console
To update your CA certificate by applying maintenance
- Sign in to the AWS Management Console and open the Amazon RDS console athttps://console.aws.amazon.com/rds/.
- In the navigation pane, choose Certificate update.

The Databases requiring certificate update page appears.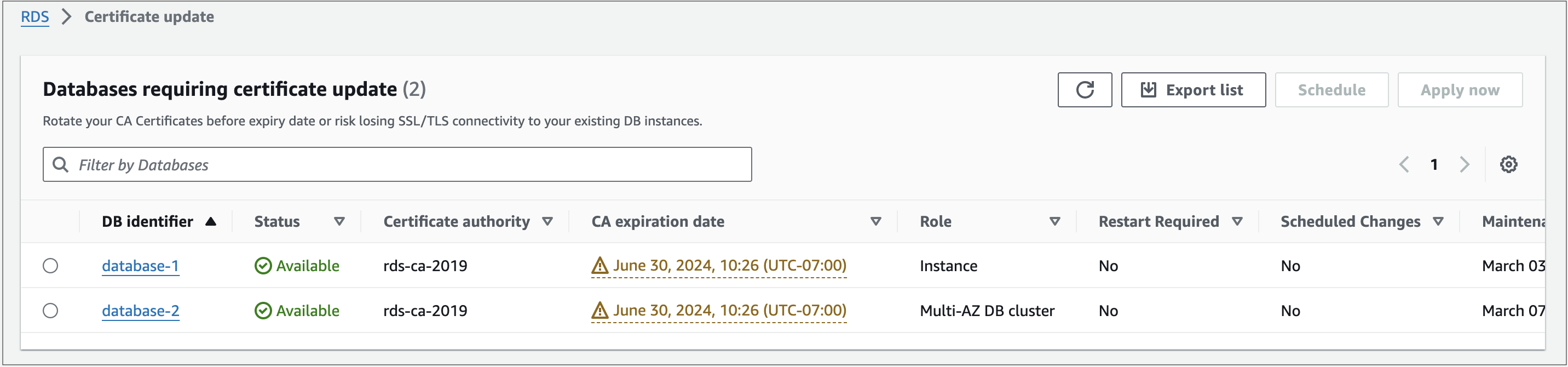
Note
This page only shows the DB instances for the current AWS Region. If you have databases in more than one AWS Region, check this page in each AWS Region to see all DB instances with old SSL/TLS certificates.
3. Choose the DB instance that you want to update.
You can schedule the certificate rotation for your next maintenance window by choosingSchedule. Apply the rotation immediately by choosing Apply now.
Important
If you experience connectivity issues after certificate expiry, use the Apply now option.
4. 1. If you choose Schedule, you are prompted to confirm the CA certificate rotation. This prompt also states the scheduled window for your update.
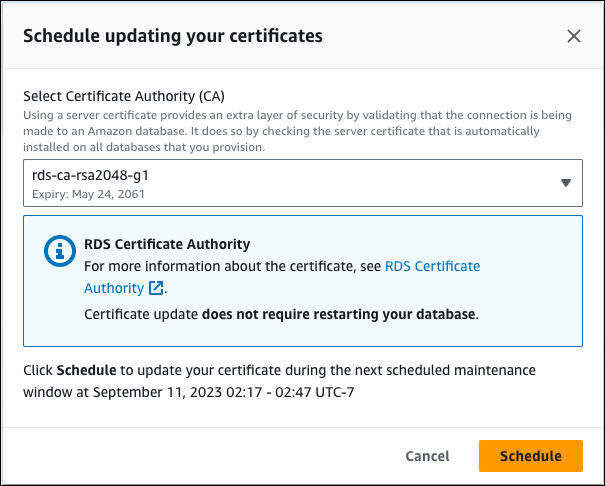
2. If you choose Apply now, you are prompted to confirm the CA certificate rotation.
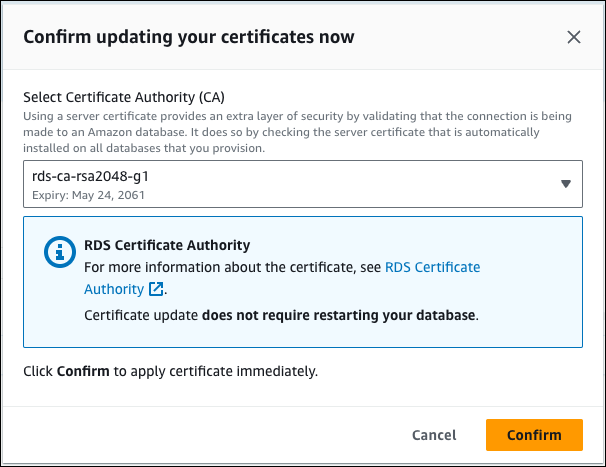
Important
Before scheduling the CA certificate rotation on your database, update any client applications that use SSL/TLS and the server certificate to connect. These updates are specific to your DB engine. After you have updated these client applications, you can confirm the CA certificate rotation.
To continue, choose the check box, and then chooseConfirm.
5. Repeat steps 3 and 4 for each DB instance that you want to update.
Automatic server certificate rotation
If your root CA supports automatic server certificate rotation, RDS automatically handles the rotation of the DB server certificate. RDS uses the same root CA for this automatic rotation, so you don't need to download a new CA bundle. See Certificate authorities.
The rotation and validity of your DB server certificate depend on your DB engine:
- If your DB engine supports rotation without restart, RDS automatically rotates the DB server certificate without requiring any action from you. RDS attempts to rotate your DB server certificate in your preferred maintenance window at the DB server certificate half life. The new DB server certificate is valid for 12 months.
- If your DB engine doesn't support rotation without restart, RDS notifies you about a maintenance event at least 6 months before the DB server certificate expires. The new DB server certificate is valid for 36 months.
Use the describe-db-engine-versions command and inspect theSupportsCertificateRotationWithoutRestart flag to identify whether the DB engine version supports rotating the certificate without restart. For more information, see Setting the CA for your database.
Sample script for importing certificates into your trust store
The following are sample shell scripts that import the certificate bundle into a trust store.
Each sample shell script uses keytool, which is part of the Java Development Kit (JDK). For information about installing the JDK, see JDK Installation Guide.
Linux
The following is a sample shell script that imports the certificate bundle into a trust store on a Linux operating system.
mydir=tmp/certs
if [ ! -e "${mydir}" ]
then
mkdir -p "${mydir}"
fi
truststore=${mydir}/rds-truststore.jks
storepassword=changeit
curl -sS "https://truststore.pki.rds.amazonaws.com/global/global-bundle.pem" > ${mydir}/global-bundle.pem
awk 'split_after == 1 {n++;split_after=0} /-----END CERTIFICATE-----/ {split_after=1}{print > "rds-ca-" n+1 ".pem"}' < ${mydir}/global-bundle.pem
for CERT in rds-ca-*; do
alias=$(openssl x509 -noout -text -in $CERT | perl -ne 'next unless /Subject:/; s/.*(CN=|CN = )//; print')
echo "Importing $alias"
keytool -import -file <span class="katex"><span class="katex-mathml"><math xmlns="http://www.w3.org/1998/Math/MathML"><semantics><mrow><mrow><mi>C</mi><mi>E</mi><mi>R</mi><mi>T</mi></mrow><mo>−</mo><mi>a</mi><mi>l</mi><mi>i</mi><mi>a</mi><mi>s</mi><mi mathvariant="normal">"</mi></mrow><annotation encoding="application/x-tex">{CERT} -alias "</annotation></semantics></math></span><span class="katex-html" aria-hidden="true"><span class="base"><span class="strut" style="height:0.7667em;vertical-align:-0.0833em;"></span><span class="mord"><span class="mord mathnormal" style="margin-right:0.13889em;">CERT</span></span><span class="mspace" style="margin-right:0.2222em;"></span><span class="mbin">−</span><span class="mspace" style="margin-right:0.2222em;"></span></span><span class="base"><span class="strut" style="height:0.6944em;"></span><span class="mord mathnormal">a</span><span class="mord mathnormal" style="margin-right:0.01968em;">l</span><span class="mord mathnormal">ia</span><span class="mord mathnormal">s</span><span class="mord">"</span></span></span></span>{alias}" -storepass <span class="katex"><span class="katex-mathml"><math xmlns="http://www.w3.org/1998/Math/MathML"><semantics><mrow><mrow><mi>s</mi><mi>t</mi><mi>o</mi><mi>r</mi><mi>e</mi><mi>p</mi><mi>a</mi><mi>s</mi><mi>s</mi><mi>w</mi><mi>o</mi><mi>r</mi><mi>d</mi></mrow><mo>−</mo><mi>k</mi><mi>e</mi><mi>y</mi><mi>s</mi><mi>t</mi><mi>o</mi><mi>r</mi><mi>e</mi></mrow><annotation encoding="application/x-tex">{storepassword} -keystore </annotation></semantics></math></span><span class="katex-html" aria-hidden="true"><span class="base"><span class="strut" style="height:0.8889em;vertical-align:-0.1944em;"></span><span class="mord"><span class="mord mathnormal">s</span><span class="mord mathnormal">t</span><span class="mord mathnormal">ore</span><span class="mord mathnormal">p</span><span class="mord mathnormal">a</span><span class="mord mathnormal">ss</span><span class="mord mathnormal" style="margin-right:0.02691em;">w</span><span class="mord mathnormal" style="margin-right:0.02778em;">or</span><span class="mord mathnormal">d</span></span><span class="mspace" style="margin-right:0.2222em;"></span><span class="mbin">−</span><span class="mspace" style="margin-right:0.2222em;"></span></span><span class="base"><span class="strut" style="height:0.8889em;vertical-align:-0.1944em;"></span><span class="mord mathnormal" style="margin-right:0.03148em;">k</span><span class="mord mathnormal">eys</span><span class="mord mathnormal">t</span><span class="mord mathnormal">ore</span></span></span></span>{truststore} -noprompt
rm $CERT
done
rm ${mydir}/global-bundle.pem
echo "Trust store content is: "
keytool -list -v -keystore "$truststore" -storepass ${storepassword} | grep Alias | cut -d " " -f3- | while read alias
do
expiry=`keytool -list -v -keystore "$truststore" -storepass <span class="katex"><span class="katex-mathml"><math xmlns="http://www.w3.org/1998/Math/MathML"><semantics><mrow><mrow><mi>s</mi><mi>t</mi><mi>o</mi><mi>r</mi><mi>e</mi><mi>p</mi><mi>a</mi><mi>s</mi><mi>s</mi><mi>w</mi><mi>o</mi><mi>r</mi><mi>d</mi></mrow><mo>−</mo><mi>a</mi><mi>l</mi><mi>i</mi><mi>a</mi><mi>s</mi><mi mathvariant="normal">"</mi></mrow><annotation encoding="application/x-tex">{storepassword} -alias "</annotation></semantics></math></span><span class="katex-html" aria-hidden="true"><span class="base"><span class="strut" style="height:0.8889em;vertical-align:-0.1944em;"></span><span class="mord"><span class="mord mathnormal">s</span><span class="mord mathnormal">t</span><span class="mord mathnormal">ore</span><span class="mord mathnormal">p</span><span class="mord mathnormal">a</span><span class="mord mathnormal">ss</span><span class="mord mathnormal" style="margin-right:0.02691em;">w</span><span class="mord mathnormal" style="margin-right:0.02778em;">or</span><span class="mord mathnormal">d</span></span><span class="mspace" style="margin-right:0.2222em;"></span><span class="mbin">−</span><span class="mspace" style="margin-right:0.2222em;"></span></span><span class="base"><span class="strut" style="height:0.6944em;"></span><span class="mord mathnormal">a</span><span class="mord mathnormal" style="margin-right:0.01968em;">l</span><span class="mord mathnormal">ia</span><span class="mord mathnormal">s</span><span class="mord">"</span></span></span></span>{alias}" | grep Valid | perl -ne 'if(/until: (.*?)\n/) { print "$1\n"; }'`
echo " Certificate <span class="katex"><span class="katex-mathml"><math xmlns="http://www.w3.org/1998/Math/MathML"><semantics><mrow><mrow><mi>a</mi><mi>l</mi><mi>i</mi><mi>a</mi><mi>s</mi></mrow><mi>e</mi><mi>x</mi><mi>p</mi><mi>i</mi><mi>r</mi><mi>e</mi><mi>s</mi><mi>i</mi><msup><mi>n</mi><mo mathvariant="normal" lspace="0em" rspace="0em">′</mo></msup></mrow><annotation encoding="application/x-tex">{alias} expires in '</annotation></semantics></math></span><span class="katex-html" aria-hidden="true"><span class="base"><span class="strut" style="height:0.9463em;vertical-align:-0.1944em;"></span><span class="mord"><span class="mord mathnormal">a</span><span class="mord mathnormal" style="margin-right:0.01968em;">l</span><span class="mord mathnormal">ia</span><span class="mord mathnormal">s</span></span><span class="mord mathnormal">e</span><span class="mord mathnormal">x</span><span class="mord mathnormal">p</span><span class="mord mathnormal">i</span><span class="mord mathnormal">res</span><span class="mord mathnormal">i</span><span class="mord"><span class="mord mathnormal">n</span><span class="msupsub"><span class="vlist-t"><span class="vlist-r"><span class="vlist" style="height:0.7519em;"><span style="top:-3.063em;margin-right:0.05em;"><span class="pstrut" style="height:2.7em;"></span><span class="sizing reset-size6 size3 mtight"><span class="mord mtight"><span class="mord mtight">′</span></span></span></span></span></span></span></span></span></span></span></span>expiry'"
done
macOS
The following is a sample shell script that imports the certificate bundle into a trust store on macOS.
mydir=tmp/certs
if [ ! -e "${mydir}" ]
then
mkdir -p "${mydir}"
fi
truststore=${mydir}/rds-truststore.jks
storepassword=changeit
curl -sS "https://truststore.pki.rds.amazonaws.com/global/global-bundle.pem" > ${mydir}/global-bundle.pem
split -p "-----BEGIN CERTIFICATE-----" ${mydir}/global-bundle.pem rds-ca-
for CERT in rds-ca-*; do
alias=$(openssl x509 -noout -text -in $CERT | perl -ne 'next unless /Subject:/; s/.*(CN=|CN = )//; print')
echo "Importing $alias"
keytool -import -file <span class="katex"><span class="katex-mathml"><math xmlns="http://www.w3.org/1998/Math/MathML"><semantics><mrow><mrow><mi>C</mi><mi>E</mi><mi>R</mi><mi>T</mi></mrow><mo>−</mo><mi>a</mi><mi>l</mi><mi>i</mi><mi>a</mi><mi>s</mi><mi mathvariant="normal">"</mi></mrow><annotation encoding="application/x-tex">{CERT} -alias "</annotation></semantics></math></span><span class="katex-html" aria-hidden="true"><span class="base"><span class="strut" style="height:0.7667em;vertical-align:-0.0833em;"></span><span class="mord"><span class="mord mathnormal" style="margin-right:0.13889em;">CERT</span></span><span class="mspace" style="margin-right:0.2222em;"></span><span class="mbin">−</span><span class="mspace" style="margin-right:0.2222em;"></span></span><span class="base"><span class="strut" style="height:0.6944em;"></span><span class="mord mathnormal">a</span><span class="mord mathnormal" style="margin-right:0.01968em;">l</span><span class="mord mathnormal">ia</span><span class="mord mathnormal">s</span><span class="mord">"</span></span></span></span>{alias}" -storepass <span class="katex"><span class="katex-mathml"><math xmlns="http://www.w3.org/1998/Math/MathML"><semantics><mrow><mrow><mi>s</mi><mi>t</mi><mi>o</mi><mi>r</mi><mi>e</mi><mi>p</mi><mi>a</mi><mi>s</mi><mi>s</mi><mi>w</mi><mi>o</mi><mi>r</mi><mi>d</mi></mrow><mo>−</mo><mi>k</mi><mi>e</mi><mi>y</mi><mi>s</mi><mi>t</mi><mi>o</mi><mi>r</mi><mi>e</mi></mrow><annotation encoding="application/x-tex">{storepassword} -keystore </annotation></semantics></math></span><span class="katex-html" aria-hidden="true"><span class="base"><span class="strut" style="height:0.8889em;vertical-align:-0.1944em;"></span><span class="mord"><span class="mord mathnormal">s</span><span class="mord mathnormal">t</span><span class="mord mathnormal">ore</span><span class="mord mathnormal">p</span><span class="mord mathnormal">a</span><span class="mord mathnormal">ss</span><span class="mord mathnormal" style="margin-right:0.02691em;">w</span><span class="mord mathnormal" style="margin-right:0.02778em;">or</span><span class="mord mathnormal">d</span></span><span class="mspace" style="margin-right:0.2222em;"></span><span class="mbin">−</span><span class="mspace" style="margin-right:0.2222em;"></span></span><span class="base"><span class="strut" style="height:0.8889em;vertical-align:-0.1944em;"></span><span class="mord mathnormal" style="margin-right:0.03148em;">k</span><span class="mord mathnormal">eys</span><span class="mord mathnormal">t</span><span class="mord mathnormal">ore</span></span></span></span>{truststore} -noprompt
rm $CERT
done
rm ${mydir}/global-bundle.pem
echo "Trust store content is: "
keytool -list -v -keystore "$truststore" -storepass ${storepassword} | grep Alias | cut -d " " -f3- | while read alias
do
expiry=`keytool -list -v -keystore "$truststore" -storepass <span class="katex"><span class="katex-mathml"><math xmlns="http://www.w3.org/1998/Math/MathML"><semantics><mrow><mrow><mi>s</mi><mi>t</mi><mi>o</mi><mi>r</mi><mi>e</mi><mi>p</mi><mi>a</mi><mi>s</mi><mi>s</mi><mi>w</mi><mi>o</mi><mi>r</mi><mi>d</mi></mrow><mo>−</mo><mi>a</mi><mi>l</mi><mi>i</mi><mi>a</mi><mi>s</mi><mi mathvariant="normal">"</mi></mrow><annotation encoding="application/x-tex">{storepassword} -alias "</annotation></semantics></math></span><span class="katex-html" aria-hidden="true"><span class="base"><span class="strut" style="height:0.8889em;vertical-align:-0.1944em;"></span><span class="mord"><span class="mord mathnormal">s</span><span class="mord mathnormal">t</span><span class="mord mathnormal">ore</span><span class="mord mathnormal">p</span><span class="mord mathnormal">a</span><span class="mord mathnormal">ss</span><span class="mord mathnormal" style="margin-right:0.02691em;">w</span><span class="mord mathnormal" style="margin-right:0.02778em;">or</span><span class="mord mathnormal">d</span></span><span class="mspace" style="margin-right:0.2222em;"></span><span class="mbin">−</span><span class="mspace" style="margin-right:0.2222em;"></span></span><span class="base"><span class="strut" style="height:0.6944em;"></span><span class="mord mathnormal">a</span><span class="mord mathnormal" style="margin-right:0.01968em;">l</span><span class="mord mathnormal">ia</span><span class="mord mathnormal">s</span><span class="mord">"</span></span></span></span>{alias}" | grep Valid | perl -ne 'if(/until: (.*?)\n/) { print "$1\n"; }'`
echo " Certificate <span class="katex"><span class="katex-mathml"><math xmlns="http://www.w3.org/1998/Math/MathML"><semantics><mrow><mrow><mi>a</mi><mi>l</mi><mi>i</mi><mi>a</mi><mi>s</mi></mrow><mi>e</mi><mi>x</mi><mi>p</mi><mi>i</mi><mi>r</mi><mi>e</mi><mi>s</mi><mi>i</mi><msup><mi>n</mi><mo mathvariant="normal" lspace="0em" rspace="0em">′</mo></msup></mrow><annotation encoding="application/x-tex">{alias} expires in '</annotation></semantics></math></span><span class="katex-html" aria-hidden="true"><span class="base"><span class="strut" style="height:0.9463em;vertical-align:-0.1944em;"></span><span class="mord"><span class="mord mathnormal">a</span><span class="mord mathnormal" style="margin-right:0.01968em;">l</span><span class="mord mathnormal">ia</span><span class="mord mathnormal">s</span></span><span class="mord mathnormal">e</span><span class="mord mathnormal">x</span><span class="mord mathnormal">p</span><span class="mord mathnormal">i</span><span class="mord mathnormal">res</span><span class="mord mathnormal">i</span><span class="mord"><span class="mord mathnormal">n</span><span class="msupsub"><span class="vlist-t"><span class="vlist-r"><span class="vlist" style="height:0.7519em;"><span style="top:-3.063em;margin-right:0.05em;"><span class="pstrut" style="height:2.7em;"></span><span class="sizing reset-size6 size3 mtight"><span class="mord mtight"><span class="mord mtight">′</span></span></span></span></span></span></span></span></span></span></span></span>expiry'"
done
To learn more best practices about using SSL with Amazon RDS, see Best practices for successful SSL connections to Amazon RDS for Oracle.