Jetson was not booting after UEFI secure boot + DiskEncryption (original) (raw)
Hello,
I’m implementing UEFI secure boot and Disk encryption on Jetson AGX Xavier. I’ve followed the steps mentioned in the documentation. After flashing with rootfs encryption and UEFI secure boot with eks image, jetson was failed at L4T launcher loading kernel.
Please review the system configuration and steps I followed.
Host OS : Ubuntu 22.0
Board : Jetson AGX Xavier
Version : V35.6.1
Step1 : Generating the UEFI keys.
$ cd to <LDK_DIR>
$ mkdir uefi_keys
$ cd uefi_keys
### Generate PK RSA keypair and certificate
$ openssl req -newkey rsa:2048 -nodes -keyout PK.key -new -x509 -sha256 -days 3650 -subj "/CN=my Platform Key/" -out PK.crt
### Generate KEK RSA keypair and certificate
$ openssl req -newkey rsa:2048 -nodes -keyout KEK.key -new -x509 -sha256 -days 3650 -subj "/CN=my Key Exchange Key/" -out KEK.crt
### Generate db_1 RSA keypair and certificate
$ openssl req -newkey rsa:2048 -nodes -keyout db_1.key -new -x509 -sha256 -days 3650 -subj "/CN=my Signature Database key/" -out db_1.crt
### Generate db_2 RSA keypair and certificate
$ openssl req -newkey rsa:2048 -nodes -keyout db_2.key -new -x509 -sha256 -days 3650 -subj "/CN=my another Signature Database key/" -out db_2.crt
Step 2: creating a UEFI_keys config file$ vim uefi_keys.conf
step 3: creating UefiDefaultSecurityKeys.dtbo.
Qes: Do I need to copy this generated device tree blob to /bootloader/.. path?
Edit: copied UefiDefaultSecurityKeys.dtbo to /bootloader path and flashed the system again. Boot was unsuccessful.
$ cd ..
$ sudo tools/gen_uefi_default_keys_dts.sh uefi_keys/uefi_keys.conf
$ sudo chmod 644 uefi_keys/_out/*.auth
step4: EKB image generation.
For eks_t194.img file I have prepared the custom keys fv, kek2, sym1_t194.key, sym2_t194.keys using openssl.
Note: I have generated the fv_for_ekb, fv_for_ssk_dk and replace the same in the optee/optee_os/core/pta/tegra/jetson_user_key_ptc.c as it mentioned in the OP-TEE: Open Portable Trusted Execution Environment — NVIDIA Jetson Linux Developer Guide 1 documentation. Now I’m using the same fv_for_ekb key in the gen_ekb.py script command.
then I run this command
python3 gen_ekb.py \
-chip t194 \
-kek2_key kek2.key \
-fv fv.key \
-in_sym_key sym1_t194.key \
-in_sym_key2 sym2_t194.key \
-out eks_t194.img
Then copied the generated eks image file to bootloader path.cp eks_t194.img bootloader/eks_t194.img
step 5: Flashing Jetson board.
sudo ROOTFS_ENC=1 ./flash.sh --no-flash -i ./sym2_t194.key -u rsa_priv.pem -v ./sbk.key jetson-xavier mmcblk0p1
cd bootloader
sudo bash ./flashcmd.txt
Note : I’ve already implemented secure boot and fused keys into hardware. I’m facing these errors after encrypting the rootfs and UEFI secure boot.
Edit: When I only implement the secure boot and flash the system. System boots without any errors.
Could you let me know if I have missed any steps? and I’m attaching the flash logs for review.
flash_log.txt (104.5 KB)
I’d really appreciate your help.
Thanks
Vamsi.
Hello
To narrow down the problem. I have separated UEFI secure boot and Disk encryption and UEFI payload encryption.
I have successfully enable the UEFI secure boot.
The cmd I have used:sudo ./flash.sh --generic-passphrase --no-flash -u /home/vamsi/Desktop/keys/rsa_priv.pem -v /home/vamsi/Desktop/keys/sbk.key --uefi-keys /home/vamsi/nvidia/Linux_for_Tegra/uefi_keys/uefi_keys.conf jetson-xavier mmcblk0p1
The same rsa_priv.pem key was used in secure boot enable.
- UEFI payload encryption
Now coming to the issue. I could able to generate the EKB image using
sudo python3 gen_ekb.py -chip t194 -kek2_key /home/vamsi/Desktop/keys/kek2.key -fv /home/vamsi/nvidia/Linux_for_Tegra/uefi_keys/FV_for_ekb.key -in_sym_key /home/vamsi/nvidia/Linux_for_Tegra/uefi_keys/sym1_t194.key -in_sym_key2 /home/vamsi/nvidia/Linux_for_Tegra/uefi_keys/sym2_t194.key -out eks_t194.img
Note: fv key was randomly genrated using the openssl.
Ques: Is, this generated key and the keys at this path optee/optee_os/core/pta/tegra/jetson_user_key_ptc.c should be same?
Similarly generated the sym1_t194.key and sym2_t194.keys.
all the paths were properly set and generated the eks image using the python script. I have used cp command to copy image file into the /bootlaoder path and also verified that the file was latest and updated.
It seems like the EKS image that I’m generated is either not working properly or no placed into the boot loader path properly.
For EKS image generation I even used the user_key i.e (sym1_t194.key) with all zero’s. This approach is also didn’t worked.
Flash cmd I have used for UEFI payload encryptionsudo ./flash.sh --generic-passphrase --no-flash -u /home/vamsi/Desktop/keys/rsa_priv.pem -v /home/vamsi/Desktop/keys/sbk.key --uefi-keys /home/vamsi/nvidia/Linux_for_Tegra/uefi_keys/uefi_keys.conf --uefi-enc /home/vamsi/nvidia/Linux_for_Tegra/uefi_keys/sym1_t194.key jetson-xavier mmcblk0p1
Error: Failed to boot Kernel and keep on resetting the system again and again.
I’m thinking, once UEFI payload encryption was successful, I could do the rootfs encryption too, as both required the EKB generation.
Any suggestions or modifications are greatly appreciated.
thanks
Vamsi.
hello v_vuyyuru,
it looks the failure with disk encryption.
you must update the fv_for_ekb[], please update op-tee binaries, and also tos.img for using customize FVs.
please also setup serial console, we’ll need to dig into the bootloader logs for details.
Hello @JerryChang ,
Thanks for the reply.
I have followed these methods:
- I’ve modified the fv key back to original one in
fv_for_ekb[]. Now, there is no change in fv key, so I did not build the opee source.
generated the EKS image and flashed with UEFI payload + Disk encryption. Boot was failed with folowing errors.
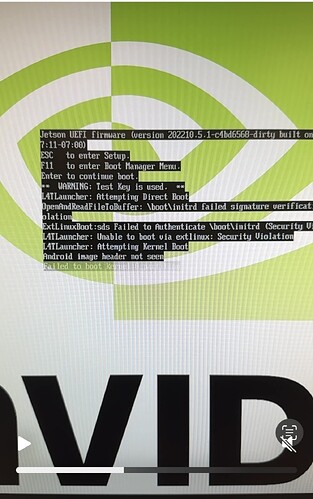
Jetson UEFI firmware (version 202210.5.1-c4bd6568-dirty built on 2025-04-28T12:3
7:11-07:00)
ESC to enter Setup.
F11 to enter Boot Manager Menu.
Enter to continue boot.
** WARNING: Test Key is used. **
L4TLauncher: Attempting Direct Boot
OpenAndReadFileToBuffer: \boot\initrd failed signature verification: Security Vi
olation
ExtLinuxBoot:sds Failed to Authenticate \boot\initrd (Security Violation)
L4TLauncher: Unable to boot via extlinux: Security Violation
L4TLauncher: Attempting Kernel Boot
Synchronous Exception at 0x000000086CDF8320
Method 2: modify the fv key with random generated and replace the key in the fv_for_ekb and build the optee sources and tos.img file. Still boot was unsuccessful.
Jetson UEFI firmware (version 202210.5.1-c4bd6568-dirty built on 2025-04-28T12:3
7:11-07:00)
ESC to enter Setup.
F11 to enter Boot Manager Menu.
Enter to continue boot.
** WARNING: Test Key is used. **
L4TLauncher: Attempting Direct Boot
OpenAndReadFileToBuffer: \boot\initrd failed signature verification: Security Vi
olation
ExtLinuxBoot:sds Failed to Authenticate \boot\initrd (Security Violation)
L4TLauncher: Unable to boot via extlinux: Security Violation
L4TLauncher: Attempting Kernel Boot
Synchronous Exception at 0x000000086CDF8320
/////system restarts here again
Jetson UEFI firmware (version 202210.5.1-c4bd6568-dirty built on 2025-04-28T12:3
7:11-07:00)
ESC to enter Setup.
F11 to enter Boot Manager Menu.
Enter to continue boot.
** WARNING: Test Key is used. **
L4TLauncher: Attempting Recovery Boot
Header not seen
Failed to boot recovery:0 partition
>>Start PXE over IPv4.
This is the successful bootloader log after I flashed the system by enabling the UEFI secure boot.
Jetson UEFI firmware (version 202210.5.1-c4bd6568-dirty built on 2025-04-28T12:3
7:11-07:00)
ESC to enter Setup.
F11 to enter Boot Manager Menu.
Enter to continue boot.
** WARNING: Test Key is used. **
L4TLauncher: Attempting Direct Boot
EFI stub: Booting Linux Kernel...
EFI stub: UEFI Secure Boot is enabled.
EFI stub: Using DTB from configuration table
EFI stub: Loaded initrd from LINUX_EFI_INITRD_MEDIA_GUID device path
EFI stub: Exiting boot services and installing virtual address map...
I’m getting this problem when I enable the Disk encryption+ UEFI payload encryption. could you review the EKS image generation command :
sudo python3 gen_ekb.py -chip t194 -kek2_key /home/vamsi/Desktop/keys/kek2.key -fv /home/vamsi/nvidia/Linux_for_Tegra/uefi_keys/FV_for_ekb.key -in_sym_key /home/vamsi/nvidia/Linux_for_Tegra/uefi_keys/sym1_t194.key -in_sym_key2 /home/vamsi/nvidia/Linux_for_Tegra/uefi_keys/sym2_t194.key -out eks_t194.img
flash command
# rootfs encryption + UEFI secure boot
sudo ROOTFS_ENC=1 ./flash.sh --generic-passphrase --no-flash -i /home/vamsi/nvidia/Linux_for_Tegra/uefi_keys/sym2_t194.key -u /home/vamsi/Desktop/keys/rsa_priv.pem -v /home/vamsi/Desktop/keys/sbk.key --uefi-keys /home/vamsi/nvidia/Linux_for_Tegra/uefi_keys/uefi_keys.conf --uefi-enc /home/vamsi/nvidia/Linux_for_Tegra/uefi_keys/sym1_t194.key jetson-xavier mmcblk0p1
is this issue related to keys mismatch?
I’d appreciate your help
Thanks
Vamsi.
hello v_vuyyuru,
we’ve also tested locally, it’s confirmed.. bootloader Secureboot + UEFI Secureboot (uefi-keys) + UEFI payload encryption (uefi-enc) + Disk Encryption (ROOTFS_ENC) is working on SBKPKC fused Jetson AGX-Xavier on JP-5.1.5/r35.6.1
here’s the flash command-line we’re using.$ sudo ROOTFS_ENC=1 ./flash.sh -u rsa_priv.pem -v sbk.key -i ./sym2_t194.key --uefi-keys ./uefi_keys/uefi_keys.conf --uefi-enc ./uefi_keys/sym_t194.key jetson-agx-xavier-devkit mmcblk0p1
please double check you’re using the same “sym2_t194.key” and “sym_t194.key” keys to generate EKS image, eks_t194.img.