A Review of Methods for Estimating Algorithmic Complexity: Options, Challenges, and New Directions - PubMed (original) (raw)
Review
A Review of Methods for Estimating Algorithmic Complexity: Options, Challenges, and New Directions
Hector Zenil. Entropy (Basel). 2020.
Abstract
Some established and also novel techniques in the field of applications of algorithmic (Kolmogorov) complexity currently co-exist for the first time and are here reviewed, ranging from dominant ones such as statistical lossless compression to newer approaches that advance, complement and also pose new challenges and may exhibit their own limitations. Evidence suggesting that these different methods complement each other for different regimes is presented and despite their many challenges, some of these methods can be better motivated by and better grounded in the principles of algorithmic information theory. It will be explained how different approaches to algorithmic complexity can explore the relaxation of different necessary and sufficient conditions in their pursuit of numerical applicability, with some of these approaches entailing greater risks than others in exchange for greater relevance. We conclude with a discussion of possible directions that may or should be taken into consideration to advance the field and encourage methodological innovation, but more importantly, to contribute to scientific discovery. This paper also serves as a rebuttal of claims made in a previously published minireview by another author, and offers an alternative account.
Keywords: Kolmogorov complexity; Lempel–Ziv–Welch (LZW); Shannon entropy; algorithmic complexity; block decomposition method; causality v correlation; coding theorem method; lossless compression; practical feasibility; rebuttal to Paul Vitányi’s review.
Conflict of interest statement
The author declares no conflict of interest.
Figures
Figure 1
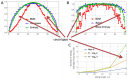
(A) An observer trying to characterise an observed stream of data (s) of unknown source (in this case, the sequence of natural numbers in decimal or binary that the observer may not recognise) has currently two options: (B) the statistical compression approach (green arrow) represented by run-length encoding (RLE), producing a rather cryptic and even longer description than the original observation with no clear correspondence between possible ground and represented states; or alternatively, (C) an approach that takes on the challenge as in an inverse problem represented by the Coding theorem method (CTM) (green arrow) that allows finding the set of small computer programs according to some reference machine up to a certain size that match their output to the original observation thereby potentially reverse engineering of the generating mechanism that may have recursively produced the sequence in the first place. (D) Such an approach allows a state space description represented by a generative rule or transition table and a state diagram whose elements may correspond (or not) to a physical unfolding phenomenon against which it can be tested (notice that the binary to decimal Turing machines (TM) is also of a finite, small size and is only an intermediate step to arrive at s, but can be one of the engines behind it; here, for illustration purposes, only the TM binary counter is shown as an example).
Figure 2
Test for model internal consistency and optimality. The number of rules used in the transition table for the first and shortest Turing machine producing a string following the enumeration is in agreement with the estimation arrived at by CTM after application of the Coding theorem under the assumptions of optimality. Adapted from [53].
Figure 3
Agreement in shape and ranking of empirical distributions produced by three completely different models of computation: Turing machines (TM), cellular automata (CA), and post tag systems (TS), all three universal Turing models of computation for the same set of strings of length k=5 and k=6 for purposes of illustration only (comparison was made across all string lengths up to around 20, which already included a large set of 220 strings).
Figure 4
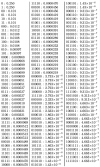
This is the first ever empirical probability distribution produced by all the 15,059,072 Turing machines with three states and two symbols as reported in [29]. CTM has produced several comprehensive large tables for all binary (and also non-binary [60]) Turing machines with up to four and five states (and currently for six states) and is currently also computing for six states on one of the largest super computers available. The distributions (this and the much larger ones that followed) have shed light on many matters, from long standing challenges (the short string regime left uncovered by statistical compression), to the impact of the change of choice of computational power on empirical output distributions, to applications tested in the field that require high sensitivity (such as perturbation analysis [39,40]).
Figure 5
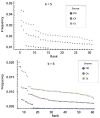
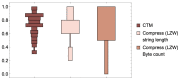
(A) Unlike compression, which behaves just like the Shannon entropy, CTM approximates the long-tail shape of the universal distribution, better conforming with the theory under strong assumptions of optimality. We call these causal gaps (A,B) because they are precisely the cases in which strings can be explained by a computer program of length far removed from the greatest program length of the most algorithmically random strings according to our (universal) computational model. (C) Divergence of CTM from entropy (and therefore LZW). Adapted from [38].
Figure 6
Density histograms showing how poorly lossless compression performs on short strings (just 12 bits in length), collapsing all values into two to four clusters, while CTM produces a finer-grained classification of 36 groups of strings. CTM (and BDM) can be calculated using the Online Algorithmic Complexity Calculator (
https://complexitycalculator.com/
).
Figure 7
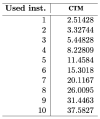
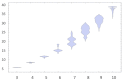
Each “drop-like” distribution represents the set of strings that are minimally produced with the same number of instructions (Y axis) for all machines with up to four states for which there can be up to 2(n+1)=10 transition rules. The more instructions needed to produce the strings, the more complex they are shown to be according to CTM (Y axis), after applying a Coding theorem-like equation to the empirical probability values for each string. The results conform with the theoretical expectation: the greater CTM, the greater the number of instructions used by the shortest Turing machine according to the enumeration, and vice versa. Adapted from [53].
Similar articles
- A Decomposition Method for Global Evaluation of Shannon Entropy and Local Estimations of Algorithmic Complexity.
Zenil H, Hernández-Orozco S, Kiani NA, Soler-Toscano F, Rueda-Toicen A, Tegnér J. Zenil H, et al. Entropy (Basel). 2018 Aug 15;20(8):605. doi: 10.3390/e20080605. Entropy (Basel). 2018. PMID: 33265694 Free PMC article. - Symmetry and Correspondence of Algorithmic Complexity over Geometric, Spatial and Topological Representations.
Zenil H, Kiani NA, Tegnér J. Zenil H, et al. Entropy (Basel). 2018 Jul 18;20(7):534. doi: 10.3390/e20070534. Entropy (Basel). 2018. PMID: 33265623 Free PMC article. - A Review of Graph and Network Complexity from an Algorithmic Information Perspective.
Zenil H, Kiani NA, Tegnér J. Zenil H, et al. Entropy (Basel). 2018 Jul 25;20(8):551. doi: 10.3390/e20080551. Entropy (Basel). 2018. PMID: 33265640 Free PMC article. Review. - LSD-induced increase of Ising temperature and algorithmic complexity of brain dynamics.
Ruffini G, Damiani G, Lozano-Soldevilla D, Deco N, Rosas FE, Kiani NA, Ponce-Alvarez A, Kringelbach ML, Carhart-Harris R, Deco G. Ruffini G, et al. PLoS Comput Biol. 2023 Feb 3;19(2):e1010811. doi: 10.1371/journal.pcbi.1010811. eCollection 2023 Feb. PLoS Comput Biol. 2023. PMID: 36735751 Free PMC article. - Methods of information theory and algorithmic complexity for network biology.
Zenil H, Kiani NA, Tegnér J. Zenil H, et al. Semin Cell Dev Biol. 2016 Mar;51:32-43. doi: 10.1016/j.semcdb.2016.01.011. Epub 2016 Jan 21. Semin Cell Dev Biol. 2016. PMID: 26802516 Review.
Cited by
- Emergence and algorithmic information dynamics of systems and observers.
Abrahão FS, Zenil H. Abrahão FS, et al. Philos Trans A Math Phys Eng Sci. 2022 Jul 11;380(2227):20200429. doi: 10.1098/rsta.2020.0429. Epub 2022 May 23. Philos Trans A Math Phys Eng Sci. 2022. PMID: 35599568 Free PMC article. - Kolmogorov compression complexity may differentiate different schools of Orthodox iconography.
Peptenatu D, Andronache I, Ahammer H, Taylor R, Liritzis I, Radulovic M, Ciobanu B, Burcea M, Perc M, Pham TD, Tomić BM, Cîrstea CI, Lemeni AN, Gruia AK, Grecu A, Marin M, Jelinek HF. Peptenatu D, et al. Sci Rep. 2022 Jun 24;12(1):10743. doi: 10.1038/s41598-022-12826-w. Sci Rep. 2022. PMID: 35750777 Free PMC article. - Effects of External Stimulation on Psychedelic State Neurodynamics.
Mediano PAM, Rosas FE, Timmermann C, Roseman L, Nutt DJ, Feilding A, Kaelen M, Kringelbach ML, Barrett AB, Seth AK, Muthukumaraswamy S, Bor D, Carhart-Harris RL. Mediano PAM, et al. ACS Chem Neurosci. 2024 Feb 7;15(3):462-471. doi: 10.1021/acschemneuro.3c00289. Epub 2024 Jan 12. ACS Chem Neurosci. 2024. PMID: 38214686 Free PMC article. - Approximations of algorithmic and structural complexity validate cognitive-behavioral experimental results.
Zenil H, Marshall JAR, Tegnér J. Zenil H, et al. Front Comput Neurosci. 2023 Jan 24;16:956074. doi: 10.3389/fncom.2022.956074. eCollection 2022. Front Comput Neurosci. 2023. PMID: 36761393 Free PMC article. - Language of fungi derived from their electrical spiking activity.
Adamatzky A. Adamatzky A. R Soc Open Sci. 2022 Apr 6;9(4):211926. doi: 10.1098/rsos.211926. eCollection 2022 Apr. R Soc Open Sci. 2022. PMID: 35425630 Free PMC article.
References
- Franklin J.N.Y., Porter C.P. Key developments in algorithmic randomness. arXiv. 20042004.02851
- Bienvenu L., Shafer G., Shen A. On the history of martingales in the study of randomness. Electron. J. Hist. Probab. Stat. 2009;5:1.
- Kolmogorov A.N. Three approaches to the quantitative definition of information. Probl. Inf. Transm. 1965;1:1–7. doi: 10.1080/00207166808803030. - DOI
- Martin-Löf P. The definition of random sequences. Inf. Control. 1966;9:602–619. doi: 10.1016/S0019-9958(66)80018-9. - DOI
- Davis M. The Universal Computer, The Road from Leibniz to Turing. W. Norton & Company; New York, NY, USA: 2000.
Publication types
LinkOut - more resources
Full Text Sources