How to integrate third-party tools into GitHub Advanced Security code scanning (original) (raw)

Nicholas Liffen // Director, GitHub Advanced Security // GitHub
GitHub understands every workflow is unique. To support you, we offer an extensible platform with a broad ecosystem of over 17,000 app integrations and pre-built GitHub Actions templates across the software development lifecycle. This includes over 70 actions for open source and commercial security application security tools across categories like dynamic analysis, compliance, and container scanning that you can use to extend your testing beyond GitHub Advanced Security native solutions. Through these integrations, you are notified immediately in your workflow when there’s a security issue, and are provided insights for remediation in the same format that GitHub results are delivered, enabling you to avoid productivity-killing context-switching.
In this guide, we'll walk you through setting up an example integration, and KPMG will share some insights again.
We use many different static analysis tools at KPMG, including Checkov for cloud infrastructure configurations, Trivy for containers, and ESLint for code quality. It would be easy to add several tools to your pipeline but then never check the results. But by pulling everything into one place, code scanning makes it easier to benefit from all the different tools we use. It helps ensure that nothing is slipping through the cracks. It’s a pretty underrated capability of GHAS.

Phil Wright-Christie // Lead DevOps Engineer // KPMG
Let’s look at how you can use GitHub Actions to automatically run third-party application security tools, upload the results, and view them with code scanning.
In this guide, you will learn:
- Why third-party tools are a valuable addition to GitHub code scanning
- How to integrate third-party tools into code scanning with GitHub Actions
- How to view results from third-party code scanning tools in code scanning
1.Set up container scanning.
Let’s start with Trivy, a comprehensive security capability which enables organizations to scan containers. All of the logic within this section can be applied to other types of application security and quality tools.
Drop the following file into the .github/workflowsdirectory. You can name this file whatever you like, but we recommend something appropriate like trivy.yml
name: "trivy"
on:
workflow_dispatch:
push:
pull_request:
jobs:
trivy:
runs-on: ubuntu-latest
steps:
- uses: actions/checkout@v3
- name: Set up JDK 17
uses: actions/setup-java@v3
with:
distribution: 'temurin'
java-version: 17
architecture: x64
- name: Cache Maven packages
uses: actions/cache@v3.3.1
with:
path: ~/.m2
key: <span class="katex"><span class="katex-mathml"><math xmlns="http://www.w3.org/1998/Math/MathML"><semantics><mrow><mrow><mi>r</mi><mi>u</mi><mi>n</mi><mi>n</mi><mi>e</mi><mi>r</mi><mi mathvariant="normal">.</mi><mi>o</mi><mi>s</mi></mrow><mo>−</mo><mi>m</mi><mn>2</mn><mo>−</mo></mrow><annotation encoding="application/x-tex">{{ runner.os }}-m2-</annotation></semantics></math></span><span class="katex-html" aria-hidden="true"><span class="base"><span class="strut" style="height:0.6667em;vertical-align:-0.0833em;"></span><span class="mord"><span class="mord"><span class="mord mathnormal" style="margin-right:0.02778em;">r</span><span class="mord mathnormal">u</span><span class="mord mathnormal">nn</span><span class="mord mathnormal" style="margin-right:0.02778em;">er</span><span class="mord">.</span><span class="mord mathnormal">os</span></span></span><span class="mspace" style="margin-right:0.2222em;"></span><span class="mbin">−</span><span class="mspace" style="margin-right:0.2222em;"></span></span><span class="base"><span class="strut" style="height:0.7278em;vertical-align:-0.0833em;"></span><span class="mord mathnormal">m</span><span class="mord">2</span><span class="mord">−</span></span></span></span>{{ hashFiles('**/pom.xml') }}
restore-keys: ${{ runner.os }}-m2-
- name: Build with Maven
run: mvn --no-transfer-progress verify
- name: "Set up QEMU"
if: runner.os == 'Linux'
uses: docker/setup-qemu-action@v2.2.0
- name: "Set up Docker Buildx"
if: runner.os == 'Linux'
uses: docker/setup-buildx-action@v2
- name: "Verify Docker WebGoat build"
if: runner.os == 'Linux'
uses: docker/build-push-action@v4.1.1
with:
tags: localbuild/testimage:latest
push: false
load: true
context: ./
file: ./Dockerfile
build-args: |
webgoat_version=${{ env.WEBGOAT_MAVEN_VERSION }}
- name: Run Trivy vulnerability scanner
uses: aquasecurity/trivy-action@master
with:
image-ref: 'localbuild/testimage:latest'
format: 'sarif'
output: 'trivy-results.sarif'
timeout: 20m0s
- name: Upload Trivy scan results to GitHub Security tab
uses: github/codeql-action/upload-sarif@v2
if: always()
with:
sarif_file: 'trivy-results.sarif'What this workflow does is:
- Builds the Maven Project with a Maven install
- Sets up Docker and runs the Docker build locally in the action workflow
- Runs the Trivy container scan
- Uploads the results to GitHub code scanning.
Once you’ve committed the above file into the .github/workflowsdirectory, select the Actions tab. The Trivy job should be running.
2**. View the SARIF results.**
Select the Security tab on your Web Goat repository.
Select Code scanning from the sidebar.
Click the tool filter, and pick Trivy.
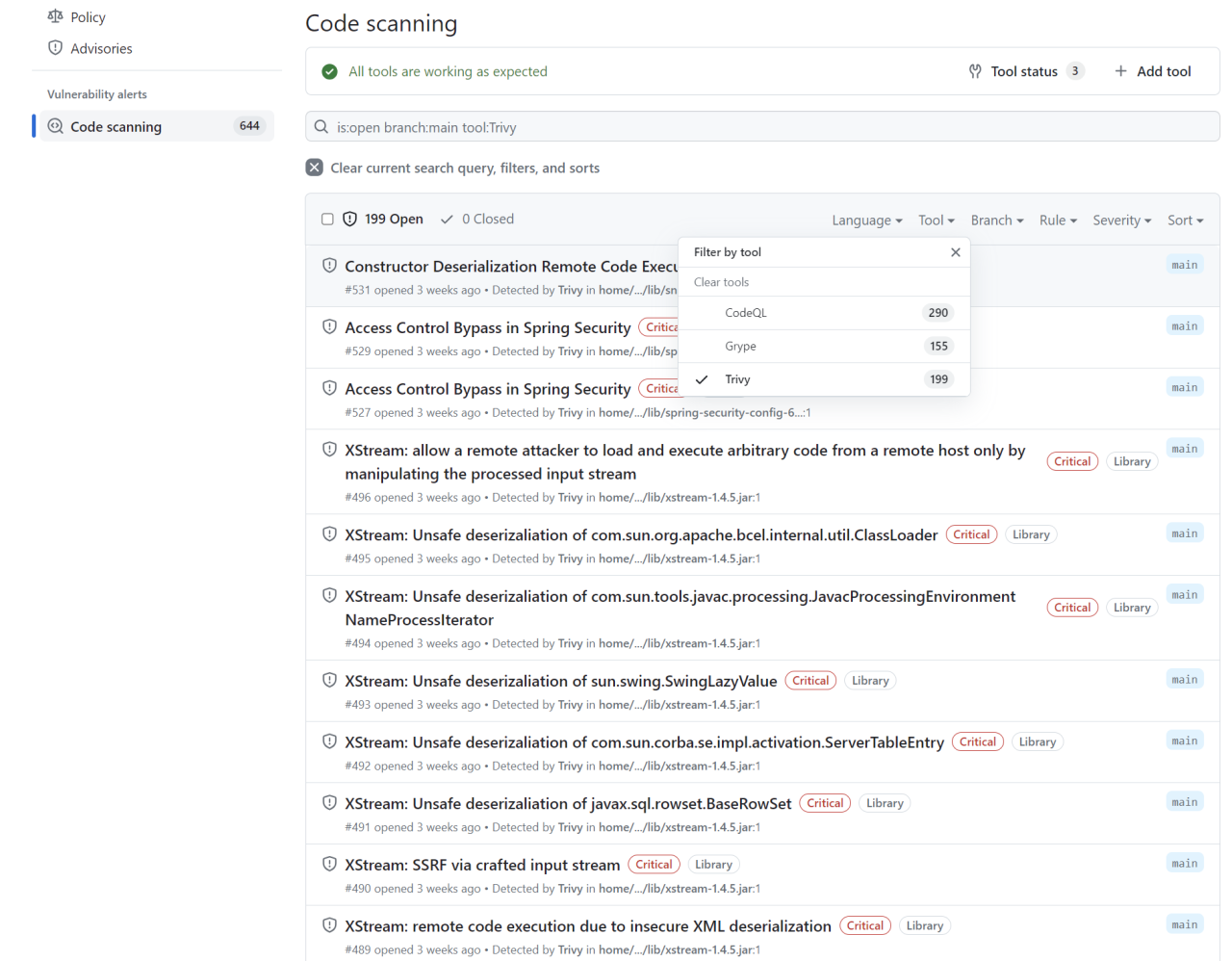
You should see some Trivy results.
Next up: Customizing the scope of secret scanning
Trivy is but one of many application security tools that you can use with code scanning. Be sure to check out GitHub Marketplace to find actions to help you automatically upload SARIF files from all the tools you use, and check out our automation learning pathway to learn more about GitHub Actions.
But first, let’s move on to secret scanning and how we can adjust the scope of our scans.