Identity and access management strategy: Time to modernize? (original) (raw)

igor - Fotolia
More likely than not, your company's identity and access management strategy needs an update. Learn how to decide if that's the case and, if so, what you should do now.
IT is constantly evolving, but the speed of change in how organizations of all sizes operate and interact has never been more frenetic. Now is the time to access and modernize your identity and access management strategy. The number of diverse and geographically spread users and devices connecting to enterprise networks via disparate applications and APIs grows daily, and the proliferation of device types is set to explode as the internet of things gains traction.
Security teams are on the back foot, struggling to keep control over who and what can access network resources at the very moment that identities are a primary target for hackers who -- armed with a valid identity and credentials -- can easily bypass other security controls. This makes identities a critical digital asset and puts identity security at the heart of a layered defense strategy. Many organizations have tried to use existing identity and access management (IAM) systems to deal with these seismic changes. But this has led to identity sprawl and debilitating security controls, creating a chaotic environment of unmanaged identities that is difficult to secure. Many identity and access management strategies have become outdated, so companies need to adapt and develop longer-term solutions.
The basic role of IAM is to associate all activities within an environment with a specific user or device and report on those activities. However, for an organization to stay competitive, identity and access governance is no longer enough; an IAM must handle identity federation and single sign-on (SSO) with easy administration and provisioning of users and devices on a massive scale. Yet many identity and access management strategies are still centered around in-house systems that fall short when it comes to mobile apps and customer-facing services, whose users demand quick and easy access wherever they are with whatever device they have. Even those security teams that do recognize identity as a new security perimeter are struggling to balance user demands against security requirements.
Identities are a critical digital asset, putting identity security at the heart of a layered defense strategy.
Bolting on additional identity and access management products to existing on-premises tools is rarely efficient or secure. As devices, applications and networks all support different protocols, this approach results in a disparate collection of homegrown identity management solutions with no centralized control that comprises the entire layer of identity controls. A major weakness is that it requires manual and time-consuming provisioning and deprovisioning of access as changes only propagate to some IT resources, leaving errors and omissions that can result in frustrated users, lost productivity and unprotected data.
Identity control layer essentials
The key to digital transformation success is providing joined-up services to employees, partners and customers quickly and easily. This puts SSO -- where the identity of an entity in one domain can be used for authentication of the same entity in another domain -- plus centralized provisioning and deprovisioning, high on the list of requirements for a modern identity and access management strategy. It also must be built on open standards, offer multifactor and context-aware authentication, be self-service and be able to scale, potentially to millions of users and devices.
Enterprises need to manage a diverse set of IT resources, which when it comes to identity management, use a diverse set of authentication protocols. Aim to limit the number of components needed to handle each different device and protocol type. This reduces the number of different tools and specialists required, as well as the chances of gaps being created where controls from different vendors don't sufficiently overlap.
Many IAM-related standards and protocols have been proposed over the years. Desktop applications often use Lightweight Directory Access Protocol (LDAP), whereas web-based applications tend to use Security Assertion Markup Language (SAML) or Open Authentication (OAuth), and Windows applications generally utilize Kerberos. Other standards include Central Authentication Service, OZ Protocol, CoSign Protocol, WS-Fed, JSON Web Token and OpenID Connect (OIDC). Although there is a broad range of options for implementing SSO, developers with the knowledge to code a secure and seamless integration between an application and identity provider aren't so plentiful. SAML, OAuth and OIDC are gaining traction with developers -- a report by Ping Identity found 49% of companies surveyed use OIDC -- but mobile and internet of things (IoT) requirements are harder to implement due to resource and communication limitations and a lack of authoritative guidelines on how to securely authenticate to specific identity provider platforms.
What IoT means for an identity and access management strategy
SSO is an essential feature for humans because it reduces many of the shortcomings of passwords. IoT devices don’t necessarily require the convenience of SSO, but a device's relationships are very important. Devices that must be identified in multiple domains need to have their identities and relationships managed across them, so an IAM that can only support one domain is not suitable for the complete identity management of IoT devices. The use of technologies like generic bootstrapping architecture and identity management systems built to handle IoT will be needed to reduce the complexity of maintaining the identities and relationships throughout a device's lifetime. The Cloud Security Alliance's guidance in its "Identity and Access Management for the Internet of Things" report even goes as far as to say that companies should "evaluate a move to identity relationship management in place of traditional IAM."
For the foreseeable future, CISOs will need to include securing multiprotocol environments in their identity and access management strategy, so the best approach will be to determine which protocols have to be supported and employ a single identity management solution that supports them without the need for extensive modifications or add-ons. This will ensure security and consistency, which in turn improves user productivity and generates cost savings.
However, building this class of IAM infrastructure is beyond the capability of most organizations and requires a huge investment in hardware and people, which in most cases will be a non-core activity. In many instances, the best option will be to outsource identity management to a provider that specializes in it. This is why many CISOs are turning to identity as a service (IDaaS) to upgrade their IAM capabilities. Both established IT vendors like Microsoft and Oracle, and newer players like Ping Identity, are promoting cloud-based services and platforms to deliver shared identities across multiple applications, while still providing a single aggregated view. Beware though that some providers who offer identity federation and SSO via the cloud do not provide a truly integrated and complete enterprise-grade IAM solution.
Accessing expertise: Cloud-based IAM
A big attraction of cloud-based IAM for many organizations is not just that it allows the rapid rollout of new capabilities, but that it solves the problem of finding and hiring security personnel with the skills to support on-premises IAM products. Tech Data, for example, wanted to deliver a frictionless experience for their customers and vendor partners. To do this, they needed to replace an antiquated system that no longer supported the complex needs of the business. They chose the Ping Identity Platform to deliver centralized, standards-based single sign-on and federated identity management.
Centralized lifecycle management tools for identities are a key feature to look for in any offering. Modifying access permissions is a time-consuming daily task: new users, those leaving or changing roles, and contractors and consultants coming and going. Their access rights and permissions all need to be easily updatable to maintain security and productivity. How well the end-user experience is delivered certainly affects security, as there is less incentive to circumvent frustrating login processes. Wayne Dale, application security engineer at FastMed Urgent Care, said, "We estimate that an average help desk call costs 15to15 to 15to30. By using Centrify Identity Service, we eliminated a couple of hundred calls a month, saving us thousands of dollars every year. We've definitely seen a return on investment."
A disparate collection of homegrown identity management solutions with no centralized control results in frustrated users, lost productivity and unprotected data.
Being able to reuse existing investments in on-premises directory infrastructures will be an important consideration for those needing to continue supporting legacy applications. JumpCloud's Directory as a Service can virtually connect any IT resource to a single, master directory, authenticating them in their natural protocol regardless of whether they are on-premises or cloud-based. Mike Lemire, while information security officer at Yesware, chose JumpCloud's cloud identity management platform for Yesware's hybrid environment that has two office locations, remote employees, Windows and Mac machines, Amazon Web Services servers and over 200 software as a service (SaaS) applications. "By implementing JumpCloud, I was able to implement very important controls across all of our laptops and all of our workstations." It also made enrolling new users a lot easier: "We add a user to JumpCloud, and they're automatically provisioned to Google, to their own machine and to other SaaS platforms."
With over 18,000 employees, Broadcom Limited decided on Okta's cloud-based service for a simple and efficient way to onboard new employees so that they can be productive starting on day one. According to an IT manager at Broadcom Limited, Neeraj Malhotra, Okta's service has recognized 30% faster time-to-productivity for new users from merger and acquisition activity, as well as 50% less time integrating newly acquired directories.
Microsoft Azure and Google Cloud Platform are currently the leading platforms on which IT leaders are running IAM technologies, and they work seamlessly with their own products. The attraction of IAM tools from many newer players though is that there is no vendor lock-in regarding which apps or devices can be used. This means IT departments can be more flexible when dealing with new requests from managers and users.
Some IAM products totally embrace the concept of a software-defined perimeter like Google BeyondCorps, which implements access policies based on information about a device, its state and its associated user, while Vidder PrecisionAccess uses multifactor authentication, context-aware authorization and device trust assessment before giving access to authorized applications. Of course, time frames designated in the service-level agreement for things like response times and patch installation are essential whenever responsibility for an aspect of security is entrusted to a third-party. Another essential is a matrix of who is responsible for what, particularly when it comes to an attack or breach.
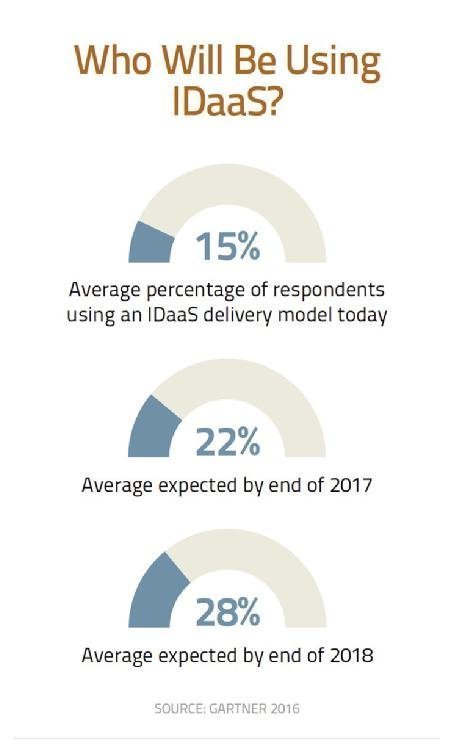
Whichever product is chosen, ongoing user training is vital. In a 2016 survey sponsored by KPMG, 46% of respondents said a lack of training or understanding of IAM policies and processes was expected to be the main cause of their next IAM-related breach.
Managing digital identities and access control for users, devices and applications in a world of cloud computing remains a real challenge. Any device, anywhere, with anytime access already has organizations rewriting the rule books. As IoT sweeps across the world, it will force enterprises to further adapt processes and technologies to securely manage the influx of users and devices and the rise in multiple interaction points with access to information.
The days of users conforming to how services are delivered are over; services must adapt to the new ways and devices used to get work done. To meet governance and compliance requirements, CISOs will need to overhaul their identify and access management strategies and their entire IAM infrastructure to reduce the risks associated with this level of remote access. Tackling such a challenge without outside help may well take two to three years and will need to include discovery, asset identification and provisioning to bring existing users and devices under the management of the IAM system. That timescale will put a business way behind its nimbler competitors. To successfully modernize an IAM infrastructure before it's too late, companies need to outsource the task to those who do it 24/7.
Next Steps
Learn what federated identity tools are all about
See why IAM can address unstructured content risks
Read what our expert has to say about biometrics and identity
 By: Aaron Tan
By: Aaron Tan  By: Andrew Froehlich
By: Andrew Froehlich  By: Nicholas Fearn
By: Nicholas Fearn  7 Reasons Identity and Access Management Is Important
7 Reasons Identity and Access Management Is Important  By: Linda Rosencrance
By: Linda Rosencrance