Hunting the Hunters: How We Identified Navalny's FSB Stalkers - bellingcat (original) (raw)
Today, alongside investigative partners CNN, Der Spiegel, and The Insider, we identified a long-running FSB operation to trail Russian opposition figure Alexey Navalny, including a number of chemical weapons experts involved in the research and development of Novichok. How did we find all of this information, and how did we verify the information? We’ll detail our investigative methodologies here, with some discussion on Russian data markets, cross-referencing data to be sure of its veracity, and other topics.
Bellingcat has previously investigated the role of a chain of Russian government-run scientific institutes in providing research into and manufacturing of nerve agent for GRU’s overseas assassination program, including the March 2018 Novichok poisoning of Sergey and Yulia Skripal and the earlier poisoning of Bulgarian arms manufacturer Emilian Gebrev.
In the course of a Belingcat investigation into Russia’s renewed chemical weapons project, we analyzed call metadata for the telephone numbers used by two senior executives of SC Signal, an entity that we found to be directly involved in the development of new variants and application methods for nerve agents. We had observed that in the months preceding Alexey Navalny’s poisoning, both of these executives – Arur Zhirov and Victor Taranchenko – had communicated with Stanislav Makshakov, and less frequently with his FSB superiors Kirill Vasilyev and Vladimir Bogdanov.
At the start of Bellingcat’s investigation into the Navalny poisoning we investigated whether a similar surge appeared between SC Signal executives and the GRU-linked institute just before the Navalny poisoning in Tomsk. We did not find such a pattern; with a single Signal-GRU (Sergey Chepur) phone call on 6 July 2020. However we did observe a more significant surge between SC Signal and FSB linked numbers. In particular, The first such surge appeared in the period 29 June 2020 to 7 July 2020, with а peak on 6 July 2020. On 6 July, SC Signal’s CEO Artur Zhirov had received calls from four different FSB employees linked to the Criminalistics Institute, including Col. Stanislav Makshakov and Gen. Vladimir Bogdanov. In addition Zhirov had received a call from a landline number belonging to FSB’s secure communications department.
With this information, we started our search, eventually finding a team of FSB officers and chemical weapon experts who had trailed Alexey Navalny since 2017.
Russia’s Data Market
Much of the information we used for our investigations could never be found in most Western countries, but in Russia, is readily available either for free or a fairly modest fee. Additionally, Russian email providers, such as Mail.ru and Rambler, and social networks, such as Vkontakte, are far less secure and privacy-focused than their Western equivalents, leading to frequent data leaks and robust search functions.
Due to porous data protection measures in Russia, it only takes some creative Googling (or Yandexing) and a few hundred euros worth of cryptocurrency to be fed through an automated payment platform, not much different than Amazon or Lexis Nexis, to acquire telephone records with geolocation data, passenger manifests, and residential data. For the records contained within multi-gigabyte database files that are not already floating around the internet via torrent networks, there is a thriving black market to buy and sell data. The humans who manually fetch this data are often low-level employees at banks, telephone companies, and police departments. Often, these data merchants providing data to resellers or direct to customers are caught and face criminal charges. For other batches of records, there are automated services either within websites or through bots on the Telegram messaging service that entirely circumvent the necessity of a human conduit to provide sensitive personal data.
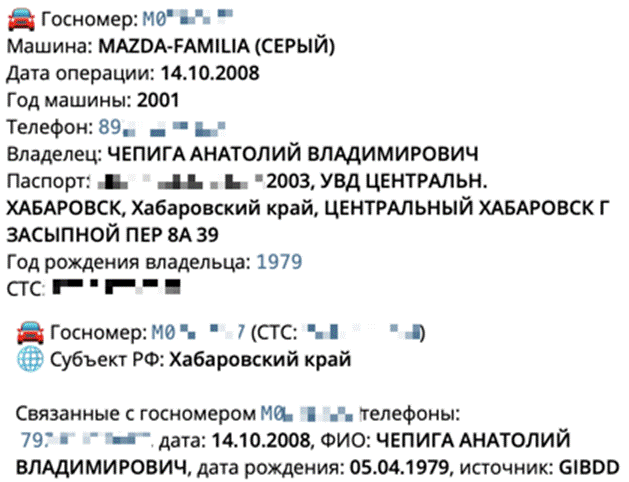
For example, to find a huge collection of personal information for Anatoliy Chepiga — one of the two GRU officers involved in the poisoning of Sergey Skripal and his daughter — we only need to use a Telegram bot and about 10 euros. Within 2-3 minutes of entering Chepiga’s full name and providing a credit card via Google Pay or a payment service like Yandex Money, a popular Telegram bot will provide us with Chepiga’s date of birth, passport number, court records, license plate number, VIN number, previous vehicle ownership history, traffic violations, and frequent parking locations in Moscow. A sample of the baseline information provided can be seen below, with key personal details censored.
Redacted screenshot of personal data for Skripal poisoner Anatoliy Chepiga. Some details provided include his car’s license plate number (госномер), telephone number(s) (телефон), passport number and year/place of issuance (паспорт), and date of birth (дата рождения).
For more information on the Russian data black market, see this investigation by Andrey Zakharov for the BBC’s Russian Service (abbreviated version in English) where the journalist tested out these data markets to see their accuracy and delivery methods. He was able to purchase his own passport file for about 2,000 rubles (about 22.50 EUR) from a data seller on an online forum. After talking to another anonymous data broker, who marketed themselves as a “detective agency”, Zakharov spent “less than 10,000 rubles” (about 110 EUR) purchased phone records for both himself and a family member. The data was accurate, and included the near-exact locations for himself and his family member over a recent timespan.
While there are obvious and terrifying privacy implications from this data market, it is clear how this environment of petty corruption and loose government enforcement can be turned against Russia’s security service officers. A few hundred euros could — and does — provide you with months of phone call data for an FSB or GRU officer, allowing investigators to trace the intelligence services’ operations, identify the colleagues of research targets, and follow the physical tracks of spies across Russia and abroad.
Our Discovery Process
Uncovering the identities of the FSB officers involved in the Navalny operation involved some legwork with the aforementioned Russian leaked data information system along with more traditional open source investigation. We will detail the workflow of how the initial leads were found, followed-up on, and expanded on to find new data points and build confidence in the veracity of our acquired data. It is important to note that for every source of data we find, we are sure to verify and corroborate it with other data sources. A person’s name, date of birth, license plate, passport number, and other data points can be cross-referenced with other sources to be sure that a single data source is not tainted. Additionally, most all of the leaked sources are preserved as they were when leaked — meaning that if someone is in the headlines for misdeeds in 2020, a leaked database from 2016 will be out of the hands of the Russian government and others for manipulation.
Bellingcat has acquired dozens of leaked databases over the past few years, giving us a large number of data points to cross-reference and verify any new data we acquire. If the birth date of an FSB officer in an explosive new dossier does not match that of a Moscow oblast vehicle registration database from 2013, then something is amiss — but we rarely run into such issues, and did not have any of these contradictions in this investigation.
A starting point was looking at passenger manifests of parallel flights to the ones that Navalny took. Our hypothesis was that it was unlikely that any potential operatives would travel on the exact same flight as Navalny, but would rather fly on an earlier one to the same destination, and return to Moscow soon after. Navalny’s itinerary — as would be clear to a government employee or data broker with access to booking records — was to take Aeroflot 1460 from Moscow to Novosibirsk on August 14, and later return to Moscow from Tomsk on August 20.
With this in mind, we looked at other flights to Novosibirsk on August 14, when Navalny arrived, or the day prior. We cross referenced these passengers with those who had tickets to travel from Tomsk to Moscow the on August 20 or 21, matching Navalny’s itinerary. These parameters led us to Aleksey Frolov, a Russian man born in 1980 who had a flight from Moscow to Novosibirsk on August 13 (Aeroflot 1460, the same as Navalny), and from Tomsk to Moscow on August 21. However, even though he purchased the Tomsk – Moscow ticket, he never boarded the flight — matching the circumstances of Navalny being rerouted to Omsk when suffering the effects of poison on board his return flight.
If that sounds like a long shot, bear in mind the specificity of Frolov’s travel itinerary — and the decreased number of passengers on internal flights due to the COVID-19 pandemic.
What was interesting about Frolov’s return flight to Moscow is that he was listed as a co-traveler with two other men, indicating that their tickets were purchased in a group operation (i.e. a single person bought all three tickets together). These two men were Vladimir Panyaev and Ivan Spiridonov.
Now, we had three names of potentially suspicious men — a man named Frolov with the exact same travel itinerary as Navalny except for arriving a day early and departing a day later, and two other men who were traveling with him back to Moscow. Frolov and Spiridonov were ghosts with all the markings of fake personas: no taxpayer number (INN), no history of vehicle ownership, and no registered residences, yet they were traveling all over Russia for years. Panyaev, however, was using his real name. When searching for Panyaev’s phone number on the GetContact app, which crowdsources contact book entries for a given number, we found that he was listed as “FSB Vladimir Alexandrovich Panyaev” in someone’s phone contact book.
Screenshot from GetContact listings, with the three names provided for Panyaev being: “Vladimir Panyaev”, “Panyaev Vladimir”, and “FSB Vladimir Alexandrovich Panyaev”
One person listing a man as “FSB” in their phone is not conclusive proof that they are indeed an operative with the FSB, but it’s as good of a lead as any to dig more into the trio who were planning on traveling together from Tomsk to Moscow: Panyaev, Frolov, and Spiridonov.
In examining Panyaev’s travel records, the information dam bursts: he had common trips with Frolov to Kaliningrad in July 2020 — matching Navalny’s itinerary. They also travelled together to Astrakhan in April 2017, where Navalny was scheduled to visit before a zelenka attack sent him to the hospital. Just before the Astrakhan trip in April 2017, they travelled together to Chelyabinsk, where Navalny visited at the same time.
Panyaev also was a co-traveler with a man named Aleksey Alexandrov on a flight from Omsk to Moscow in September 2017, yet again matching Navalny’s movements across Russia.
Clearly, this was either a cosmic coincidence, or Panyaev and his colleagues were trailing Navalny. While we could find nothing about Frolov outside of his travel records, Panyaev’s co-traveler to Omsk, Aleksey Alexandrov, seemed familiar. Aleksey Alexandrovich Alexandrov was born on 16 June 1981, while Aleksey Andreevich Frolov was born on 16 June 1980. Alexandrov’s wife’s maiden name, as we determined through examining social media, was Frolova. Searching for Aleksandrov’s residential history, we see that he was previously registered living at Michurinsky 25 — a residential building commonly used for those attending the FSB Academy, located down the road at Michurinsky 70.
After viewing Alexandrov’s phone records, the situation becomes clear: while Alexandrov did not book any travel from his home in Moscow before Navalny’s poisoning, Frolov did. Yet, metadata in his phone records revealed that on August 14, when Navalny had arrived in Novosibirsk, Alexandrov’s phone pinged a cell tower near the hotel where Navalny was staying. He later turns on his phone just after midnight on August 20, showing he was in Tomsk, near Navalny’s hotel just hours after the poisoning likely took place. Just like “Frolov”, Alexandrov trailed Navalny by traveling to Novosibirsk on August 14, and Tomsk on August 20. This same pattern can be seen in other locations where the travel records of “Frolov” and Alexandrov’s phone records matched up. Frolov is not a real person, but rather the cover identity of Alexandrov.
From here, we can build out the entire timeline of who talked to whom, where they traveled, and so on. Let’s walk through a handful of research vectors in establishing the FSB operation team.
Vehicle Address Registration
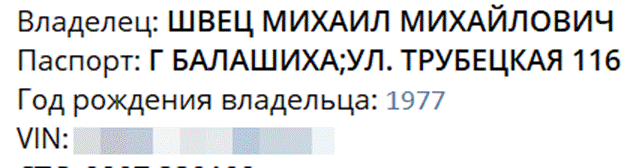
On August 15 and 16, a few days before Navalny’s poisoning, Alexandrov / Frolov communicated frequently with a Moscow-based number ending in -58. Searching this number on a popular Telegram bot reveals that it belongs to a man named Mikhail Shvets, born 1977. Shvets registered his vehicle to an address in 2019: Trubetskaya 116 in Balashikha.
Vehicle information from a popular Telegram bot linked to a number called by Alexandrov. The entry reads —
Owner: Shvets Mikhail Mikhailovich
Passport: City – Balashikha; Trubetskaya Street 116
Owner’s year of birth: 1977
VIN: [redacted]
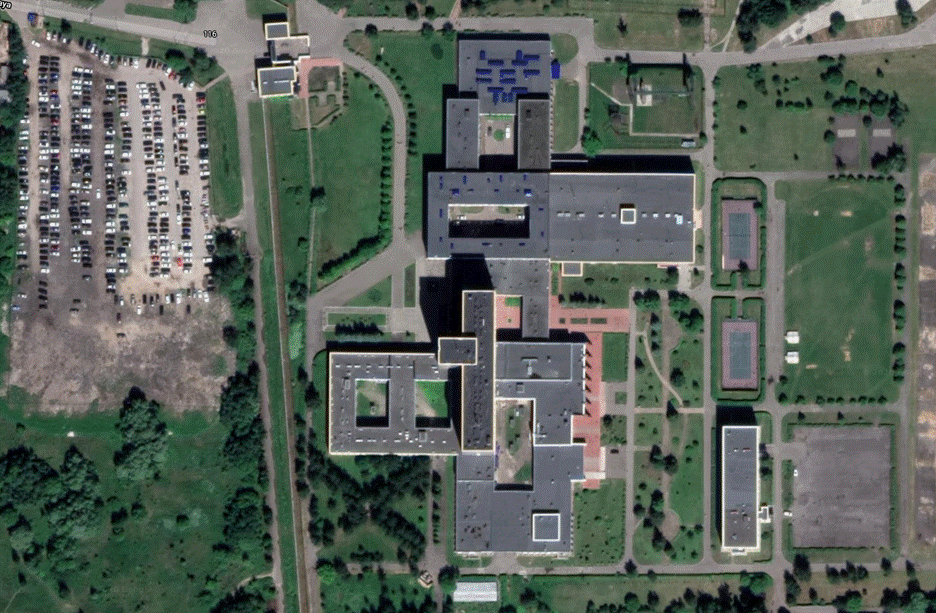
When looking at this address on Google Maps, it is clearly not a residential building, unless Shvets is a very wealthy oligarch with a gigantic housekeeping staff parked outside. This building on Trubetskaya 116 is not an address where anyone actually lives, but rather Shvets’s work address — the FSB Center for Special Operations.
FSB Center of Operations, located at Trubetskaya Street 116 in the Moscow suburb of Balashikha
Searching for this address on a leaked Moscow vehicle registration database reveals 191 people (along with Shvets) who have registered their vehicles to Trubetskaya 116. None of these registrations listed an apartment number, every one of these people was born between the years of 1970 and 1997 (age 23-50), and 161 of the 191 (84%) are male. This behavior mirrors that of other sloppy operations from the GRU, where its officers frequently list their work address in their vehicle registration.
Parking Leads
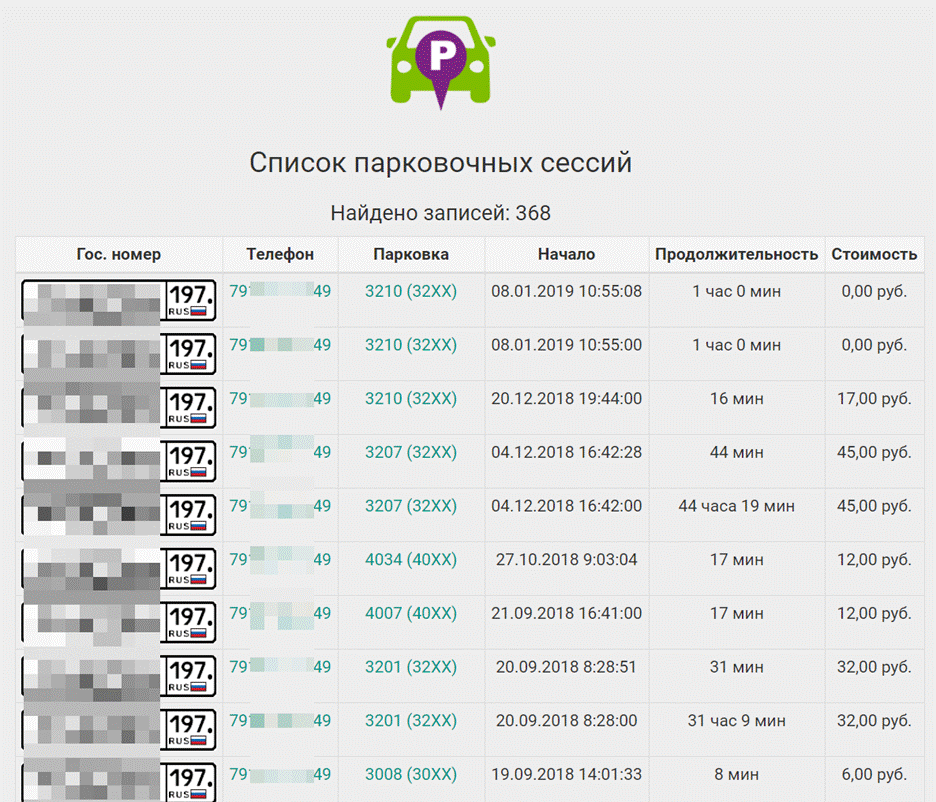
On August 25, a few days after Navalny was poisoned, Alexandrov / Frolov communicates with a Moscow-based number that ends in -49. When searching this number on a popular Telegram bot that trawls vehicle information, we see that someone with this phone number has paid for hundreds of parking sessions in Moscow for one vehicle.
Open database showing parking expenses in Moscow, linked to a number in Alexandrov’s phone logs
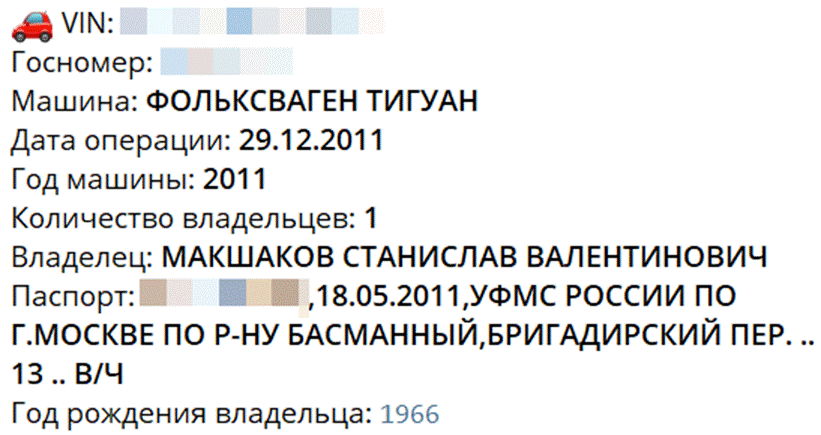
Both this car (by searching its license plate) and phone number are tied to a man named Stanislav Valentinovich Makshakov.
Information from a popular Telegram bot showing registration information tied to a car that was parked by a person using a cell phone number that communicated with Alexandrov.
VIN: [redacted]
License plate: [redacted]
Vehicle: Volkswagen Tiguan
Date of operation: 29.12.2011
Vehicle’s year: 2011
Number of owners: 1
Owner: Makshakov Stanislav Valentinovich
Passport: [redacted], 18.05.2011, UFMS Russia, Moscow (Basmanny district, Brigadirsky pereulok, 13, military unit)
Year of owner birth: 1966
Makshakov’s registered address is Brigadirsky pereulok 13 in Moscow — an official registered address for the Russian Ministry of Defense’s 27th Military Scientific Center. As we revealed in a previous investigation, this center was involved in the development and testing of chemical weapons, and a location visited by a key GRU officer during preparation of overseas assassination missions using chemical weapons.
Makshakov is listed as a patent holder regarding the use of a chemical for training soldiers during exposure to mustard gas — this patent was filed by military unit 61469 of the Russian Armed Forces, a scientific/medical unit based in the Saratov Oblast. Further investigation into Makshakov’s phone records will reveal that he supervised the operation, and is a scientist by training who worked in Shikhany in the Saratov Oblast– where Novichok was developed, and where military unit 61469 operates.
Frequent Flyers
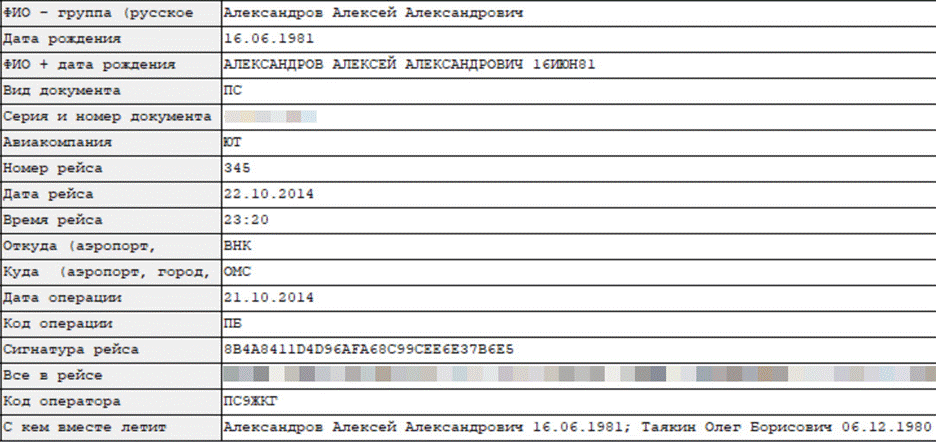
Further digging into the phone logs and travel records will flesh out the entire operation and reveal cadres of FSB operatives. Alexandrov, for example, flew with a man named Oleg Tayakin in October 2014.
Flight showing Alexandrov and Tayakin as co-travelers between Moscow (Vnukovo) and Omsk on 22 October 2014
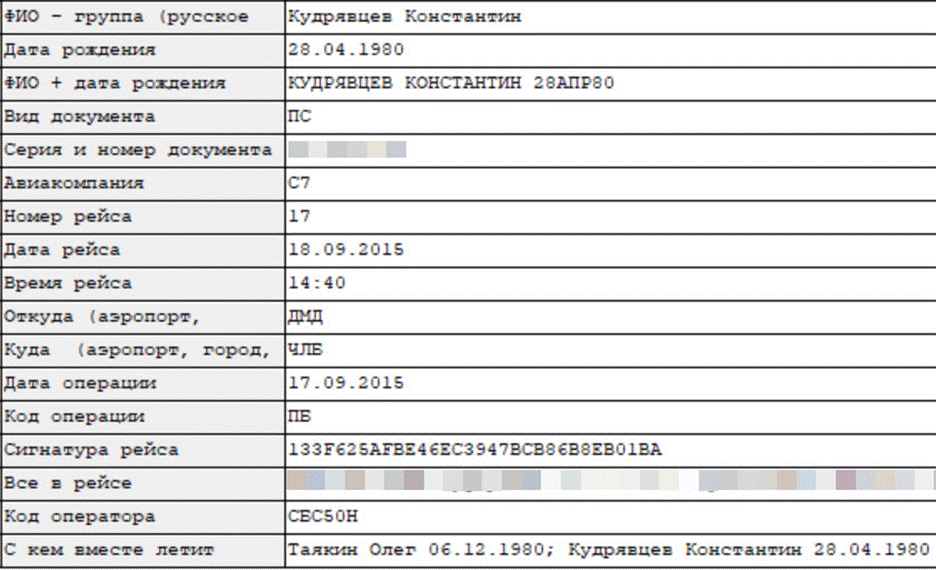
Searching for Tayakin’s passport number, we can see that he traveled with a man named Konstantin Kudryavtsev in 2015.
Flight showing Tayakin and Kudryavtsev as co-travelers, between Moscow (Domodedovo) and Chelyabinsk on 18 September 2015
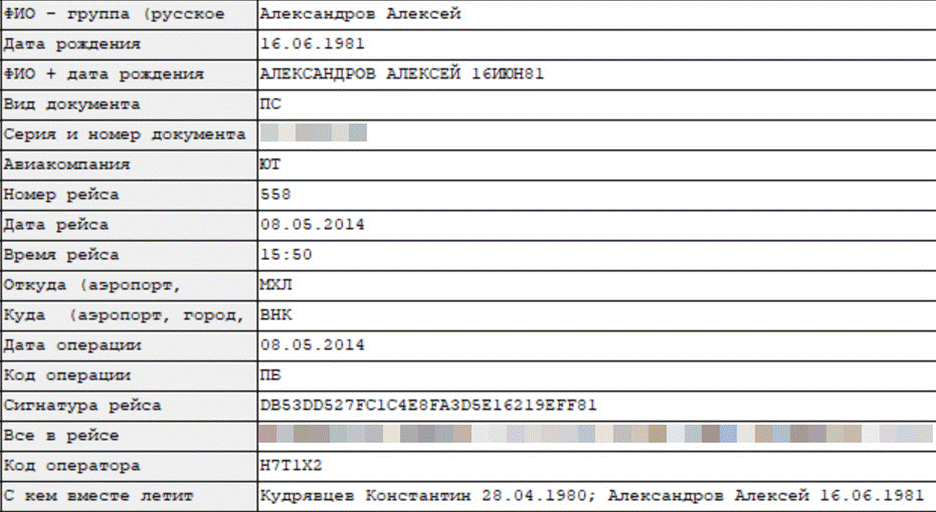
Completing the circle, we can see that Alexandrov traveled with the same Kudryavtsev in 2014.
Flight showing Alexandrov and Kudryavtsev as co-travelers, between Moscow (Vnukovo) and Makhachkala in Dagestan on 8 May 2014
All of these men are in each other’s phone contact logs, and also communicating and traveling with the aforementioned Makshakov, Panyaev, and Spiridonov (real name Ivan Osipov), among other operatives involved in the poisoning of Aleksey Navalny.
Predictable Algorithms
The algorithms often used by the FSB to create alter egos for their operatives is pretty easy to figure out: the same first name, the same date/month of birth (with the year shifted up or down by one), and the last name usually matching the maiden name of either the operative’s wife or girlfriend. For example:
- Aleksey Alexandrovich Alexandrov (born 16 June 1981) becomes Aleksey Andreevich Frolov (born 16 June 1980)
- Ivan Vladimirovich Osipov (born 21 August 1976) becomes Ivan Vasilyevich Spiridonov (born 21 August 1975)
- Konstantin Borisovich Kudryavtsev (born 28 April 1980) becomes Konstantin Yevgenievich Sokolov (born 28 April 1979).
Sometimes there are minor innovations, but still within the realm of educated guessing:
- Oleg Borisovich Tayakin (born 6 December 1980) was aged down exactly six months to become Oleg Vasilievich Tarasov (born 6 June 1980).
Conclusion
Tugging on one thread will unravel an entire tapestry of cross-referenced data, eventually revealing how Navalny’s poisoning was planned and carried out by a team of chemical weapon experts and FSB operatives. Much of this data is available due to the negligence of the Russian government — it’s hard to imagine an entire city’s vehicle registration database with passport numbers, addresses, license plate numbers, and other data to be leaked online annually for anyone to find in Germany or Canada — as well as the sloppiness of the security services themselves.
The FSB and GRU are as ambitious as they are dangerous in their operations, but the same cannot be said about their operational security practices. You do not need to look for dead drops in a park or trail people through alleyways to uncover the cover identities of spies, rather you just need a keen eye, patience, and the sense of knowing where to look for available leaked data sources.
Written by Aric Toler