Python theHarvester How to use it? (original) (raw)
Last Updated : 12 Jul, 2024
**theHarvester is another tool like sublist3r which is developed using Python. This tool can be used by penetration testers for gathering information of emails, sub-domains, hosts, employee names, open ports, and banners from different public sources like search engines, PGP key servers, and SHODAN computer database. This tool can be used in passive reconnaissance and by anyone who needs to know what an attacker can see about the organization.
How to install theHarvester
If you are using a Kali Linux machine then this tool is already installed in it, just type the command
theharvester
or
theHarvester
It will generate a help menu and list all available options which look like this:
root@kali:~# theharvester
*- | || |_ ___ /\ /__ _ _ ____ _____ __| | ___ _ __ *
- | _| ' \ / _ \ / /_/ / _` | '__\ \ / / _ / __| / _ \ '| *
- | |_| | | | _/ / __ / (| | | \ V / _/_ \ || __/ | *
- _|| ||___| / // _, || _/ _||/____|| *
*- TheHarvester Ver. 3.0.0 *
- Coded by Christian Martorella *
- Edge-Security Research *
- cmartorella@edge-security.com *
Usage: theharvester options
-d: Domain to search or company name
-b: data source: baidu, bing, bingapi, dogpile, google, googleCSE,
googleplus, google-profiles, linkedin, pgp, twitter, vhost,
virustotal, threatcrowd, crtsh, netcraft, yahoo, all
-s: start in result number X (default: 0)
-v: verify host name via dns resolution and search for virtual hosts
-f: save the results into an HTML and XML file (both)
-n: perform a DNS reverse query on all ranges discovered
-c: perform a DNS brute force for the domain name
-t: perform a DNS TLD expansion discovery
-e: use this DNS server
-p: port scan the detected hosts and check for Takeovers (80, 443, 22, 21, 8080)
-l: limit the number of results to work with(bing goes from 50 to 50 results,
google 100 to 100, and pgp doesn't use this option)
-h: use SHODAN database to query discovered hostsExamples:
theharvester -d microsoft.com -l 500 -b google -h myresults.html
theharvester -d microsoft.com -b pgp
theharvester -d microsoft -l 200 -b linkedin
theharvester -d apple.com -b googleCSE -l 500 -s 300
To install it in other Linux os you can use the command
sudo apt-get install theharvester
If this do not work you can clone the Git hub repository and use it using commands
git clone https://github.com/laramies/theHarvester.git
cd theHarvester
sudo python ./theHarvester.py
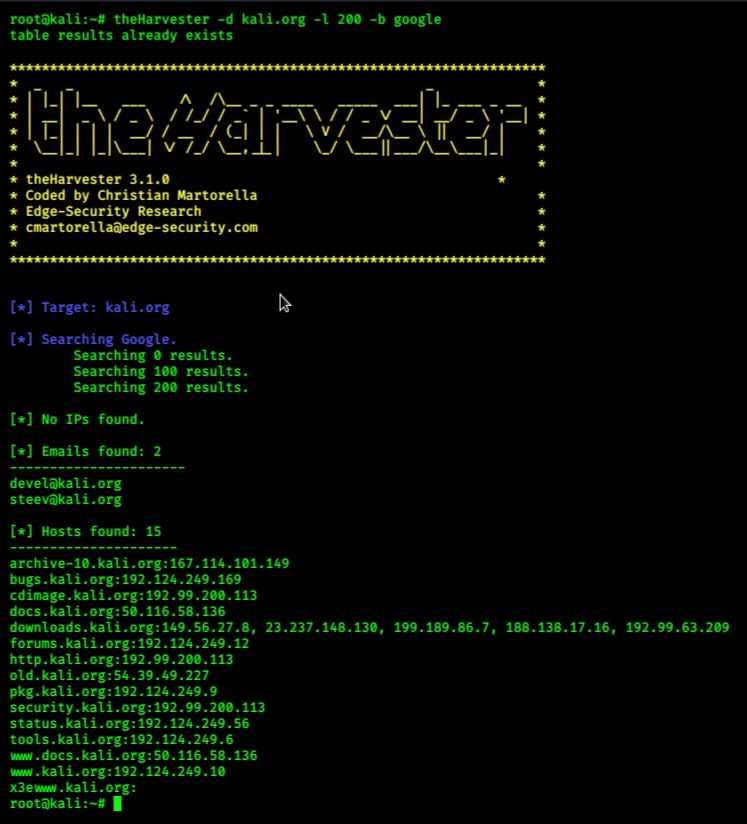
**Example
Search email addresses from domain kali.org with results of 200 and using **Bing as data source.
theharvester -d kali.org -l 200 -b bing
Enhance your coding skills with DSA Python, a comprehensive course focused on Data Structures and Algorithms using Python. Over 90 days, you'll explore essential algorithms, learn how to solve complex problems, and sharpen your Python programming skills. This course is perfect for anyone looking to level up their coding abilities and get ready for top tech interviews.
Join the Three 90 Challenge and commit to completing 90% of the course in 90 days to earn a 90% refund. It’s the perfect way to stay focused, track your progress, and reap the rewards of your hard work. Take the challenge and become a DSA expert in Python today