communications – Techdirt (original) (raw)
Trump Using Pointless, Shitty Tariffs To Bully Countries Into Coddling Elon Musk’s Starlink
from the cronyism-on-steroids dept
By now most sentient people realize Trump’s tariffs are a mindlessly descructive gambit that’s going to decimate inventory, drive smaller companies out of business, and significantly drive up costs for American consumers. There’s bottomless evidence that the clumsy effort to bully the planet was concocted by imbeciles, and most countries have justifiably told the Trump administration to go fuck itself.
But amusingly (?), the Trump administration still seems to think it can leverage the threat of tariffs to try and force companies into using Elon Musk’s Starlink service, according to the Washington Post:
“A series of internal government messages obtained by The Post reveal how U.S. embassies and the State Department have pushed nations to clear hurdles for U.S. satellite companies, often mentioning Starlink by name. The documents do not show that the Trump team has explicitly demanded favors for Starlink in exchange for lower tariffs. But they do indicate that Secretary of State Marco Rubio has increasingly instructed officials to push for regulatory approvals for Musk’s satellite firm at a moment when the White House is calling for wide-ranging talks on trade.”
When asked by WAPO, the State Department just insisted they were being patriotic:
“Starlink is an American-made product that has been game-changing in helping remote areas around the world gain internet connectivity. Any patriotic American should want to see an American company’s success on the global stage, especially over compromised Chinese competitors.”
A growing number of countries are trying to move away from Starlink because of Musk’s unhinged support of racism and conspiratorial fascism, and the fact they’re not sure they can trust Musk to be objective or reliable when it comes to military and political communications.
Germany and Ukraine, for example, are starting to more heavily use France’s Eutelsat fledgling low Earth orbit (LEO) satellite services after Musk restricted Ukraine’s access to the service near Crimea because he personally opposed Ukraine’s military aims (defending itself from unprovoked invasion by a fascist).
The U.S. certainly has a long history of promoting U.S. corporate interests globally. But even this level of naked cronyism is an extreme outlier. Everywhere you look, the Trump administration is looking to coddle Trump’s rich benefactor, who donated $277 million to ensure Trump’s election victory.
They’ve duct-taped Starlink terminals to the White House roof, creating all sorts of new cybersecurity vulnerabilities by bypassing government security protocols. They’ve installed Starlink at the FAA, in a bid to oust Verizon out of a $2 billion agency telecom contract. They’re rewriting the infrastructure bill grant program to drive as much taxpayer money as possible to Elon Musk.
The head of the Trump FCC, Brendan Carr, has been going around acting like a used car salesmen, telling countries that refuse to sign up for Starlink service that they’re effectively aiding communism. Carr’s been falsely claiming that countries either have the choice of Starlink or compromised Chinese satellite service, ignoring a growing array of looming French, European, Canadian, and Jeff Bezos’ alternatives.
This is, of course, just transparently corrupt effort to reward the authoritarian administration’s top donor. And while Starlink certainly has its uses (disasters, war, or the middle of nowhere rural America–assuming you can afford it), it’s ill-suited for this sort of “use everywhere, for everything” approach.
The technology has been criticized for harming astronomy research and the ozone layer. Starlink customer service is largely nonexistent. It’s too expensive for the folks most in need of reliable broadband access. The nature of satellite physics, launch logistics, and capacity constraints means slowdowns and annoying restrictions are inevitable and will get worse, and making it scale to meet real-world demand is many years away. There are real questions about whether the network is even permanently sustainable.
It’s not an improved solution for White House broadband access (unless you’re trying to hide administration communications from transparency requirements). It’s not a good upgrade over Verizon fiber or 5G at the FAA. And it’s a very problematic a downgrade from the kind of high-capacity, future-proof fiber deployments the infrastructure bill was funding.
This is all before you get to the fact that Starlink is being run by an overt white supremacist openly embracing authoritarianism, who is actively decimating the country’s science, arts, consumer protection, and public safety infrastructure for his own amusement. Musk may be enjoying the fruits of his investments into Trump now, but the longer-term stain and stink on his brands may prove difficult to wash off as the full scope of the administration’s damage begins to penetrate thicker electorate skulls.
Filed Under: authoritarian, communications, corruption, low earth orbit, military, satellite, security, telecom
Companies: spacex, starlink
But His Gmail: National Security Advisor Waltz’s Private Email Hypocrisy
from the the-best-hypocrites-trump-can-find dept
Remember Mike Waltz? The National Security Advisor who’s spent the last few weeks demonstrating his profound inability to handle basic security? First, there was the illegal Signal chat where he accidentally added a journalist while discussing potential war crimes. Then we learned about his completely exposed Venmo contacts and leaked passwords. And now, in a twist that would be too on-the-nose for fiction, it turns out the same official who previously demanded DOJ action over private email use… has been conducting government business through Gmail.
Ah, but her emails.
All this seems less than great for the top “security” official in the administration.
Members of President Donald Trump’s National Security Council, including White House national security adviser Michael Waltz, have conducted government business over personal Gmail accounts, according to documents reviewed by The Washington Post and interviews with three U.S. officials.
The use of Gmail, a far less secure method of communication than the encrypted messaging app Signal, is the latest example of questionable data security practices by top national security officials already under fire for the mistaken inclusion of a journalist in a group chat about high-level planning for military operations in Yemen.
A senior Waltz aide used the commercial email service for highly technical conversations with colleagues at other government agencies involving sensitive military positions and powerful weapons systems relating to an ongoing conflict, according to emails reviewed by The Post. While the NSC official used his Gmail account, his interagency colleagues used government-issued accounts, headers from the email correspondence show.
This is, needless to say, pretty fucking bad. First, there’s the basic security incompetence: the National Security Advisor conducting sensitive government business through a commercial email service. Even if Gmail has robust security, it’s completely inappropriate for handling government communications — giving Google potential access to sensitive national security discussions that should never leave secured government systems.
But more concerning is what this reveals about Waltz’s (lack of) judgment. As National Security Advisor, he’s one of the highest-value targets for foreign intelligence services. Every personal account, every commercial service he uses represents another potential vulnerability for adversaries to exploit. And given his demonstrated pattern of security failures — from exposed Venmo contacts to leaked passwords — it’s clear he’s making their job easier.
The National Security Council’s response is a masterclass in missing the point (or, more accurately, misdirecting from the point). When pressed about “sensitive military matters” being discussed over Gmail, their spokesperson offered this gem:
Hughes said NSC staff have guidance about using “only secure platforms for classified information.”
This attempt at reassurance actually reveals the depth of the problem. The distinction isn’t just between classified and unclassified information — it’s about maintaining basic operational security for all sensitive government communications.
And as if to underscore how little they grasp this, we learned from a WSJ article that Waltz’s infamous Signal chat wasn’t a one-off mistake.
Two U.S. officials also said that Waltz has created and hosted multiple other sensitive national security conversations on Signal with cabinet members, including separate threads on how to broker peace between Russia and Ukraine as well as military operations
The scale of security failures here should be absolutely disqualifying for any administration official, let alone America’s top national security advisor. But what makes this situation particularly galling is Waltz’s own history of grandstanding about private email use. Here he is in a tweet that remains up from less than two years ago:

Yes, that’s the same Mike Waltz demanding DOJ action over private email use by a previous National Security Advisor. The hypocrisy would be merely annoying if the stakes weren’t so high. But this isn’t just about scoring political points — it’s about the fundamental security of our nation’s most sensitive communications.
By Waltz’s own standard, articulated in that still-visible tweet, the DOJ should be investigating his wanton use of private commercial messaging services. But more importantly, someone needs to ask: if this is how carelessly our National Security Advisor handles basic operational security, what other vulnerabilities has he created that we don’t yet know about?
Filed Under: but her emails, communications, gmail, mike waltz, national security
The Communication Vacuum Is Causing More Chaos As GameStop Tweets And Deletes Promo
from the literally-just-say-something! dept
The chaos for Xbox keeps on rolling, it seems. We were just talking about how years of muddled communication coming from Microsoft’s Xbox team over exclusives and game ports to other consoles is resulting in a ton of confusion and speculation among the gaming public. The responsibility for all of this lies squarely at the feet of Xbox chief Phil Spencer and his team, which have oscillated between talking out of both sides of their mouths on these exclusives, and just sitting back and not saying a single thing when the confusion shows its head. And what that also allows for is speculation and conspiracy theories when, seemingly, a 3rd party vendor simply makes an oopsie.
GameStop tweeted out a promotion the other day for a in-store demo day where the public could walk into a store and try out some games using “Game Pass,” Xbox’s game-streaming and subscription service. It’s currently called “Xbox Game Pass,” but GameStop’s tweet referred to it as “Microsoft Game Pass.” The result was immediate.
On February 7, the official GameStop Twitter/X/whatever account posted a promo image for an Xbox demo day. Seems fine enough. But when referring to Game Pass, the company used the term “Microsoft Game Pass.” This is odd. Normally, I don’t think anyone would really care. However, we ain’t in normal times right now.
A retweet from Wario64 pointing out the phrase “Microsoft Game Pass” went viral online and theories were quickly spun up, with many pointing to this as more evidence that Microsoft was planning to kill the Xbox brand or use it for hardware only. Others suggested that it was Microsoft rebranding the subscription service— which grants you access to hundreds of games for a monthly fee—so it could be used on Switch or PlayStation.
This was almost certainly a simple mistake. Microsoft has told reporters writing stories about this whole thing that it had nothing to do with the verbiage GameStop tweeted out. But this wild speculation is again the result of one thing: the vacuum the Xbox team has left in place to be filled by conspiracy theories and rumor.
And it only got worse when GameStop subsequently deleted the tweet entirely.
This, as you might expect, convinced some that it was a mistake. It also convinced some “passionate” gamers that it was actually evidence that GameStop let the cat out of the bag too early and the death of Xbox as a brand really is coming soon. The end is nigh and all that.
Anyway, the reality is that GameStop likey made a mistake. Or, someone realized that using the term “Microsoft Game Pass” right now would set off a firestorm of speculation that would lead to more coverage and online discussion of an event that, let’s be real here, would never have been covered by most places or talked about online by gamers if this whole thing hadn’t spiraled out of control.
Correct. The point isn’t that GameStop’s mistake is in and of itself a big deal. It isn’t. The point instead is that the Xbox team has completely failed to get out in front of all of this speculation, allowing everyone’s pet theories to take the place of what should have been clear and proactive communication coming out from Microsoft as to just what in the hell it has planned for the Xbox brand.
Seriously, Spencer and team: just freaking say something, for the love of god.
Filed Under: communications, game pass, phil spencer, video ames, xbox
Companies: gamestop, microsoft
Phil Spencer Internal Comms Leak, In Which He Only Addresses To Most Fringey Conspiracy Theory
from the facepalm dept
And here we go again. I have spent some time pointing out that the Xbox team has demonstrated an unfortunate inability to properly communicate both internally and externally about its various plans. Whether it comes to how it’s going to handle exclusives, game ports, or just the overall direction of the division’s plans, what comes out of the team at Microsoft is often a confusing, vague, jumbled mess that serves only to free everyone to speculate away as to what is actually going to happen. This came to a head recently, with rampant speculation primarily that Microsoft was going to port a number of high profile first-party games to other consoles, and a secondary and more fringe theory that Microsoft was going to get out of the console making business entirely.
Well, Xbox chief Phil Spencer has apparently held an internal open meeting with his team to answer, well, I guess only the fringiest of the speculation. We’ll start with what was actually addressed.
A recent story from reporter Shannon Liao alleges Spencer held an internal town hall meeting with Xbox employees on February 6, following the weekend reports of Xbox porting games to PS5. In that meeting, he reportedly said the company has no plans to stop making consoles and that Xboxes would continue to be a part of the company’s strategy alongside other devices.
This part is easy. I can’t believe any serious person actually ever thought that Microsoft was going to pivot away from its console business entirely. It is true that Sony is kicking Microsoft’s butt overall in the console market. Reports have Sony moving roughly three times the units compared with the Xbox. But selling 7.6 million Xbox units is nothing to sneeze at and it would be baffling to see the company simply walk out of the market entirely.
Which is what makes it so frustrating that Spencer only addressed that rumor and completely ignored the question about game ports.
Interestingly, Liao also reported on X/Twitter that Spencer did not confirm nor deny rumors that Starfield would go to other consoles, even though this meeting took place after those reports cropped up.
Later this week, we will likely find out if any of these rumors and reports of Xbox exclusives coming to other platforms are true. On February 5, the day before the reported town hall meeting, Spencer announced that a “business update event” about the future of Xbox was coming soon and that he would be sharing more details then. Until that time, the Xbox faithful will just have to hold on a little bit longer.
They’re not going to “hold on” at all, as we’ve already seen. They’re going to speculate, theorize, and otherwise fill the information void that Xbox has left in its wake. Sure, we may have answers this week, still. Maybe. Hell, with the Xbox team, you never know.
But leaving the public to generate its own theories will also virtually guarantee that whatever the news Spencer will finally release in his event will piss off or disappoint some percentage of the public that had settled on some theory that won’t come to be.
In other words, this is just not how you handle communicating to either your internal team, nor your customers.
Filed Under: communications, phil spencer, rumors, starfield, xbox
Companies: microsoft
California Court: Passwords Are Communications, Protected By The Stored Communications Act
from the only-so-far-you-can-take-a-subpoena dept
The Stored Communications Act — enacted in 1986 — is not only outdated, it’s also pretty weird. An amendment to the ECPA (Electronic Communications Privacy Act), the SCA added and subtracted privacy from communications.
It’s the subtractions that are bothersome. Law enforcement wasn’t too happy a lot of electronic communications were now subject to warrant requirements. They much preferred the abundant use/misuse of subpoenas to force third-parties into handing over stuff they didn’t have the probable cause to demand directly from criminal suspects.
Private parties — especially those engaged in civil litigation — also preferred to see fewer communications protected by the ECPA. So, this law — which declared every unopened email more than 180 days old free game — was welcomed by plenty of people who didn’t have the general public’s best interests in mind.
The government tends to make the most use of the ECPA and SCA’s privacy protection limitations, using the law and legal interpretations to access communications most people logically assumed the government would need warrants to obtain.
But the SCA also factors into civil litigation. In some cases, the arguments revolve around who exactly is protected by the law when it comes to unexpected intrusion by private parties. In this case — one highlighted by FourthAmendment.com (even as the site owner notes it’s not really a Fourth Amendment case) — it involves international litigation involving US service providers. The case directly deals with the Stored Communications Act and what it does or does not protect.
This lawsuit was brought by Path, an Arizona corporation, and its subsidiary, Tempest. Central to the litigation is Canadian citizen Curtis Gervais, who apparently was hired as an independent contractor by Tempest, which promoted him to the position of CEO in February 2022. A few months later, Gervais allegedly hacked into a competitor’s (Game Server Kings [“GSK”]) computers, leading to Tempest demoting (lol) Gervais to COO (Chief Operating Officer).
This demotion apparently didn’t sit well with Gervais, who allegedly began sharing confidential Tempest information with GSK, utilizing communications platform Discord to hand over this information to GSK employees.
So, it’s three American companies and one Canadian individual wrapped up in a dispute over ex parte demands to disclose information to the plaintiffs (Path/Tempest). Discord challenged the subpoenas, which asked for — among other things — any passwords used by Gervais to log into its services.
That’s where it gets interesting. Very few courts have considered what’s explicitly covered by the SCA and/or what can be obtained with subpoenas issued under this authority.
As is implied by both laws in play here (Electronic Communications Protection Act, Stored Communications Act), the protections (or lack thereof) apply to communications. Path argued that its subpoenas did not exceed the grasp of these laws, despite demanding Discord hand over Gervais’ passwords. According to the plaintiffs, passwords aren’t communications.
But that’s a very reductive view of passwords, something Discord pointed out in its challenge of the subpoenas:
Applicants argue passwords are not afforded protection under the SCA because passwords should not be considered “content.” Discord argues passwords are implicitly included within the SCA’s prohibitions because passwords implicate communications. In other words, Discord argues that passwords are “content “ under the SCA because they are “information concerning the substance, purport, or meaning” of a communication.
The court [PDF] says Discord is correct. But only after a lot of discussion because, as the court notes, this is an issue of “first impression.” It has never been asked to make this determination prior to this unique set of circumstances. But, despite the lack of precedent, the court still delivers a ruling that sets a baseline for future cases involving SCA subpoenas.
It begins by saying that even if the language of the SCA doesn’t specifically include passwords in its definition of “content,” it’s clear Congress meant to add protections to electronic communications with this amendment, rather than lower barriers for access.
The legislative history agrees with a broad interpretation of “content.” Congress explained that the purpose of enacting the SCA was to protect individuals on the shortcomings of the Fourth Amendment. Specifically, Congress enacted the SCA due to the “tremendous advances in telecommunications and computer technologies” with the “comparable technological advances in surveillance devices and techniques.” The SCA was further meant to help “Americans [who] have lost the ability to lock away a great deal of personal and business information.”
With this analysis of the scope of the term “content” under the SCA in mind, the Court now turns to determine if passwords are afforded protection under the SCA under that understanding of the definition of the term “content.” Passwords are undoubtedly a form of “information.” And passwords broadly “relate to” (or are “concerning”) the “substance, purport, or meaning of [a] communication” even if passwords are not themselves the content of a communication. Passwords further relate to a person’s intended message to another; while a password is not the content of the intended message, a password controls a user’s access to the content or services that require the user to prove their identity. As a matter of technological access to an electronic message, a password thus “relates to” the intended message because without a password, the author cannot access their account to draft and send the message (and the user cannot access their account to receive and read the message).
When a person uses a password to access their account to draft and send a message, that author inherently communicates to the recipient at least one piece of information that is essential to complete the communication process: namely, that the author has completed the process of authentication. The password is information or knowledge which is intended to convey a person’s claim of identity not just to the messaging system but also implicitly to the recipient. As such, within the context of electronic communication systems, passwords are a critical element because they convey an “essential part” of the communication with respect to access and security protocols.
The dispute at issue here demonstrates the inherency of communicating about passwords when using a messaging platform such as Discord: when the user of the “Archetype” sent messages demanding ransom for the stolen source code, those messages conveyed to the recipients that the author is or was an authentic or authorized user of the “Archetype” account who used and had access to the password for that account. That password for that account thus is information concerning that communication, even if the password is not itself written out in the content directly.
In addition to all of that, there’s the undeniable fact that if you’re able to obtain login info (including passwords) with a subpoena, it doesn’t matter if courts limit the reach of demands for communications. If you have the keys to the accounts, you have full access to any stored communications, whether or not this access has been explicitly approved by a court.
With this password in hand, a litigant (or their ediscovery consultants) would have unfettered access to all communications within the account holder’s electronic storage, without regard to relevance, privilege, or other appropriate bounds of permissible discovery. In other words, litigants could circumvent the very purpose of the SCA by simply requesting that a service provider disclose the password for a user account, ultimately vitiating the protections of the SCA.
No court would allow the government to claim this is acceptable under the SCA and/or the Constitution. And no court should allow it just because it’s litigation involving only private parties. This particular demand cannot be honored without violating the law. And the companies behind the subpoenas know this because they obviously have zero interest in obtaining nothing more than Gervais’ login info.
The only conceivable use for the passwords here is for Applicants to access the requested accounts (such as “Archetype”) and view the contents of all electronically stored communications in those requested accounts.
That’s clearly the litigants’ intent. And it doesn’t mesh with the legislative intent, which was to create a few new protections for then-newfangled electronic communications. This particular demand is rejected. The subpoenas are still alive, but they’re no longer intact. If the suing entities want access to the defendant’s communications, they’ll have to do it the old-fashioned way: by making discovery requests that remain on the right side of the law.
Filed Under: california, communications, curtis gervais, ecpa, passwords, sca, stored communications act
Companies: discord, path, tempest
Of Course Bank Execs Communicated Via Encrypted Messaging, But That’s Not The Fault Of Encryption
from the this-is-always-going-to-happen dept
I don’t think this is a surprise to anyone, but the SEC and the CFTC combined to issue fines on a bunch of Wall Street firms for execs communicating across encrypted messaging in a manner that wasn’t recorded and preserved as required. Being in a regulated industry means having to deal with all sorts of compliance requirements, that includes preservation of communications. But, of course, that freaks people out, so… they do what everyone does, and figure out ways to communicate outside of “official” channels such that it’s not recorded.
This could come in the form of… talking in person. Or over the phone. Or… by using third party messaging services that are widely available. And, if you’re going to do that, it’s no surprise that you’d use end-to-end encrypted services like Signal or WhatsApp.
The Securities and Exchange Commission today announced charges against 10 firms in their capacity as broker-dealers and one dually registered broker-dealer and investment adviser for widespread and longstanding failures by the firms and their employees to maintain and preserve electronic communications. The firms admitted the facts set forth in their respective SEC orders. They acknowledged that their conduct violated recordkeeping provisions of the federal securities laws, agreed to pay combined penalties of $289 million as outlined below, and have begun implementing improvements to their compliance policies and procedures to address these violations.
That’s from the SEC side. From the CFTC we get:
The Commodity Futures Trading Commission today issued orders simultaneously filing and settling charges against swap dealer and futures commission merchant (FCM) affiliates of four financial institutions for failing to maintain, preserve, or produce records that were required to be kept under CFTC recordkeeping requirements, and failing to diligently supervise matters related to their businesses as CFTC registrants.
The settling registrants admit the facts detailed in the orders, are ordered to cease and desist from further violations of recordkeeping and supervision requirements, and are ordered to engage in specified remedial undertakings.
There’s some overlap. Wells Fargo, BNP Paribas, and SG Americas/Société Générale) gets hit by both agencies.
The details are pretty much exactly what you’d expect:
The SEC’s investigation uncovered pervasive and longstanding “off-channel” communications at all 11 firms. As described in the SEC’s orders, the firms admitted that from at least 2019, their employees often communicated through various messaging platforms on their personal devices, including iMessage, WhatsApp, and Signal, about the business of their employers. The firms did not maintain or preserve the substantial majority of these off-channel communications, in violation of the federal securities laws. By failing to maintain and preserve required records, certain of the firms likely deprived the Commission of these off-channel communications in various SEC investigations. The failures involved employees at multiple levels of authority, including supervisors and senior executives.
I’ve seen some people using this as yet another opening to bash encryption, but encryption is not the problem here at all. First of all, encryption did not stop these banks from getting caught and fined. Second, as noted up top, people are always going to try to figure out ways to communicate that isn’t recorded. These messaging apps were convenient.
Indeed, if anything, these fines should (hopefully?) serve to get employees at these banks to be much more careful about how they communicate to avoid future fines. I still expect there to be plenty of attempts to get around the regulatory requirements to preserve communications, and it seems likely that bankers are going to get used to making phone calls or talking in person since that can’t be preserved in the same manner.
But, really, any time you have regulations requiring such archiving of so many communications, you just know that this kind of thing is likely to happen. There’s a reason why these industries are so heavily regulated… but there’s also a reason why the people in those industries really don’t want their communications preserved for future legal enquiries. There’s no perfect answer here, but these kinds of fines, (which, in total, added up to over half a billion dollars) at least suggest that there are financial penalties available for the banks that basically go “off-channel” as a standard way of communicating.
Filed Under: banks, cftc, communications, encryption, preservation, sec
Companies: bnp paribas, sg americas, wells fargo
Trust, Safety, And Communication
from the your-comms-strategy-is-your-trust-strategy dept
One thing that should be evident by now is that every online community eventually learns the need for some level of “trust & safety” or basic moderation to take place. And they quickly find that things are a lot more complex than they seem from the outside. Just try to moderate a medium sized Facebook Group if you want an example. Or play our Moderator Mayhem game.
It’s always interesting to see the points at which community organizers realize this and try to figure out how they’re going to handle this issue or that issue — and begin to realize what an impossible task it is. And while some people think that it’s now been long enough that any new community should have “the basics” figured out, it’s important to recognize that (1) there are always new problems, and (2) the “simple” problems are often a lot more complex than they seem. On top of that, there are thousands of things that any new community “should” have, and at some point the people building them need to weigh “releasing something” against “having every feature in place.” You can disagree with where the line is drawn, but everyone has to draw a line somewhere.
I was thinking about all this over the last week or so as there was some discussion when the (still invite-only beta) Bluesky ran into some issues regarding a username filter (specifically, the filter allowed users to sign up with slurs as their user names). This is, obviously, not good.
The debate on Bluesky morphed over the course of a few days from criticism regarding the pretty major omissions on the filter list, to the lack of communication from the company and its (normally communicative) employees. Basically the entire company went silent, followed eventually by some more bland “corporate” sounding responses that went against the “poasting” style the team had embraced earlier. Indeed, the sudden silence from the team stood out even more given their normal willingness to engage in all sorts of ways on just about everything else. Going from super talkative to silent at the moment of notable controversy is, perhaps, the opposite of a compelling communications strategy.
Still, it’s somewhat understandable when looked at in context. The teams have repeatedly talked about how much they need to accomplish in building both a protocol (which may change the nature of some of these issues) and their own platform as a reference app of that protocol. The service is still in beta for a reason. And when there are thousands of trust & safety things you need to set up in addition to building the platform and the service, raising money, finding a business model, and everything else, it can get a little overwhelming. And that’s especially true when the company had made earlier moves and statements suggesting that they took these issues seriously and were working on solutions. So, when things blow up because they missed some things, it can feel like an attack. The team believes their heart is in the right place, and they’re trying to balance the variety of things they need to do, and yet… they’re still getting yelled at.
But, alas, this is the general rule when you run any sort of online community: you will get yelled at, and at some point you need to decide what issues to deal with and what to focus on. Getting yelled at sucks. And often makes people clam up. Of course, the obvious (and very true!) counter to this is that having to deal with hate, abuse, and racism also sucks. And also makes people want to clam up. So if you’re taking a job to build a social network, you’re signing up for this specific kind of abuse, and you need to be ready for it in order to protect others from abuse.
Back in May, I had written a thing about social media Nazi bars, tradeoffs, and the impossibility of content moderation at scale, which I think remains quite relevant here. There are always tradeoffs, and unlike, say, Substack (which is much larger and much more well resourced), I’ve seen no indication that the Bluesky team is simply abdicating its responsibilities here, but rather prioritizing as best it can, meaning some things that everyone agrees are important won’t get put in place as quickly as some would hope.
For example, regarding the filter list, while it was an obvious failing in how the system was set up, any sort of brute filter list runs into problems over time. If you don’t want to deal with a “Scunthorpe” problem, you need a more sophisticated solution, and more sophisticated solutions require more time and thought, and we’re right back to the line-drawing exercise I mentioned above, where the long list of thousands of things you need to accomplish is at least one item longer (and more complex).
The real difference here seemed to be how much the communications problem exacerbated the more classic trust & safety failing.
And it made me start to think about how communications itself is a strategic trust & safety tool, though rarely considered as such. Some of the communications issue was, as many people noted, the failure of the company to come out and say they were sorry for the errors. And, yeah, it seems like this is a case where company leadership should have done so. But sorry only goes so far. Mark Zuckerberg has to keep going on apology tours, and it’s not clear that it’s really helpful.
Instead, I think the failure might be in the lack of clear communication on the larger roadmap from Bluesky. This applies to lots of other online communities as well, but I’m focused on Bluesky to make this point (although arguably, it applies even more to others). Many people (I think, falsely) focused on this one error regarding to the username filter list, insisting that it showed the company “didn’t care.” That struck me as unlikely, given earlier statements and actions by the Bluesky team, which seemed to indicate not just that they cared about this, but they cared deeply, to the point that they wanted more thoughtful, serious, and comprehensive approaches to dealing with it, rather than slapdash duct tape fixes.
But, unless you’re paying close attention, you might miss all of that. And there’s no clearly laid out roadmap that people might have pointed to to alleviate the concerns of others.
Things might have gone a bit differently if Bluesky had a page with a roadmap regarding its plans for federation, composable moderation, trust & safety tooling, trust & safety hiring, and the like. If such a roadmap existed, that showed exactly how the team was thinking about these things, and made it clear that the team was working towards them deliberately, including at least some public explanation of the tradeoffs of various approaches, it would be more difficult for users to fill in the void with “they just don’t care.”
On top of that, it would similarly give the team breathing room to keep working on that roadmap, rather than having to respond to every emergency (some emergencies will still require emergency reactions, but not every emergency will grind everything else to a halt). This isn’t the answer to everything, of course. Nothing is.
But having clear communications, especially regarding a project that is designed to be decentralized and is being designed for the public benefit, is a key element of building trust, which I guess would be somewhere around 50% of the point of building out trust & safety.
Creating such a roadmap is quite a process in and of itself. As far as I can tell, no one else has done it either. And I’ve already been talking about how the team likely already has too much on its plate. But it does strike me that spending a bit more time on this at this early stage might help prevent some of the problems going forward, both in allowing users to point out some areas where the roadmap may need to be adjusted, or in simply having a better understanding of not just where Bluesky is today, but where it’s heading in the future.
I honestly think this understanding of the communications element of trust & safety could help many other communities as well. Many of the complaints and problems come from a mismatch between expectations and how a company actually makes decisions. And one way to deal with that is to better align the expectations. I think the last decade might have gone differently if Twitter, Facebook and others had been more public and upfront with some of their internal trust & safety discussions as well, so this is hardly unique to Bluesky.
But, at the very least, I think it’s important to start considering the role of communications as a part of a trust & safety strategy.
Filed Under: communications, content moderation, roadmap, trust and safety
Companies: bluesky
Twitch Rolls Out New Tiered Revenue Splits, Pissing Creators Off Yet Again
from the why-is-this-so-hard? dept
Amazon-owned Twitch appears to be running something of an experiment to see just how much it can piss off its creative community before a mass exodus occurs. Reading back through our posts on the platform, you will be left with the understanding that there are two types of policy rollouts when it comes to Twitch. There are the policies the company rolls out and almost immediately has to rescind after everyone gets wildly angry. And then there are the polices the company rolls out that result in just as much anger, but where the platform ignores the anger and gives its creative community the middle finger.
We’ll have to saddle up and wait to just which version Twitch’s latest policy update is, which focuses on how some larger streamers can still earn the 70/30 revenue split despite everyone else getting moved into a 50/50 split tier.
Twitch’s mid-life platform crisis continues. After rolling out controversial new 50/50 revenue splits for top streamers last fall, the massively popular online gaming hangout is now announcing a new “Partner Plus Program” that will return certain channels to the previous 70/30 split, but with tons of caveats. It’s already not going over well.
“We want to help streamers keep doing what they love, so we can all keep loving what they do,” Twitch tweeted on June 15. “Today we’re announcing the Partner Plus program, a new program for streamers to build toward as they continue to grow their businesses,” began the blog post it linked to. From there it outlined how the new program will work when it launches in October, including a bunch of hyper-specific details.
And it’s those details that are pissing off some portion of the creative community. To qualify, streamers must have 350 recurring paid subscribers and there is something of a progressive revenue system at play, where the 70/30 split in the program only applies to the first $100k earned. After that, all money earned reverts back to the 50/50 split that pissed everyone off.
In other words, this is both aimed at placating the platform’s larger streamers while also still clawing a huge portion of the revenue back both among small and larger streamers. And for a majority of those streamers, purely from a revenue sharing standpoint, it’s difficult to see what remains attractive about streaming on Twitch versus other platforms, such as YouTube. Especially for non-established streamers looking to build themselves on the platform.
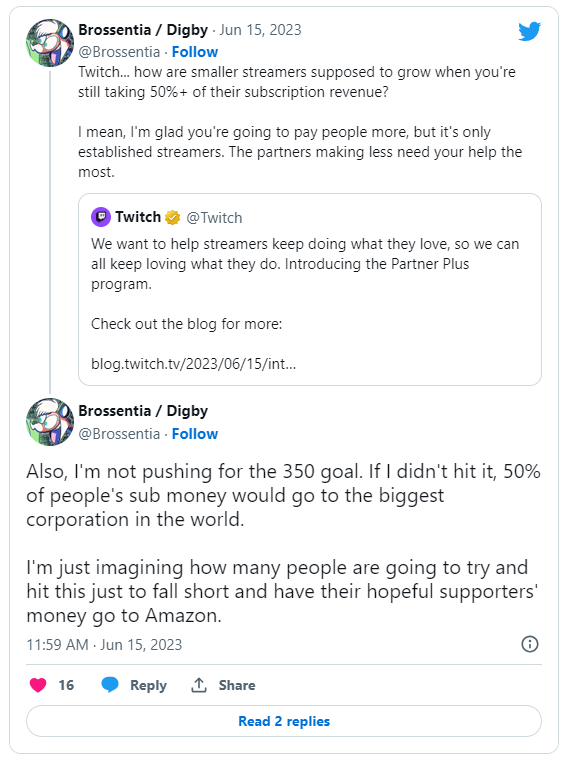
Listening and communicating: this continues to be the challenge at Twitch and it’s frankly getting very frustrating to tread this same ground over and over again. The easiest way Twitch can lose ground as a platform is by pissing off its most important asset: the creative community. The optics of Amazon’s ownership certainly don’t help matters, given the huge sums of money Amazon already generates for itself.
So come on down from the crystal tower, folks. Come talk to your community and learn what makes them tick. And maybe, just maybe, build a platform around that community rather than trying to dictate to them when they have other options in the marketplace.
Filed Under: communications, revenue split, streamers
Companies: twitch
Law Enforcement Hack Of Encrypted Chat Service Involving 30,000 Phones Being Challenged In European Courts
from the basically-an-untargeted-bulk-collection dept
For at least 3 months in early 2020, France-based EncroChat wasn’t in sole control of its communication services. Its servers had been compromised by European law enforcement — a joint effort involving law enforcement agencies located in France, the UK, and the Netherlands.
Authorized by a single court order from a French court, the Joint Investigative Team (JIT) infiltrated EncroChat servers and began intercepting text messages and recording lock screen passwords. The encryption EncroChat provided was never compromised. Instead, malware deployed via the compromised servers allowed law enforcement to extract data and communications from infected devices and, in some cases, disable remote wipe features.
The fallout from the three-month bulk harvesting of data and communications from nearly 60,000 phones was immense. More than 100 million messages were intercepted, leading to hundreds of raids, thousands of arrests, and thousands of kilograms of drugs seized.
The fallout continues, with hundreds of criminal prosecutions underway in several nations. And hundreds of cases means dozens of evidentiary challenges, especially when it appears the entire operation was authorized by a single court order issued by one judge in only one of the nations where prosecutions are currently occurring.
Matt Burgess of Wired has taken an in-depth look at the ongoing battles over the legality of this hacking and the ensuing massive data haul. Complicating matters for prosecutors is the fact that the data was harvested in France but passed on to law enforcement in other countries, possibly in violation of recipient countries’ laws.
Across Europe, legal challenges are building up. In many countries, courts have ruled that messages from EncroChat can be used as evidence. However, these decisions are now being disputed. The cases, many of which have been reported in detail by Computer Weekly, are complex: Each country has its own legal system with separate rules around the types of evidence that can be used and the processes prosecutors need to follow. For instance, the UK largely doesn’t allow “intercepted” evidence to be used in court; meanwhile, Germany has a high bar for allowing malware to be installed on a phone.
The unknown aspects of the remote access malware is one of the issues being discussed in German courts. Another concern being raised is how the data was shared by European law enforcement, including the German beneficiaries of this France-based infiltration.
There are multiple cases now headed to European Union courts, thanks to questions raised at the local level by defense lawyers. And, as Burgess points out, there’s one major case on the docket that could alter the evidentiary attack plans of others challenging this three-month, 100 million message “search” by the JIT.
In October, the French Court of Cassation questioned previous EncroChat legal decisions and said they should be re-examined. “The judge who authorized this measure was not in charge of 60,000 investigations, but only one, and therefore ordered a disproportionate act,” say lawyers Robin Binsard and Guillaume Martine, who are challenging the collection of the data. “We have to defend our clients without knowing how the investigators acted,” they say.
The issues of these cases are reminiscent of the FBI’s “Playpen” investigation. After compromising a dark web server hosting CSAM, the FBI deployed malware to users connecting to the site, allowing it to harvest device IDs, lP addresses, and other information it could use to identify investigation targets. The FBI’s search was authorized by a single court in Virginia but its malware was distributed to 8,000 computers in 120 countries.
In almost every case, the search performed by the FBI’s NIT (Network Investigative Technique) occurred outside of the jurisdiction it was supposed to be limited to. In almost every case, the FBI came away with a win, with judges deciding the extraterritorial searches violated the law but awarding good faith to the FBI because the (illegal) searches were authorized by a judge.
The same problems are evident in the EncroChat cases, only on a much more massive scale and with dozens of different countries and their laws implicated. And just like in the FBI NIT cases, prosecutors are refusing to hand over information about the malware deployed by law enforcement. We’ll have to see if they’re as willing to dump criminal cases if courts rule this information must be handed over to defendants. It’s going to take a long time to sort this all out. European law enforcement agencies are currently basking in the glow of successful, multi-national disruption of organized crime. But that glow will fade fast if courts begin ruling too much was done with too little judicial oversight — oversight that appears may have been misled about the breadth and depth of the search effort it authorized.
Filed Under: communications, encryption, evidence, france, germany, hacking, privacy, surveillance, uk
Companies: encrochat
TECHLASH 2.0: The Next-Gen TECHLASH Is Bigger, Stronger & Faster
from the escalation dept
The roll-out of the “Facebook Papers” on Monday October 25 felt like drinking from a fire hose. Seventeen news organizations analyzed documents received from the Facebook whistleblower, Frances Haugen, and published numerous articles simultaneously. Most of the major news outlets have since then published their own analyses on a daily basis. With the flood of reports still coming in, “Accountable Tech” launched a helpful aggregator: facebookpapers.com.
The volume and frequency of the revelations are well-planned. All the journalists were approached by a PR firm, Bryson Gillette, that, along with prominent Big Tech critics, is supporting Haugen behind-the-scenes. “The scale of the coordinated roll-out feels commensurate with the scale of the platform it is trying to hold accountable,” wrote Charlie Warzel (Galaxy Brain).
Until the “Facebook Papers,” comparisons of Big Tech to Big Tobacco didn’t catch on. In July 2020, Mark Zuckerberg of Facebook, Sundar Pichai of Google, Jeff Bezos of Amazon, and Tim Cook of Apple were called to testify before the House Judiciary Subcommittee on Antitrust. A New York Times headline claimed the four companies prepare for their “Big Tobacco Moment.” A year later, this label is repeatedly applied to one company out of those four, and it is, unsurprisingly, a social media company.
TECHLASH 1.0 started off with headlines like Dear Silicon Valley: America’s fallen out of love with you (2017). From that point, it becomes a competition “who slams them harder?” eventually reaching: Silicon Valley’s tax-avoiding, job-killing, soul-sucking machine (2018).
In the TECHLASH 2.0 era, the antagonism has reached new heights. The “poster child” for TECHLASH 2.0 – Facebook – became a deranging brain implant for our society or an authoritarian, hostile foreign power (2021). In this escalation, virtually no claim about the malevolence of Big tech is too outlandish in order to generate considerable attention.
As for the tech companies, their crisis response strategies have evolved as well. As TECHLASH 2.0 launched daily attacks on Facebook its leadership decided to cease its apology tours. Nick Clegg, *****Facebook VP of Global Affairs, provided his regular “mitigate the bad and amplify the good” commentary in numerous interviews. Inside Facebook, he told the employees to “listen and learn from criticism when it is fair, and push back strongly when it is not.”
Accordingly, the whole PR team transitioned into (what company insiders call) “wartime operation” and a full-blown battle over the narrative. Andy Stone combated journalists on Twitter. In one blog post, the WSJ articles were described as inaccurate and lacking context. A lengthy memo called the accusations “misleading” and some of the scrutiny “unfair.” Zuckerberg’s Facebook post argued that the heart of the accusations (that Facebook prioritizes profit over safety) is “just not true.”
On Twitter, Facebook’s VP of Communications referred to the embargo on the consortium of news organizations as an “orchestrated ‘gotcha’ campaign.” During Facebook’s third-quarter earnings call, Mark Zuckerberg reiterated that “what we are seeing is a coordinated effort to selectively use leaked documents to create a false picture about our company.”
Moreover, Facebook attacked the media for competing on publishing those false accusations: “This is beneath the Washington Post, which during the last five years competed ferociously with the New York Times over the number of corroborating sources its reporters could find for single anecdotes in deeply reported, intricate stories,” said a Facebook spokeswoman. “It sets a dangerous precedent to hang an entire story on a single source making a wide range of claims without any apparent corroboration.”
Facebook’s overall crisis response strategies revealed the rise of VADER:
- Victimage – we’re a victim of the crisis
- Attack the accuser – confronting the person/group claiming something is wrong
- Denial – contradicting the accusations
- Excuse – denying intent to do harm
- Reminder – reminding the past good works of the company.
The media critics describe the current backlash as overblown, full of hysteria, and based on arguments that don’t stand up to the research. More aggressively, a Facebook employee told me: “If in this storyline, we are Vader, then the media is BORG – Bogus, Overreaching, Reckless, and Grossly exaggerated.” Leaving aside the crime of mixing “Star Wars” and “Star Trek,” we can draw a broader generalization:
Both the tech coverage and the companies’ crisis responses have evolved in the past few weeks. We moved from a peaceful time (pre-TECHLASH) to a Cold War (TECHLASH 1.0) and now “all Hell breaks loose” (TECHLASH 2.0).
“Product Journalism” still exists around new devices/services, but the recent “firestorm” teaches us a valuable lesson. The Next-Gen of TECHLASH is bigger, stronger and faster – just like the tech companies it’s fighting against.
* In another move from the playbook, Facebook was rebranded as Meta. Since Meta means Dead in Hebrew (to the world’s amusement), I will refer to Facebook as Facebook for the time being.
Dr. Nirit Weiss-Blatt is the author of The Techlash and Tech Crisis Communication
Filed Under: communications, techlash
