How to secure Azure Functions with Entra ID (original) (raw)
Centralized identity management is vital to the protection of your organization's resources. Do you know how to secure Azure Functions with Entra ID to optimize data security?
Securing Azure Functions is paramount to protecting sensitive data and maintaining the application's security and resilience.
Organizations can mitigate potential risks by implementing security measures, such as role-based access control (RBAC), encryption and regular security assessments. Logging and monitoring mechanisms can provide valuable insights into any security incidents or possible threats, enabling proactive responses. Selecting the appropriate authentication flow for your application can provide further protection.
By following these best practices, you can create a secure, efficient and user-friendly environment for Azure Functions using Microsoft Entra ID.
Why secure with Entra ID?
Entra ID, formerly known as Azure Active Directory, is essential for centralized identity management. It provides a system with integrated Microsoft services, which simplifies user access and credential management. This centralized system enables administrators to control and monitor access from a single point. Entra ID supports many authentication protocols and security standards, ensuring secure and efficient management of user identities.
One helpful feature is Entra ID's RBAC. It assigns specific permissions to users, ensuring only authorized individuals can access sensitive functions and data. By using RBAC, organizations can adhere to the principle of least privilege and reduce the risk of security breaches. Entra ID's integration with other Azure services streamlines security policies and facilitates consistent security measures across Azure resources.
Entra ID also offers advanced auditing and logging capabilities to enhance security. It supports single sign-on (SSO) and multifactor authentication (MFA), while audits and logs keep detailed records of access and activities. These records help organizations quickly detect and respond to suspicious behavior. SSO simplifies UX by allowing access to multiple applications with a single set of credentials. MFA adds an extra layer of security by requiring additional verification steps. These features work to improve security, compliance and user convenience in Azure Functions.
Choose the right authentication flow
Proper authentication flow is essential when integrating Entra ID with Azure Functions. Entra ID offers different authentication flows for various types of applications and scenarios. Understanding these flows can help you implement the best authentication strategy for your application.
Entra ID authentication flows
Authentication flows determine how users prove their identity to access applications and resources. These flows outline the steps involved in securely exchanging information among the user, application and Entra ID. This includes obtaining authorization codes, exchanging them for tokens and validating them to ensure the user's identities.
Different applications require different flows, from single-page apps to mobile and desktop applications, each with security considerations and tradeoffs. Authentication flows in Entra ID include the following:
- Authorization code flow. This flow works for web and native applications that require secure, server-side token handling. It involves a two-step process where the application requests an authorization code and exchanges it for an access token. This flow is highly secure because the token is never exposed to the user agent, making it ideal for high-security applications.
- Implicit flow. Typically used by single-page applications running in a browser, this flow is more straightforward but less secure than the authorization code flow. It enables the application to obtain an access token from Entra ID without an intermediate authorization code. Due to the direct token exposure, it is only recommended for applications where a short-lived token is acceptable and can be securely handled.
- Client credentials flow. This flow is for server-to-server communication without user context. The application authenticates itself using its credentials, such as a client ID and secret, to obtain an access token. It is ideal for background services, daemons and APIs that need access to resources or perform operations independently.
- Device code flow. This code flow enables users to authenticate via a secondary device. The application presents a code to the user, who then authenticates on a separate device to approve the request. It is designed for devices with limited input capabilities, such as smart TVs or IoT devices. This flow provides a convenient and secure way for users to authenticate themselves on devices with constrained UIs.
Factors to consider when choosing a flow
It is crucial to consider security when choosing an authentication flow. Applications that handle sensitive data or require high security should use flows that minimize token exposure, such as the authorization code flow. Scenarios with lower security requirements might choose the implicit or device code flows.
The selected authentication flow should offer users a seamless and intuitive experience. For example, the device code flow enables users to authenticate themselves on devices with limited input capabilities. This enhances usability without compromising security. The authorization code flow ensures a smooth experience for web and native app users by securely handling tokens in the background.
By considering these factors and understanding their capabilities, you can select the Entra ID flow that balances security, UX and application requirements. This ensures that the Azure Functions environment is both secure and user-friendly.
How to secure Azure Functions with Entra ID
To protect Azure Functions with Entra ID, follow these steps:
- Register the Azure Functions app in Entra ID. This involves setting up the Azure Functions app within the Entra ID authentication system to enable secure access control.
- Configure authentication in Azure Functions. Set up the necessary authentication settings within the Azure Functions app to ensure only authorized users or applications can access the function.
- Authorize access. Define the function's specific access controls and permissions, specifying who can invoke it and what actions they can perform.
- Implement authentication in client applications. Ensure any client applications that must invoke the function are correctly configured to handle the authentication process.
To secure Azure Functions, navigate to Azure Portal, and click into Azure Function. Within the Settings section, choose Authentication,and then select Add Identity Provider. Choose a provider from the drop-down, such as Microsoft.
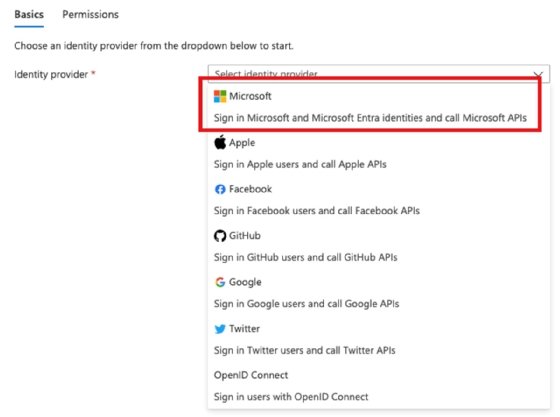
Select from the identity provider drop-down menu.
The next step is determining whether the Azure Functions app is available for internal or external users. For this example, select Workforce configuration, which only supports the current Entra ID tenant.
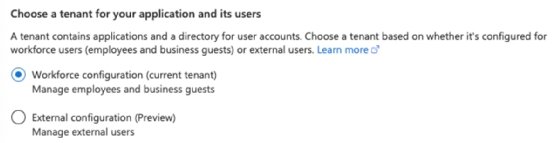
Select either a Workforce or External configuration for your application.
Next, pick an existing app registration, or create one. Registration entries, such as an app or account, control all security. It is no different for Azure Functions apps.
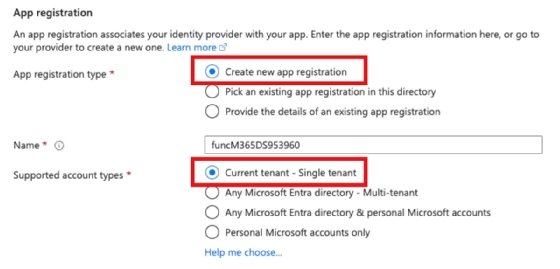
Create a new app registration, or select from an existing one.
Set your Azure Functions app's additional checks and app service authentication settings.
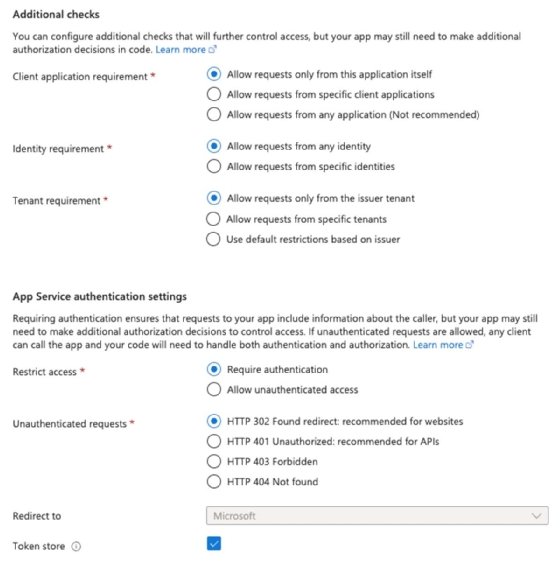
Configure additional control access checks using the options provided.
Next, assign the required permissions. Select Next: Permissions, where you can then add any Microsoft Graph permissions. By default, the assigned permission is User.Read. You can add more permissions, like when manually creating an app registration. For example, for a function app that creates users in Entra ID, you need to assign more permissions, such as the one here:
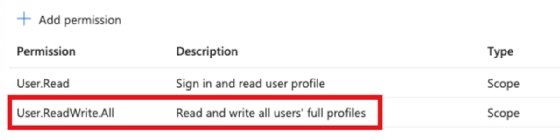
Assign required permissions by selecting Next: Permissions.
Once you have added the required permissions, select the Add button to save the new configuration.
To test the authentication, navigate to the Azure Functions app. Click on the specific function, choose Get function URL and launch it within a browser window.
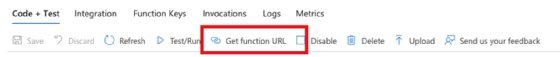
Select Get function URL, and test your authentication in a new browser window.
As you browse the URL, it should immediately direct you to the Entra ID consent window if you are logged in. If you are not, it asks you to log in and then requires consent.

The Entra ID consent window appears if you are logged in.
The advantage of protecting the Azure Functions app this way is all security controls within Entra ID are for account protection. Features such as MFA and RBAC work together to ensure security.
Though this option is secure and works well, be careful of the allowed approach based on how other applications or organizations consume the Azure Functions app. For example, enforcing MFA might fail if the consuming application cannot meet that requirement.
Liam Cleary is founder and owner of SharePlicity, a technology consulting company that helps organizations with internal and external collaboration, document and records management, business process automation, automation tool deployment, and security controls and protection. Cleary's areas of expertise include security on the Microsoft 365 and Azure platforms, PowerShell automation and IT administration. Cleary is a Microsoft MVP and a Microsoft Certified Trainer.
 Managed identity vs. service principal for Azure apps
Managed identity vs. service principal for Azure apps  By: Liam Cleary
By: Liam Cleary  Nerdio introduces Multi Entra ID for complex IT environments
Nerdio introduces Multi Entra ID for complex IT environments  By: Adrian Bridgwater
By: Adrian Bridgwater  Microsoft to roll out mandatory MFA for Azure
Microsoft to roll out mandatory MFA for Azure  By: Arielle Waldman
By: Arielle Waldman  Learning the features and limitations of MSIX app attach
Learning the features and limitations of MSIX app attach  By: Marius Sandbu
By: Marius Sandbu