Comparing web browser privacy and security features (original) (raw)
Article 3 of 3
Part of: Comparing web browsers for use in a business setting
While the four most common browsers -- Chrome, Edge, Firefox and Safari -- have largely the same feature sets, there are subtle differences when it comes to privacy and security.
Internet security is critical for all organizations, and the main connector between end users and harmful content on the internet is the web browser.
As such, browser security is of paramount importance, and browser privacy is a key component of browser security. Popular browsers -- such as Chrome, Edge and, to a lesser extent, Safari -- are provided by companies that sell user data to advertisers and other third parties.
In addition, browsers store passwords, usernames and other account security information that can be a significant target for hackers, even though the information is encrypted. Much of this information is held in cookies and a user's favorite sites are part of a saved history, which the browser providers can sell.
In organizations that minimize these risks by disabling autocomplete of usernames and passwords or purging cookies, users will have to enter a username and password to every webpage that asks for it. Yet, security and privacy shouldn't have to come at the cost of UX.
There are security features that these browsers employ to ensure privacy and security, but there is no real way to ensure complete privacy and security protections from all attack vectors, adware and other concerns. A secure browser is important to everyone in the organization, whether they have access to financial or classified information or not. So, organizations are best off finding the right mix of acceptable use policies and technologies to implement across the enterprise.
Browser security threats and tools
Organizations should begin the browser evaluation process by looking into what threats they have to combat. While this threat list covers many modern threat vectors, new methods for attack may come up. IT teams should stay abreast of any new browser security updates.
From there, IT teams can determine which browser works best and what tools they should use to supplement and support the use of the web browser.
Threats
One of the biggest threat vectors that organizations need to address is phishing. These types of attacks are highly effective and are often the entry point for cybercrime attacks, such as advanced persistent threats and ransomware. They involve tricking a user into clicking on a link to a compromised website and entering passwords, personal data or financial information. All a hacker needs is one user to download malware that is included in a game, video or other data, and then they can access the corporate network.
Organizations are best off finding the right mix of acceptable use policies and technologies to implement across the enterprise.
A Cisco report stated that the four most prevalent security threats are cryptomining, phishing, Trojans and ransomware, in that order, which account for 100 million threats a month. All other threats accounted for 10% of that combined total. Cisco's study also reported that 86% of participating organizations had at least one user try to connect to a phishing site, and 70% had users obtain malicious browser ads. Cisco also estimated that 90% of data breaches start from phishing. It is important to address phishing as part of corporate security and in harmony with browser security.
Phishing typically occurs through email but leads to a website. When selecting a browser, it is important to consider the antiphishing features.
Other threats that IT teams must protect against include the following:
- redirects, which send users to nefarious websites by tricking the user or using a fake front masquerading as the legitimate sites;
- pop-up ads that can't be closed or bombard the user with pop-ups on random actions on legit websites;
- attack vectors provided through OS or browser security failures;
- plugins and browser extensions from untrusted or falsified sources;
- password leaks from a browser's password storage; and
- browser history and cache that can be read and tracked.
Tools
Perhaps the most important preventive step that IT teams can take to minimize browser attacks is simply end-user education. Security technologies can't completely protect the enterprise from attacks if the users open the door and let attackers bypass security measures. Many organizations require annual training to teach users how to identify phishing and other attacks via browsers. These trainings cover email and other social engineering vectors as well. This will yield better results than draconian browser use policies or pouring massive amounts of resources into complex security platforms.
That said, there are tools and security software platforms that can add value:
- Pop-up blockers. While these help prevent some pop-up ads, they also prevent some pop-ups that request user-entered information such as login credentials or a form submission. Hackers have found ways around most of these blockers, so this technology may be solving more of the outdated problem of constant pop-ups.
- Native OS and browser controls. IT teams can mitigate failures in base OS and browser security with an aggressive corporate patch management policy. Viruses, security leaks and backdoors quickly receive patches from vendors, but viruses enter before the patches are implemented. Applying patches in a timely fashion is challenging but essential to a secure end-user environment.
- Antivirus software. These tools provide adware removal and password management. They are usually more effective than the native browser features. Note: These tools may also include pop-up blockers.
- Content blockers. These are effective tools for blocking phishing attacks by preventing malicious information from being displayed. IT can usually add content blockers via an extension, such as uBlock Origin. These will filter lists, ads and tracking and maintain a malicious URL blocklist. Website blocklists and allowlists can also help filter out harmful content.
- Personal website blocking. Browsers enable users to specifically add or remove websites from the accessible options of the browser. IT and business leaders can manage these lists to respond quickly to new threats.
- Forcing HTTPS. HTTPS is the secure HTTP protocol to which browsers can force the user to navigate. Some browsers will display a notification and let the user choose between these protocols, but IT can impose these controls.
- Disabling autocomplete, blocking cookies, purging browser cache. These are specific controls that IT teams can employ to minimize security or privacy risks. In addition, IT can block the browsers from storing passwords. These steps will make a more secure environment, but there may be a steep price to pay in terms of end-user happiness and productivity. Disabling any of these will result in the users having to enter login credentials at the start of every site visit, including passwords, usernames, etc. There is a middle ground where IT can purge cookies and the browser cache periodically and sometimes gradually configure autocomplete.
- Using third-party password managers. Many antivirus products include password managers. These editions are safer and more effective than in a free browser.
- Using virtual browsers. Rather than a browser on an endpoint device, organizations can run a web browser hosted in a virtual environment and deliver it to end users. Malicious software cannot get to the actual end-user device and thus would not be able to install harmful software.
- JavaScript blocker. The danger of JavaScript is that it's nearly impossible to prevent hackers from viewing and stealing information from it. Of course, not all scripts are dangerous -- but it is so popular that blocking it isn't practical. Further, Google won't allow disabled JavaScript users to sign in to Google accounts. Thus, blocking JavaScript would be safe but it would render the internet useless to most workers. If IT can block certain types of scripts, that will be the best option for most organizations.
- Extensions. Application libraries vary on their policing of nefarious extensions. Chrome extensions from the Chrome Web Store, for example, are safer than extensions from Google Play. Extensions from Safari are safe because Apple is strict. Chrome extensions, for the most part, will work with other Chromium-based browsers such as Microsoft Edge. Firefox extensions should come from Mozilla's main page to be safe. Many extensions are desirable for both end users and IT professionals because they can improve UX, security and privacy.
- Some recommended extensions include Web of Trust, LastPass, NoScript and 1Password, but there are plenty of other viable options. IT teams simply need to test the extensions and verify their efficacy and reliability.
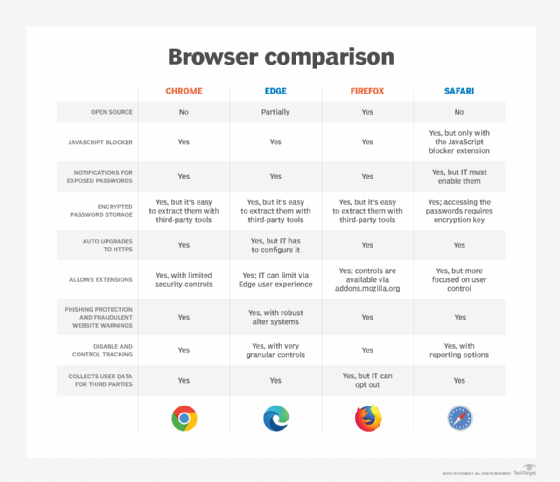
Web browser privacy comparison
The browser market is dominated by a few major players, with Google Chrome leading the pack. Mozilla Firefox, Microsoft Edge and Apple Safari round out the top four in terms of market share. There are new browsers that are more secure in many ways, including in how they keep your privacy protected and sell your data to sponsors. These other browsers include Brave, Opera and Vivaldi.
A comparison of the top four browsers shows very minor differences in security features. For example, all four of these browsers offer cookie management, password storage for autofilling, browser history and cache management, and custom site blocking.
Still, it's important to know exactly what features each browser has. Further, IT may add extensions to supplement a browser with additional functionality.
What steps should IT teams take to secure browsers?
It's difficult to name a single best browser -- even from a privacy or security perspective -- because there are not a lot of unique features across the browser market. Thus, it comes down to what users are comfortable working with and what IT teams are comfortable managing. Imagine the effect on users that a switch from Chrome to Firefox would have. It would create a new learning curve, a dip in productivity and a spike in support calls to the help desk.
Users would have to figure out how to handle migrating bookmarks, remembering passwords that were stored in the browser and losing their browsing history. If there is a valid reason to go through with a migration of this nature, then it can be done. However, the reason should justify the price that will be paid in productivity and user frustration.

With all of this in mind, the following recommendations address privacy and security concerns that an organization should consider while forming a browser policy:
- User training. Identify best practices and develop or purchase simple online training that will teach users to avoid accessing compromised sites. Users should complete this training on at least an annual basis.
- Always patch. Keep the OS, applications and the browser patched as quickly as possible.
- Antivirus. Install a competent antivirus product and keep it updated.
- Assess the browser, manage extensions. Determine the strong and weak points of the existing browser to determine if there are extensions that can improve these weaknesses. Add trusted extensions and avoid unknown ones. Ensure that users aren't adding potentially dangerous extensions as well.
- Define industry recommended security policies. Take the industry standards for browser policies and adapt them to the given organization. Deploy them through global policies to both browsers and related software applications.
- Define and implement password policies. Organizations should use strict password standards and policies that account for password length, password lifetime and strong password syntax. They should also strongly consider multifactor authentication when possible. IT teams may even want to employ passwordless applications or access points.
Dig Deeper on Application management
-
 What is a potentially unwanted program (PUP)?
What is a potentially unwanted program (PUP)?  By: Alexander Gillis
By: Alexander Gillis -
 Microsoft Edge
Microsoft Edge  By: Kinza Yasar
By: Kinza Yasar -
 Google Chrome browser
Google Chrome browser  By: Nick Barney
By: Nick Barney -
 Firefox
Firefox  By: Nick Barney
By: Nick Barney
Part of: Comparing web browsers for use in a business setting
Article 3 of 3