legacy system (legacy application) (original) (raw)
What is a legacy system?
A legacy system is any outdated computing system, hardware or software that is still in use. Legacy systems include computer hardware, software applications, file formats and programming languages. However, not all legacy systems are obsolete technologies. Most legacy systems work even if they are outdated, and enterprises will often continue using legacy systems that are critical to their daily functions and business needs.
Applications, systems and other technologies become legacy IT systems for the following reasons:
- They no longer receive updates, support or maintenance from their software developers or creators.
- They are no longer available for purchase or depend on obsolete technology to run and maintain.
- In the case of hardware such as mainframes, they are no longer able to support an organization's software.
- The system requires IT professionals with complex, largely outdated technology skill sets such as Common Business-Oriented Language, or COBOL, programming to maintain. These professionals can be difficult to find and costly to hire.
- Repairs take too long compared with new systems.
- Maintenance costs become too excessive to continue.
- They are overexposed to security vulnerabilities and cannot be updated to meet modern cybersecurity standards.
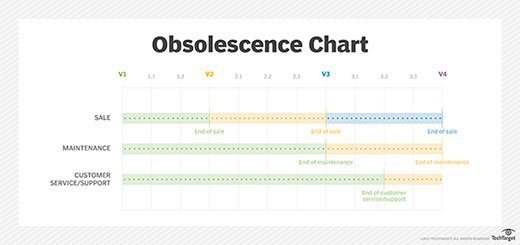
Sale, maintenance and customer service all factor into whether a system is obsolete.
What are legacy applications?
A legacy application, or legacy app, is a software program that is outdated or obsolete. Although a legacy app still works, it might be unstable because of compatibility issues with current operating systems (OSes), browsers and IT infrastructures.
Most enterprises use legacy applications and computer systems that continue to serve critical business needs. Typically, the challenge is to keep the legacy application running while converting it to newer, more efficient code that makes use of current technology and programming languages.
A legacy app is frequently tied to a specific version of an OS or coding language. For example, an application built to run on Windows 7 might not be able to run on Windows 10, despite middleware or glue code added by an application development team or the OS being generally backward compatible.
Types of legacy systems
The following are four common types of legacy systems:
- End of life (EOL). EOL legacy systems are ones that a vendor or developer has stopped supporting or offering updates for, or that are no longer purchasable.
- Inability to scale. These legacy systems no longer have the scalability to support a business's growing data, performance or security needs.
- Heavily patched software. A lot of legacy software is outdated software that has been extensively patched in the past to keep it up to date. Extensive patching -- and especially incomplete patching -- can make software more vulnerable to security breaches than modern applications and lead to its discontinuation.
- No one knows how to maintain it. A lot of legacy systems require outdated knowledge to maintain. This makes it difficult and costly to find an IT expert who knows how to maintain it.
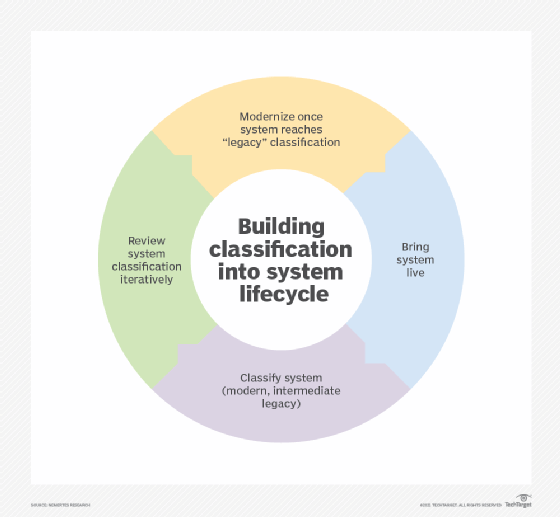
Classifying legacy systems is the first step to knowing whether they should be modernized or not.
Why are legacy systems and applications still used?
Organizations continue to use legacy systems and applications for the following reasons:
- They still work. Many legacy systems and applications work and are important to a business's daily functions. Replacing systems and technologies that still work simply because they are outdated is not always necessary.
- Costs. The cost of replacing a legacy system or application can be high. While maintaining legacy systems can cost enterprises more money long-term, some organizations do not have the immediate resources to modernize their systems. Upgrading can also require long periods of time, retraining staff or hiring staff to learn and integrate the new technologies. Some organizations also keep outdated systems because they have not yet recovered the investment for them.
- Complexities and challenges. Modernizing legacy systems can be complex undertakings. Some organizations don't have the skill set to modernize their systems and to handle the challenges that can come with doing so. Service delays, data loss and poor user experience can also result from migrations.
Risks of keeping legacy systems and applications
There are several risks associated with keeping legacy systems and applications, including the following:
- Maintenance and operating costs. Many organizations keep legacy systems and applications because of the high costs of replacing them. However, maintaining legacy technologies over the long term can be expensive. Legacy systems won't be updated by their developers. As a result, they require ongoing maintenance from IT teams. Over time, these costs can outweigh the benefits of maintaining the status quo.
- Performance. When a vendor's software development team no longer supports an application, it can be difficult for an operations team to keep the software running. As legacy systems age, continuing to use them can result in slower performance, higher resource consumption, and more frequent failures and crashes. Maintaining old technologies also prevents organizations from taking advantage of new technologies and can weaken their competitive advantage compared with more modernized competitors. Many legacy systems also cannot integrate with newer systems, which can decrease functionality for organizations that have a mix of old and new technologies.
- Data silos. A data silo is a repository of data that cannot be integrated or shared with the different branches of a business. Many legacy software systems cannot integrate with new software, meaning that data stored on an older system within a business cannot be shared with other departments using newer technology.
- Compliance. Legacy systems might not be up to the standards of data compliance regulations, such as the Health Insurance Portability and Accountability Act and the General Data Protection Regulation. Failure to comply with these regulations can lead to fines and other penalties, as well as negative publicity and security breaches.
- Support and security. Legacy systems do not receive technical support or updates from their developers and depend on outdated security measures or patches to prevent breaches. This makes them vulnerable to data breaches, which cost on average $4.35 million for organizations, according to IBM's 2022 "Cost of a Data Breach" report conducted by the Ponemon Institute.
Legacy systems modernization and migration
Legacy systems and applications cannot be maintained at a functioning level forever. At some point, most enterprises will update or replace outdated hardware, coding language, OSes and software.
Legacy system and software modernization and migration often involves refactoring, which is the restructuring of a system's code to make it compatible with a new platform. An enterprise conducting a legacy system modernization or migration must first evaluate which components of its system need to be addressed. Research firms such as Gartner suggest organizations follow these steps:
- Identify which components of the system or application are no longer meeting standards or requirements for business processes and must be modernized or upgraded. Organizations should consider functionality and cost.
- Evaluate modernization or migration options. For example, a team considers moving to a software-as-a-service approach with application programming interfaces, or APIs, that free the application from ties to a specific OS and make future updates simpler. An enterprise can also redistribute the location of its application and data between on-site data centers and public cloud platforms using infrastructure as a service.
- Choose the option that will most benefit the organization's architecture, scalability and functionality.
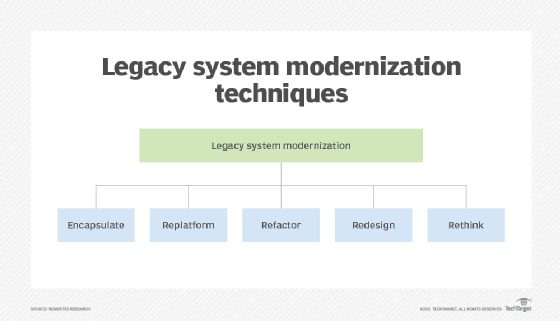
Refactoring is just one of several helpful techniques to modernizing legacy systems.
Once a method is chosen, data migration becomes important. It also often involves data conversion and the following steps:
- Extraction. Data extraction can be difficult because a lot of data stored in legacy systems is siloed or stored in outdated formats. Before data migration begins, organizations must make sure the business-critical data can be extracted.
- Data mapping. The data must be converted to the new system's formats and requirements using data mapping. Often, old data does not map exactly to the new information system.
- Updating the data. All incomplete and nontransferable data should be deleted and all duplicate data deduplicated.
- Test the migration. Organizations should run a test on a sample data set. This way, errors and bugs can be identified before the real data migration begins.
- Migrate the data. Once organizations have extracted, mapped, updated and tested their data, they can safely migrate it to their new platform.
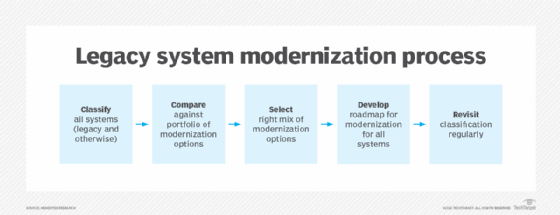
These are the steps enterprises take when modernizing a legacy system.
Examples of a legacy system
Legacy systems are crucial to many organizations such as banks and government agencies. These organizations depend on proven, consistent and reusable technologies that are often expensive to develop and cost-prohibitive to replace. Examples include the following:
- NASA's Orion spacecraft. NASA's Orion spacecraft runs on outdated IBM PowerPC 750X single-core processors, a technology from 2002. Orion itself has been in development since 2000 and is set to launch for the first time in 2022.
- Microsoft Internet Explorer (IE). Microsoft ended support for all versions of Internet Explorer prior to version 11 in January 2020. Support for IE11 ended in June 2022. Organizations can use the IE mode of Microsoft Edge to access applications and websites that still rely on IE.
Legacy systems are often migrated to the cloud. Figure out which cloud migration service meets your data and server needs.
This was last updated in November 2022
Continue Reading About legacy system (legacy application)
- 12 cloud ERP data migration best practices
- HR data migration checklist and tips for implementation success
- Legacy vulnerabilities may be biggest enterprise cyber-risk
- Application virtualization breathes digital life into legacy apps
- The decision to upgrade a legacy ERP system vs. replace it
 How to migrate legacy applications to the cloud
How to migrate legacy applications to the cloud  By: Adam Bertram
By: Adam Bertram  7 steps to migrate ECM systems to the cloud
7 steps to migrate ECM systems to the cloud  By: Laurence Hart
By: Laurence Hart  cloud modernization
cloud modernization  By: Andy Patrizio
By: Andy Patrizio  SAP dangles bigger carrots for S/4HANA Cloud, Rise
SAP dangles bigger carrots for S/4HANA Cloud, Rise  By: Jim O'Donnell
By: Jim O'Donnell