Compare BYOD vs. CYOD vs. COPE vs. COBO for a mobile strategy (original) (raw)
Organizations recognize the need for flexibility when it comes to supporting employee mobile devices. They must balance what employees want with what IT and security require.
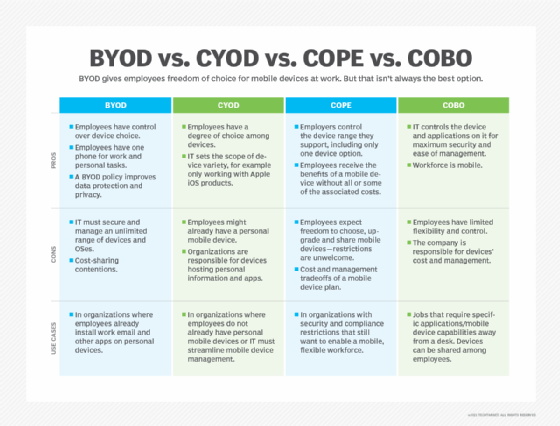
Companies can choose among four enterprise mobility management strategies:
- bring your own device (BYOD);
- choose your own device (CYOD);
- company-owned, personally enabled (COPE) devices; and
- company-owned, business-only (COBO) devices.
BYOD is one of the most popular mobile device management options, including in companies that have no formal mobile device management (MDM) policy. However, with security concerns and limited controls associated with BYOD, COPE, CYOD and COBO are making a comeback.
When weighing BYOD vs. COPE vs. COBO vs. CYOD for a mobile device policy, the IT team should strive for a functional and feasible approach that is acceptable to both the employees and their organization.
What are the basics of BYOD and is it a good idea?
BYOD refers to any employee-owned type of device -- typically a smartphone or tablet -- that is used for work. Many employees configure their personal cell phones with their work email and use the device for work-related activities. They might install apps that they use to do their jobs, either internal apps or apps that require their work login information.
Bringing their own personal device to work offers the most flexibility for employees, but does not mean the best protection for the company. BYOD adopters should consider investing in protection tools that support BYOD and add layers of security. Mobile application management (MAM) puts controls around the corporate apps on personally owned devices, isolating them from the employee's personal apps while ensuring encryption and other security measures.
What are the characteristics of CYOD and how different is it from other mobile policies?
CYOD gives the company more control than BYOD, because the company offers a range of brands or models of smartphones and tablets that employees select as their work and personal device. Some companies consider CYOD a viable option to give employees flexibility. The IT team can fully lock down and manage the device, while still allowing personal use as well.
With CYOD, IT can enforce certain security policies on the device. Typical restrictions include complex password requirements, IT approval for app installs, content filtering and GPS tracking. Mobile device management tools enable IT teams to remotely update and oversee CYOD devices.
What does COPE bring to the table?
CYOD is one version of COPE, but not the only one. The corporate-owned and personally enabled policy for devices gives the company ownership and control over the device. Employees might have input on device make and model, or they might not.
Organizations might select a COPE strategy if employees are not currently using a mobile device or not willing to continue to pay for their personal device plans. Employees must be willing to adopt a company-owned device that gives them the flexibility to conduct personal activities on it as well.
What is a COBO policy and when does it make the most sense?
COBO is the most restrictive policy for tablets, smartphones or other device types. The company owns and controls use of the device.
Under a COBO policy, the corporate-owned device runs business-only apps. These devices might be shared by multiple employees. For this reason, COBO policies are typical for employees such as field techs and warehouse workers.
Consider a COBO policy if there is a limited set of use cases for the mobile devices and security is a concern. COBO is a good fit when multiple users access the device, because it does not make sense for these employees to store personal information or install personal-use apps.
How do you choose between BYOD, CYOD, COPE and COBO?
IT has multiple mobile device implementation strategies to choose from in BYOD, CYOD, COPE and COBO. The strategy must focus on security and protection of the network and data. Take into consideration the relevant compliance requirements and which approach provides the best protections for the company.
Moving away from BYOD is not always the answer to security concerns that companies may have. MAM platforms, along with mobile threat defense tools, offer features that can ensure the corporate network is secure when a user brings their personal device for work. These tools reduce a company's risk while enabling device flexibility. Focus on mobile policies that balance the company's IT requirements and employee conveniences.
Pros and cons of BYOD and COPE
Employees generally request the convenience of a single device for work and personal use, privacy and data protection, and cost-sharing policies.
Consolidated devices. Employees like the option to have one single device for personal and work use. This setup is more convenient than having two smartphones to keep up with. BYOD and COPE are favorable to employees because these strategies provide them with one device to use for all activities.
Privacy and protection of personal data. Employees raise concerns about privacy when they have corporate mobile devices for personal use. The IT team likely will implement a MDM or MAM system to protect corporate data. Under this approach, employees need assurance that personal data such as photos, social media accounts and personal texts are not at risk of being leaked or viewed by IT.
Cost. Employees on BYOD or COPE mobile devices can see increased service costs as a result of increased bandwidth or data usage on their cellular data plan, covering their work and personal usage. Employees might expect their company to provide financial support or incentives for their smartphone bill. Without financial support, BYOD and COPE lose favor among employees, as COPE or COBO mean the device and its use are fully owned and paid for by the employer.
Editor's note: Robert Sheldon wrote about BYOD and COPE in 2013. Reda Chouffani updated the article in 2021 to include CYOD and COBO and reflect changing EMM technologies.