How to set up backup internet connections for home offices (original) (raw)
Reliable connectivity and secure access are must-haves for employees working from home. Here are ideas to consider when designing backup internet connections for home offices.
Two factors businesses must consider as they extend work-from-home policies are the reliability of broadband internet to employees' homes and secure access to business applications and data. If employees lose their primary connectivity, it can result in business disruptions that equate to lost revenue.
In many parts of the U.S. -- particularly in rural areas -- broadband can be undependable to the point of negatively affecting an employee's ability to work. This is especially true for remote workers who must always be available using IP-based unified communications tools.
The second component to backup internet connectivity is ensuring employees have secure access into a business's digital resources. Depending on the setup of the primary access architecture, securing access through a backup link might differ.
Let's look at steps enterprises can take to bolster internet connectivity and secure access using a backup internet connection for home offices.
Top methods for creating a backup internet connection for remote work
Backup internet for remote work requires IT teams and employees to make two decisions.
The first consideration is access to the internet itself. In most cases, access takes the form of a second broadband connection to an ISP. The connectivity medium is either a wired or wireless connection. Common types of wired broadband include DSL, cable, fiber, Ethernet and commercial and metropolitan copper. Wireless options are point-to-point Wi-Fi, carrier or private LTE/5G cellular networks, fixed microwave or satellite. In some cases, staff must take care to ensure imposed internet data plans are adequate for remote work if home offices require extended use of the backup connection.
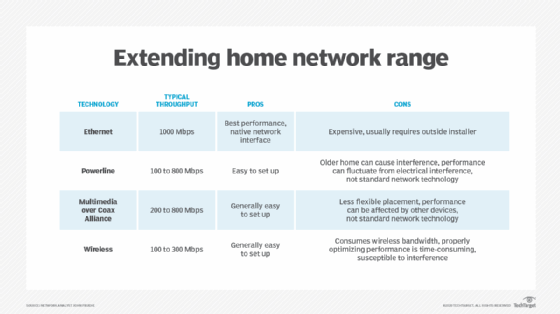
These technologies can help users deploy backup internet connections for a home office or improve their home internet connectivity.
Once staff have determined a secondary path to the internet, the next decision is evaluating how a remote user can access business applications, data and services across the internet in a way that guarantees data security. In many cases, this method is identical to what employees use for a primary internet connection. In some situations, however, a business might provide a direct path to digital corporate services that is solely tied to the primary link. This strategy usually occurs when remote access connectivity uses a direct WAN connection to the corporate network, bypassing the internet entirely. If that's the case, staff must also enable secure remote access for the secondary connection.
Common examples of secure remote access technologies include:
- VPN. VPNs can come in the form of remote access software installed on endpoint hardware or static, site-to-site VPN connections configured on dedicated routers or firewall hardware.
- Software-defined WAN. Similar to site-to-site VPNs, SD-WAN connectivity creates a securely encrypted tunnel over the internet into corporate offices and clouds. The difference, however, is SD-WAN can use primary and secondary paths simultaneously. SD-WAN's built-in path routing intelligence determines which path specific traffic flows should take, using factors such as the priority of specific traffic flows and whether primary or secondary links are operating efficiently. This model can improve overall performance for latency-sensitive business applications and delivers an added layer of reliability for remote users.
- Virtual desktop. Remote users can use any compatible endpoint to reach out to a privately deployed or cloud-based virtual desktop. Once connected, the virtual desktop operates as a standard corporate PC, but all applications and data are kept secure within the virtual desktop infrastructure.
- Secure Access Service Edge. SASE is a relatively new form of secure remote access. Users connected to the internet and seeking to access corporate resources are redirected to a secure edge or cloud. The SASE platform then applies authentication, authorization, SD-WAN and network security to the connection, so remote users can safely access a company's business resources safely and with the best performance possible.
Requirements for a backup internet connection
When reviewing options and architectures for backup internet connectivity, staff must consider several requirements to achieve the utmost in remote access reliability and performance when the primary access connection is lost.
Those requirements include the following:
- Path diversity. This feature ensures that primary and backup connections operate over separate physical paths and access points to the internet, so an upstream outage within an ISP doesn't halt both paths.
- Meet minimum speed and latency requirements. In many cases, a backup internet connection does not deliver the same speed or network latency performance compared to the primary link. This discrepancy is often due to limitations of available secondary connectivity and cost-saving efforts. While it's acceptable to architect backup internet this way, the design must meet the minimum performance needs of the remote user. Otherwise, it's not worth installing backup internet.
- Reliability. Backup connections must be operational and ready to be activated when needed.
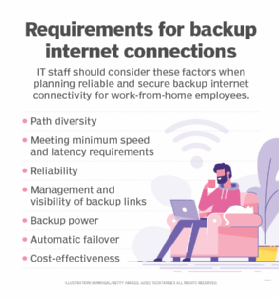
These factors are important when planning backup internet connectivity for home offices.
- Management and visibility of backup links. In-house IT staff must establish visibility into the health of backup links, so they can centrally monitor and manage them. Failing to do so often results in failed backup links going unnoticed.
- Backup power. If possible, staff should set up secondary links on separate backup power, such as an uninterruptible power supply, so remote users maintain internet connectivity during a power outage.
- Automatic failover. When a failover of the primary link occurs, it is ideal that failover to the secondary link be an automated process.
- Cost effectiveness. In some situations, backup internet options are expensive to set up and come with high per-month charges. Staff must conduct a thorough review of those options to ensure the benefits of backup internet connectivity justify the cost.
How to set up a backup internet connection and network
When researching backup internet architectures, staff should follow the steps below to determine what is the best option for the business and corresponding remote users.
1. Determine whether employees need backup internet connections for home offices
The first thing a business must evaluate is whether an employee requires redundant internet connectivity in the first place. Teams should keep this decision process simple. If internet connectivity hinders an employee's ability to perform daily tasks -- and those daily tasks significantly affect business operations -- staff can make a case to procure and install a secondary link.
However, teams must also consider that an internet connection might technically be operational, but the throughput necessary to perform bandwidth-intensive functions overwhelms available bandwidth. In this case, the employee and employer should see if they can increase the broadband upload and download speeds.
Alternatively, businesses can deploy a secondary connection, with both links used simultaneously in a load-balanced manner -- using traditional load balancing techniques, SD-WAN or SASE -- to provide both improved resilience and increased throughput capacity. Keep in mind the technologies required to accomplish this goal can quickly get expensive.
2. Evaluate available backup internet options
Where an employee lives determines the types of backup internet options available. As previously stated, common internet connectivity options for most homes and neighborhoods include fiber-to-the-home cable and DSL. Wireless options include LTE, 5G cellular networks and fixed wireless broadband.
Satellite internet is also an available option in remote areas where other options are not. But keep in mind this technology suffers from longer latency times and low throughput. Some employees could potentially connect through private WAN links, such as metro Ethernet, fiber or point-to-point wireless links, depending on availability or proximity to a business office.
3. Learn how to deploy and manage employees with dual internet connections
Employees often need to install special router hardware in their homes to deploy a backup internet connection that operates either in active-standby mode with automatic failover or in a load-balanced/SD-WAN mode.
Preconfigured modern routing hardware is typically available to make the installation a plug-and-play job any nontechnical employee can handle. Another benefit is the company's IT department can access the remote router to collect and analyze performance statistics for each employee. Ultimately, this streamlines the troubleshooting process when connectivity issues arise.
Next Steps
What is the difference between WLAN and Wi-Fi?
What's the difference between 802.11ac vs. 802.11ax?
Troubleshoot wireless network connection problems in 10 steps
WLAN security: Best practices for wireless network security
Types of wireless network attacks and how to prevent them
Dig Deeper on Network infrastructure
-
 automatic transfer switch (ATS)
automatic transfer switch (ATS)  By: Rahul Awati
By: Rahul Awati -
 SD-WAN deployments feed SASE network and security convergence
SD-WAN deployments feed SASE network and security convergence  By: Ron Karjian
By: Ron Karjian -
 5G and SD-WAN bring benefits to branch locations and beyond
5G and SD-WAN bring benefits to branch locations and beyond  By: Andrew Froehlich
By: Andrew Froehlich -
 How low Earth orbit satellite networks improve internet access
How low Earth orbit satellite networks improve internet access  By: John Burke
By: John Burke
Related Q&A from Andrew Froehlich
Identity management vs. authentication: Know the difference
Learn how authentication and identity management are both intrinsic to an identity and access management framework. Learn how they differ and the ...Continue Reading
Managed vs. unmanaged switches: What are the differences?
Managed and unmanaged network switches differ in various ways, including control and cost. Managed switches support more granular control, while ...Continue Reading
Network automation vs. orchestration: What's the difference?
Automation and orchestration take different approaches to achieve network efficiency. However, network engineers can use them together to create an ...Continue Reading