network segmentation (original) (raw)
What is network segmentation?
Network segmentation is a networking architectural design that divides a network into multiple segments (subnets) with each functioning as a smaller, individual network. Segmentation works by controlling the flow of traffic within the network. Traffic can be restricted in or to segments based on location, along with where traffic can and cannot flow. Traffic flow can also be limited by traffic type, source and destination.
The reasons for using network segmentation include the following:
- Gigantic networks are broken into smaller, easier-to-manage segments.
- Network administrators can set up granular and separate policies for each subnet.
- Administrators can control, manage or restrict the flow of traffic between subnets.
- User congestion is relieved on other parts of the network.
- Cybersecurity improves in limiting how far a malicious attack can spread by confining the attack to one segment.
Network segmentation should not be confused with microsegmentation, which reduces an organization's network attack surface by applying specific security controls to limit east-west communication at the workload level. While microsegmentation has its applications, it should not be confused with regular network segmentation. There are many differences between the two, including the following:
- Traditional network segmentation covers a larger segment of the network. Microsegmentation can be used at the device level, which makes it great for internet of things (IoT) and edge devices.
- Network segmentation works with the physical network. Microsegmentation is for virtual networks.
- Network segmentation policies are broad. Microsegmentation policies are much more granular.
- Network segmentation is hardware-based. Microsegmentation is typically software-based.
- Network segmentation limits north-south traffic at the network level. Microsegmentation limits east-west traffic at the workload level.
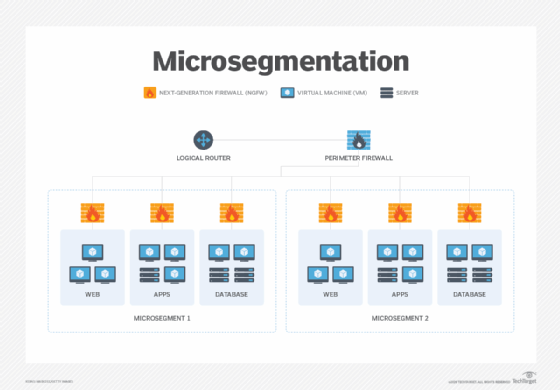
Microsegmentation enables software-based granular control of devices and virtual networks.
How does network segmentation work?
Network segmentation divides a network into multiple zones and manages each zone, or segment, individually. This means applying traffic protocols to manage what traffic passes through the segment and what is not allowed. It also covers security protocols to each zone to manage security and compliance.
Network segments are designated with their own dedicated hardware to wall each other off and only allow credentialed users to access the system. Rules are built into network configurations to determine how users, services and devices on subnetworks can interconnect with each other.
Types of network segmentation
There are two types of network segmentation: physical and virtual.
Physical segmentation uses dedicated hardware to build segments. While physical segmentation is the most secure method, it is also the most difficult to manage. Also known as perimeter-based segmentation, each segment needs its own internet connection, physical wiring and firewall. This type of segmentation operates on trust, in which anything internal is trusted and anything external is not. There are few restrictions on internal resources, which commonly operate over a flat network with minimal internal network segmentation.
Physical segmentation is also highly insecure. Once hackers or malicious actors have penetrated the firewall, they are free to move around within the network with little to nothing to stop them.
The yes/no trust of perimeter-based segmentation is no longer viable with the explosion in endpoints, all with varying levels of trust. As a result, network virtualization has become increasingly popular. It is easier to implement, as well as lock down and wall off areas from intrusion.
Virtual network segmentation covers the entire network, not just at the perimeter. Switches manage the virtual local area network environment, and firewalls are shared, reducing the required hardware. Perimeter-based segmentation is now virtualized and distributed, and security policies are much more specific and fine-grained.
What are the benefits of network segmentation?
Overall, network segmentation's major benefit is in the area of security, with manageability and performance also a consideration. Network segmentation by virtualization increases security in several ways, including the following:
- Better isolation. Network traffic can be isolated or otherwise limited, thus inhibiting lateral movement between network segments by bad players.
- Better containment. When a network issue occurs, harmful or not, its effect is limited to the local subnet in which it occurs.
- Better access control. Only approved users can access specific network resources.
- Improved monitoring. Subnets are easier to monitor, log events and detect suspicious behavior.
- Improved performance. Local traffic is reduced with fewer hosts per subnet. High-traffic networks or applications can be walled off and not impact the rest of the network.
- Reduced complexity. Rather than all the network assets sharing the same hardware and pipe, segments are overall less complex with fewer applications and less traffic.
- Easier management. Networking environments change constantly. While change is quick to implement, it can be slow to populate. Change can be regulated to just the subnetwork rather than the entire network, greatly accelerating its propagation.
Examples of network segmentation use cases
The security and performance benefits of network segmentation can be applied to multiple situations, including the following:
- Create a secure guest network. Administrators can make a space for guests with high-level security and activity monitoring.
- Dedicate user access. One segment can be created for one level of users, such as restrictions from accessing sensitive data by all except those who need it.
- Create a network for work-from-home access with additional security, such as mandatory virtual private network (VPN) use.
- Increase public cloud security. Public cloud providers require their customers to manage their own security around applications, data and system access. Network segmentation helps achieve this protection by more finely controlling who specifically has access to data.
- Isolate IoT devices into their own network. For instance, administrators can only permit devices such as security cameras to talk within their own network.
- Ensure regulatory compliance by applying secure access to sensitive data.
How to implement network segmentation
Segmenting a network is no trivial task. It requires a great deal of planning and preparation, as well as ongoing maintenance. Therefore, network teams need proper time to plan and design, starting with the following steps:
- Perform an inventory. Many companies don't have a proper inventory of their IT systems, including sensitive data and where it lives. Network administrators should ask what systems the company has and who has access to them.
- Identify who needs to use the data. This helps implement a rules-based system by granting access to only those who need it.
- Look at the what monopolizes bandwidth. One app might consume 50% of network capacity. If so, administrators should put that app on its own subnet to avoid slowing down everyone else.
- Design a segmented network. Segments can be designed after discovering which users need access to specific data and systems.
- Start with the smallest and easiest segments. Administrators can practice and learn on segments with less complexity or dependencies.
- Default deny rule. Following this basis of firewall configuration, deny access to everything that hasn't been explicitly allowed.
- Review changes frequently. Ensure that changes do not violate the segmentation configuration.
- Monitor closely. Pay attention to anything from bad-behaving apps to unusual network traffic. Administrators should review logs every day and analyze them for suspicious or unusual behavior.
This was last updated in March 2022
Continue Reading About network segmentation
- Proper network segments may prevent the next breach
- Use microsegmentation to mitigate lateral attacks
- Network design considerations for Network+ exam prep
- Why networks should apply security by design principles
- Ransomware loves network blind spots: see how to get 100% visibility
 How to subnet in cloud network environments
How to subnet in cloud network environments  By: Brien Posey
By: Brien Posey  subnet (subnetwork)
subnet (subnetwork)  By: Gavin Wright
By: Gavin Wright  Subnet use cases and considerations for network performance
Subnet use cases and considerations for network performance  How to fix the top 5 cybersecurity vulnerabilities
How to fix the top 5 cybersecurity vulnerabilities  By: Dave Shackleford
By: Dave Shackleford