networking (computer) (original) (raw)
What is networking (computer)?
Networking, also known as computer networking, is the practice of transporting and exchanging data between nodes over a shared medium in an information system. Networking comprises not only the design, construction and use of a network, but also the management, maintenance and operation of the network infrastructure, software and policies.
Computer networking enables devices and endpoints to be connected to each other on a local area network (LAN) or to a larger network, such as the internet or a private wide area network (WAN). This is an essential function for service providers, businesses and consumers worldwide to share resources, use or offer services, and communicate. Networking facilitates everything from telephone calls and text messaging to streaming video and the internet of things (IoT).
Who uses networking?
The level of skill required to operate a network directly correlates to the complexity of a given network. For example, a large enterprise may have thousands of network nodes and rigorous security requirements, such as end-to-end encryption, requiring specialized network administrators to oversee the network.
Conversely, a layperson may set up and perform basic troubleshooting for a home Wi-Fi network with a short instruction manual. Both examples constitute computer networking.
Wired vs. wireless networking
When looking at the physical layer of a computer network, there are two primary types:
- Wired networking requires the use of a physical medium for transport between nodes. Copper-based Ethernet cabling, popular due to its low cost and durability, is commonly used for digital communications in businesses and homes. Alternatively, optical fiber is used to transport data over greater distances and at faster speeds, but it has several tradeoffs, including higher costs and more fragile components.
- Wireless networking uses radio waves to transport data over the air, enabling devices to be connected to a network without any cabling. Wireless LANs (WLANs) are the most well-known and widely deployed form of wireless networking. Alternatives include microwave, satellite, cellular and Bluetooth.
Generally, wired networking offers greater speed, reliability and security compared to wireless networks; wireless networking provides more flexibility, mobility and scalability.
Types of computer networks
Networks can also be classified according to how they're designed and built, encompassing approaches that include software-defined networking (SDN) and overlay networks. Networking can also be categorized by environment and scale, such as LANs, campus, WANs, data center networks and storage area networks (SANs). These include the following:
- LANs. LANs are used in business, government and home environments to interconnect devices within a specific domain, such as an office building.
- WANs. WANs connect multiple LANs and link large geographic areas, such as a headquarters location and branch offices across multiple cities, states or countries.
- Metropolitan area networks. MANsare similar to WANs, with the key difference being that they encompass one metropolitan area. Such networks can be used to connect multiple buildings of a large company, such as a bank, within a city. Multiple organizations can share high-bandwidth MANs for intracity communications. MANs can connect to WANs and the internet.
- Campus area networks. CANs are the next size down from MANs. Government buildings, large enterprises and universities that have multiple buildings within a defined geographic area may have a campus environment. Linking these buildings and the network infrastructures they contain can be achieved using a CAN.
- SANs. SANs support connections from multiple servers to multiple storage devices. They're generally secure and can support disaster recovery.
- WLANs. Most commonly implemented as Wi-Fi, WLANs form LANs using radio technology.
- Virtual LANs. VLANsare used to create logically segmented networks within the same physical network, a concept known as an overlay. This enables network administrators to separate different types of traffic along the same physical infrastructure.
- Cloud networks. This term can refer to the network infrastructure and software that connects to public, private or hybrid cloud services. It can also refer to networking resources that are hosted in the cloud.
- Carrier networks. Large telecommunications companies operate these large networks, which are among the largest in the world. They are enormously complex, are highly redundant and have extremely high bandwidth.
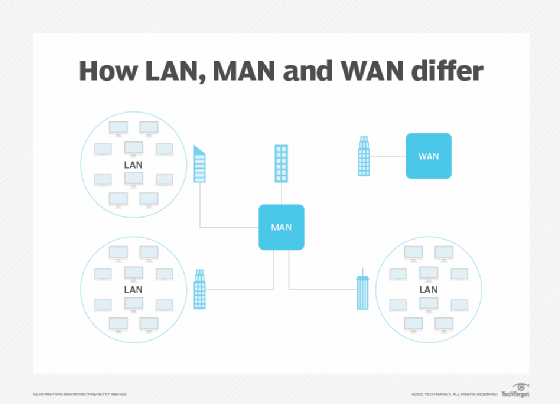
Network types vary in terms of scale and the environments they serve.
Network topologies
The physical and logical way a network is configured is called its topology. The physical deployment may look the same for each topology, but the internal workings of the network -- its logical structure -- differentiate one network architecture from another. Network diagrams typically are used to depict different topologies, with nodes depicted as dots and network links shown as lines.
The following are six main types of network topologies:
- Star network. Each node in a star network is connected to a central hub, typically a computer or server, but not directly to other nodes. It's also referred to as a hub-and-spoke topology.
- Ring network. Each node has two connection points for linking to other devices; in practice, such as when using a token ring network, each device has a single physical network connection.
- Mesh network. Each node in a mesh network connects to every other node; this is often a costly arrangement considering the number of links required.
- Point-to-point network. This topology describes dedicated connections between two nodes. It's most often used in wireless communications that require line of sight, such as microwave antennas. It may also be used for dedicated fiber connections between two sites.
- Bus network. Each device in a bus network connects to a single cable called a bus. When data packets traverse the bus, they look for the "station" containing the correct destination address. This topology is easy to set up and works well on small networks, but it quickly runs into scalability and performance challenges on larger networks.
- Tree network. Connecting multiple star networks to a shared bus creates a tree topology.

Network topologies map where nodes, such as switches and routers, are placed on a network and how they're interconnected.
Components of networking
At a high level, computer networking requires a physical network infrastructure that includes components such as switches, routers and wireless access points. In addition, networks have underlying firmware that operates such equipment. Other components include the software to monitor, manage and secure the network. These network components are present in wired and wireless networks.
Network devices
Various components connect computing devices to a network medium, whether wired or wireless. On one side of this connection is data terminal equipment (DTE), such as computers and telephones. These devices connect to data communications equipment (DCE), such as modems, routers, switches and gateways. Network protocols and standards govern the mechanisms by which DTE connect to DCE, as well as communications among different types of DCE. Once connected to the network, DTE and DCE are assigned unique IP addresses.
Links
The wired or wireless network medium that connects devices in a network is called a link. Today's wired networks can use copper twisted-pair, fiber optic or coaxial cables. Wireless links use different protocols for sending data and voice via Wi-Fi, cellular, satellite and microwave technologies. Links can have physical and logical attributes that correspond to a specific topology describing how they connect to each other.
Communication protocols
Specifications that define how network devices connect to each other are called protocols. Protocols are used in wired and wireless networks. For instance, voice over IP transports IP telephony traffic to any endpoint that supports the protocol. Hypertext Transfer Protocol provides a common way for browsers to display webpages. The IP suite, also known as Transmission Control Protocol/Internet Protocol (TCP/IP), is a family of protocols responsible for transporting data and services over an IP-based network. The TCP/IP model is divided into four protocol categories, also known as layers, according to the aspect of network communications they facilitate:
- Physical layer. Sometimes referred to as the network interface layer, this layer specifies how devices connect to a network and how bits are transmitted over the physical media being used. Some models of TCP/IP have a fifth network access layer.
- Internet layer. These protocols govern data transfers -- how data moves from the point of origin to the point of termination. Data is put in packets with addressing and routing instructions embedded in each packet. The internet layer determines the most appropriate route through a network for the packet to reach its destination. Among the protocols in this layer are IP, Address Resolution Protocol and Internet Control Message Protocol.
- Transport layer. Packet switching typically breaks data streams into discrete packets that contain routing instructions via an IP address. Each time a packet queues up for transmission, its path is likely to be different from other packets based on network traffic and other criteria. The disassembled packets are subsequently reassembled at the destination in the correct sequence via the transport layer. This layer also ensures error-free delivery of packets and can retransmit packets that are lost or dropped. Transport layer protocols include TCP and User Datagram Protocol.
- Application layer. This layer specifies how applications connect to the network and can transmit and receive data packets. It also includes security protocols, such as Transport Layer Security.
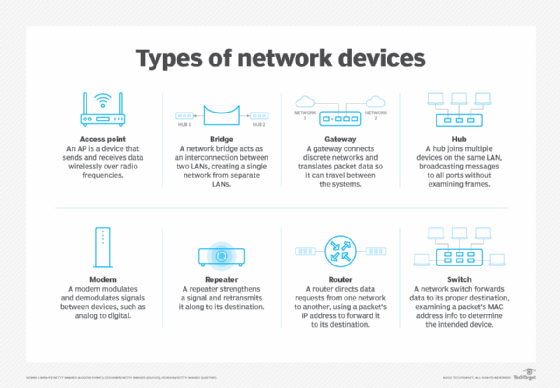
Networks are made up of a range of different components and devices.
Advantages of computer networks
Computer networks are ubiquitous today. Businesses, governments, individuals and communities depend on networking for various benefits:
- Convenience and flexibility. Networks make it faster and easier to access all kinds of information and resources. With internet-connected devices in nearly every pocket, a person can coordinate transportation, conduct financial transactions, participate in meetings and perform an almost infinite number of digital activities from almost anywhere.
- Resource sharing. Network technology links people with all kinds of information, devices and resources, making it easy to share them. Access to servers, printers, copiers and scanners helps businesses of all types and sizes use technology in efficient and cost-effective ways. Otherwise, each user would need their own copy of each resource.
- Innovation. The ability to interconnect devices and share data among them creates the opportunity for new ways of doing business, operating communities, communicating with others, automating tasks and more. Notably, networks are a fundamental requirement for IoT, which encompasses a broad range of innovative applications centered on the ability for endpoints to share and receive data over a network.
- Data storage. Networks play a key role in data storage. Getting data from the point of creation to a storage location depends on networking. Whether stored locally or hosted remotely in a cloud service, networks transport data to a storage device. Without a network, people would need to physically transport data from one device to another.
- Entertainment. Networks make access to an enormous selection of entertainment sources, such as games, music and video, possible. The internet enables people around the world to participate in multiplayer games, for example.
Risks to computer networks
Data networks come with their own set of risks that users must be aware of. They include the following:
- S ecurity threats. Networks are an attractive target for hackers and other malicious actors who wish to cause disruptions, divert resources, steal data or access sensitive information. Ransomware and phishing are among the most prevalent threats. Encryption, access control, firewalls and antivirus software are all used to counter security threats.
- Outages. While service-level agreements provide some measure of protection against disruption, the reality is that network service providers can and do experience unplanned outages. For a business, the loss of internet or WAN connectivity can bring all operations to a halt.
- Misconfigurations. Network devices must be configured for proper operation -- a process that's susceptible to human error. For example, if an incorrect command is issued, a device might not transmit data as needed.
- Equipment failure. Like any other type of equipment, network devices can experience hardware- or software-related failures, with or without warning. To avoid machine failures, network administrators must maintain an up-to-date inventory of backup devices.
- Power loss. Communications systems need power to operate, so loss of power without a suitable backup can disrupt business operations.
- Infrastructure damage. Network integrity depends on the continuous availability of the supporting infrastructure. This can include underground cables, aerial cables on poles, carrier switching center buildings, wireless transmission towers and buildings, and electric utilities. This infrastructure is susceptible to tornadoes, earthquakes, floods, electrical storms, solar flares, physical and cybersecurity breaches, vandalism and terrorism.
The future of networking
Wired and wireless networking will continue to coexist in the coming years. Speeds are likely to increase as demands for greater speed and bandwidth continue. Advances in network technology have raised the bar on performance and reduced latency.
SDN, software-defined WAN and network virtualization have reshaped networking. It's likely that they will continue to introduce more flexibility and less reliance on proprietary hardware.
Artificial intelligence, machine learning and automation have the potential to dramatically influence network performance and management as well. Given the ever-growing threat of network attacks, AI will likely play an increasingly important role in network security.
Networks entail a confusing array of wires, switches and other hardware devices. Learn some best practices for handling network components from a networking expert.
This was last updated in April 2024
Continue Reading About networking (computer)
- How to ensure optimal network workload placement
- Cloud security vs. network security: What's the difference?
- What are the features and benefits of 5G technology?
- Key SD-WAN trends to watch
- Introduction to network hardware components
 Logical vs. physical topology: What's the difference?
Logical vs. physical topology: What's the difference?  By: Verlaine Muhungu
By: Verlaine Muhungu  Common types of networking devices explained
Common types of networking devices explained  By: Jennifer English
By: Jennifer English  Link Layer Discovery Protocol (LLDP)
Link Layer Discovery Protocol (LLDP)  By: Rahul Awati
By: Rahul Awati  local area network (LAN)
local area network (LAN)  By: Kinza Yasar
By: Kinza Yasar