elliptical curve cryptography (ECC) (original) (raw)
Elliptical curve cryptography (ECC) is a public key encryption technique based on elliptic curve theory that can be used to create faster, smaller and more efficient cryptographic keys.
ECC is an alternative to the Rivest-Shamir-Adleman (RSA) cryptographic algorithm and is most often used for digital signatures in cryptocurrencies, such as Bitcoin and Ethereum, as well as one-way encryption of emails, data and software.
An elliptic curve is not an ellipse_,_ or oval shape, but it is represented as a looping line intersecting two axes, which are lines on a graph used to indicate the position of a point. The curve is completely symmetric, or mirrored, along the x-axis of the graph.
Public key cryptography systems, like ECC, use a mathematical process to merge two distinct keys and then use the output to encrypt and decrypt data. One is a public key that is known to anyone, and the other is a private key that is only known by the sender and receiver of the data.
ECC generates keys through the properties of an elliptic curve equation instead of the traditional method of generation as the product of large prime numbers. From a cryptographic perspective, the points along the graph can be formulated using the following equation:
y²=x³ + ax + b
ECC is like most other public key encryption methods, such as the RSA algorithm and Diffie-Hellman. Each of these cryptography mechanisms uses the concept of a one-way, or trapdoor, function. This means that a mathematical equation with a public and private key can be used to easily get from point A to point B. But, without knowing the private key and depending on the key size used, getting from B to A is difficult, if not impossible, to achieve.
ECC is based on the properties of a set of values for which operations can be performed on any two members of the group to produce a third member, which is derived from points where the line intersects the axes as shown with the green line and three blue dots in the below diagram labeled A, B and C. Multiplying a point on the curve by a number produces another point on the curve (C). Taking point C and bringing it to the mirrored point on the opposite side of the x-axis produces point D. From here, a line is drawn back to our original point A, creating an intersection at point E. This process can be completed n number of times within a defined max value. The n is the private key value, which indicates how many times the equation should be run, ending on the final value that is used to encrypt and decrypt data. The maximum defined value of the equation relates to the key size used.
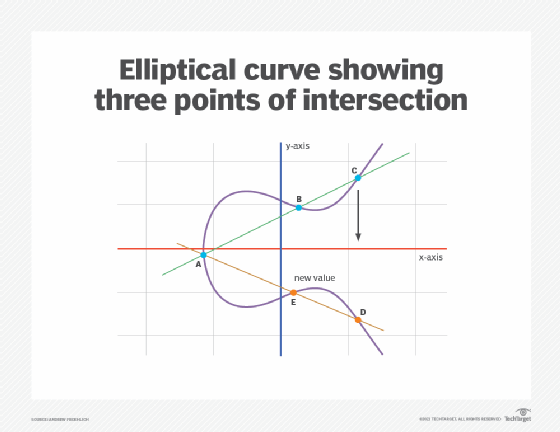
This elliptical curve diagram shows three intersection points.
Comparing RSA vs. elliptical curve cryptography
ECC can yield a level of security that requires fewer computing resources to encrypt and decrypt data compared to alternative methods, like RSA. For example, ECC using a 256-bit key would require a 3,072-bit RSA key to achieve equivalent protection. Because ECC establishes equivalent security with lower computing power and battery resource usage than RSA, it is widely used for mobile applications and internet of things (IoT) devices with limited central processing unit (CPU) resources.
ECC offers several benefits compared to RSA:
- It operates on devices with low CPU and memory resources.
- It encrypts and decrypts faster.
- Larger key sizes can be used without significantly increasing the key size or CPU and memory requirements.
How secure is elliptical curve cryptography?
ECC is thought to be highly secure if the key size used is large enough. The U.S. government requires the use of ECC with a key size of either 256 or 384 bits for internal communications, depending on the sensitivity level of the information being transmitted.
But ECC is not necessarily any more or less secure compared to alternatives such as RSA. The primary benefit of ECC is the inherent efficiencies gained when encrypting and decrypting data.
The history of elliptical curve cryptography
The properties and functions of elliptic curves in mathematics have been studied for more than 150 years. Their use within cryptography was first proposed in 1985, separately by Neal Koblitz from the University of Washington and Victor Miller at IBM.
ECC was first developed by Certicom, a mobile e-business security provider, and was then licensed by Hifn, a manufacturer of integrated circuitry and network security products. Vendors, including 3Com, Cylink Corp., Motorola, Pitney Bowes, Siemens, TRW Inc. (acquired by Northrop Grumman) and Verifone, supported ECC in their products.
The use of ECC in public and private sectors has increased over the past few years. While RSA continues to be more widely used and is easier to understand compared to ECC, the efficiency benefits of ECC make it appealing for many enterprise use cases. These include speeding up secure access to Secure Sockets Layer-encrypted websites and streaming encrypted data from IoT devices with limited computing power.
Data encryption is a must-have for cloud environments, but organizations face many challenges as they try to secure their data. Learn what cloud encryption strategies organizations can implement to overcome these limitations.
This was last updated in January 2022
Continue Reading About elliptical curve cryptography (ECC)
- EncroChat hearings delayed as lawyers seek disclosure on police hacking
- Crypto-agility: Strategies and best practices to get there
- Learn the basics of cryptography in IoT
- Mobile app security beset practices for 4 vulnerability types
- An introductory guide to mobile app security testing
 Deep dive into quantum-resistant cryptography for email security
Deep dive into quantum-resistant cryptography for email security  By: Isla Sibanda
By: Isla Sibanda  An overview of storage encryption for enterprises
An overview of storage encryption for enterprises  By: Julia Borgini
By: Julia Borgini  asymmetric cryptography By: Kate Brush
asymmetric cryptography By: Kate Brush  Explore the impact of quantum computing on cryptography
Explore the impact of quantum computing on cryptography  By: Ryan Arel
By: Ryan Arel