email virus (original) (raw)
What is an email virus?
An email virus consists of malicious code distributed in email messages to infect one or more devices. This malicious code can be activated in numerous ways: when the email recipient clicks on an infected link within the message, opens an infected attachment or interacts with the message in some other way.
Email viruses often spread by causing the malicious message to be sent to everyone in the original victim's address book.
Simply put, an email virus is a malicious code or a link to malicious code sent via email. The virus has the ability to replicate itself so it can quickly spread from one device to another. Thus, an email virus can not only infect the victim's computer, but it can also infect the computers of everyone in the victim's address book or those sharing the same network.
There are three primary ways an email virus can infect a victim's email and computer:
- via a phishing email
- included in an attachment
- embedded within the email body
Email viruses often look like executable files with extensions such as the following:
- .exe
- .dll
- .com
- .bat
- .cmd
- .pif
- .scr
- .dot
- .xls
- .xlt
- .docm
Email can serve as a delivery mechanism for all types of malware.
How to recognize an email virus
The various types of email viruses present themselves differently, so it's not always possible to recognize when an email message contains a virus.
Some infected emails have subject lines that don't make sense -- e.g., they contain gibberish text or strange special characters -- making them easy to spot. The other header fields and body content of the email may also look peculiar in some way. In other cases, the sender may be unknown to the user, which may raise the user's suspicion.
But other email messages containing viruses can be more difficult for recipients to identify. In such cases, the malicious actor may disguise the message so it appears to originate from a trusted and/or known sender. This is particularly true of email phishing campaigns carried out to further business email compromise attacks.
What can an email virus do?
An email virus can wreak all kinds of havoc:
- distribute and execute ransomware attacks;
- enlist the victim's system into a botnet;
- crash the victim's system;
- provide a threat actor with remote access to the victim's device;
- steal the victim's personal data or destroy their files;
- create unwanted pop-ups; or
- add the victim system to a malvertisement.
Email viruses are especially dangerous since they can gather information about the victim -- and their contacts -- without their knowledge. Using such a covert means of attack, an email virus can end up causing massive damage in a short period of time. By the time the victims realize that there is a problem, it's often too late to contain the damage.
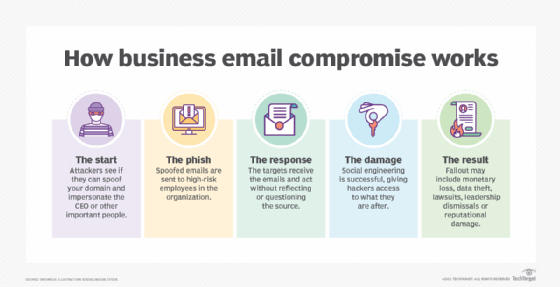
How business email compromise works and can lead to fraud
Email virus and phishing
Email viruses are often connected with phishing attacks, in which hackers send out malicious messages that look as if they are originated from legitimate, known or trusted sources, such as the following:
- the victim's bank;
- social media;
- internet search sites;
- friends, relatives or co-workers; or
- someone high up in their company, e.g., chief executive officer.
The attacker's goal is to trick the victim into revealing personal and potentially valuable information, such as their address, passwords, credit card number, Social Security number, etc.
Social engineering methods, like spam and malware-filled email messages, are commonly used by threat actors to infect user devices with email viruses and to attack their organization's network.
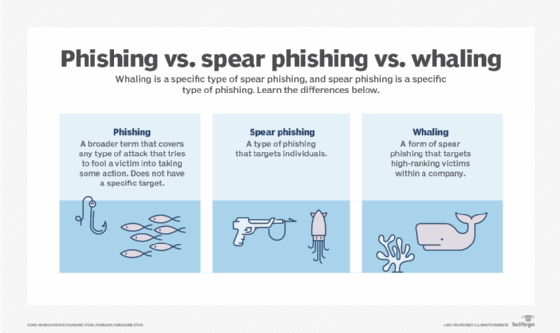
Compromised email can lead to phishing, spear phishing and whaling scams that compromise business data and the bottom line.
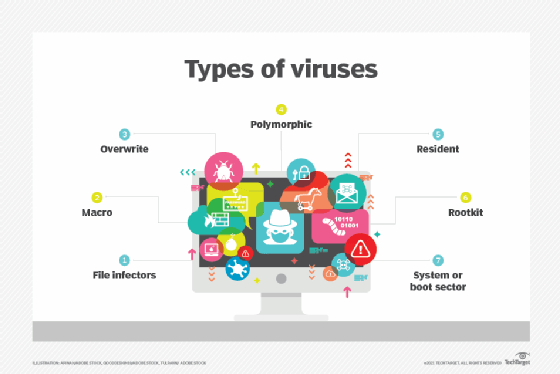
Types of email viruses
Email viruses can take many different forms:
- Email spam. Email spam, also known as unwanted or unsolicited email, usually spreads malware through links in the message. These links, when clicked, often take the victim to a phishing website that steals their data or to other sites hosting malware that further infects their device.
- Boot sector virus. This virus targets the device's master boot record. It can be hard to remove and often requires a full system format, making it one of the most dangerous and persistent types of email viruses.
- Multipartite virus. This virus can simultaneously attack the victim computer's executable files and boot sector. It can also wipe out the hard drive or solid-state storage device. As the virus spreads, it takes up memory, and the user gets multiple pop-up messages advising about low virtual memory. This is a sign the computer is infected with a multipartite virus.
- Resident virus. A resident virus immediately installs itself on the victim's computer as soon as they click on an infected email. Even if the primary virus source is removed, the virus persists in the system and is, therefore, difficult to resolve.
- Virus hoax. Virus hoax messages contain a false warning about a nonexistent threat and often instruct the recipient to take some action, such as forwarding the warning to all their contacts. These messages are a type of socially engineered email virus. One variant builds on the tech support phone scam, in which a malicious actor calls a victim and offers to "help" them with a problem that they purportedly discovered on the victim's computer.
- Macro virus. A macro virus is written in a macro language used by other software programs, especially Microsoft Excel and Microsoft Word. It is transmitted through a phishing email message containing a malicious attachment. As users share the infected documents with others, often by forwarding the email, the virus spreads and infects additional devices.
- Spambot. Spambot programs harvest email addresses to build mailing lists for sending spam. Although they're not usually distributed through email, they are instrumental in gathering valid email addresses that are then used to distribute email viruses.

How macro viruses work
Examples of well-known email viruses
This rogues' gallery of email viruses were particularly destructive:
- Melissa. Released in 1999, Melissa is one of the oldest email viruses. This fast-spreading macro virus was distributed as an email attachment, which, when opened, disabled many safeguards in Word 97 and Word 2000. Melissa also resent the virus to the first 50 people in each of its victims' address books.
- ILOVEYOU. In May 2000, the fast-spreading ILOVEYOU virus shut down email services in several major enterprises, including Microsoft and Ford Motor Company. In about 10 days, ILOVEYOU affected about 45 million users and caused about $10 billion in damages.
- Mydoom. In early 2004, MyDoom sent spammy junk mail through infected computers and hit several tech companies, including Microsoft and Google, with a distributed denial-of-service attack. It infected 16% to 25% of email messages in 2004.
- Storm Worm Trojan horse. This Trojan horse malware spread through infected attachments in email messages that exploited users' concerns about European storms.
- CryptoLocker ransomware. CryptoLocker, which spread via phishing emails and malicious attachments, encrypted victims' files. The hackers then demanded a ransom from the victims to unlock the files.
How to detect email virus infections
Email viruses have evolved and become more dangerous over time. To combat them, detection methods have evolved as well:
- Signature-based detection. When a new virus variant is discovered, its signature is added to the signature database of the antivirus software. This approach is still in use today. However, it has some limitations that enable threat actors to create advanced viruses that can avoid matching with existing signatures.
- Heuristics. Heuristic analysis involves examining code for suspicious properties to detect previously unknown viruses and new variants of existing viruses.
- Real-time protection. Antivirus and antimalware programs constantly monitor systems for suspicious activity to protect the systems in real time.
- Sandbox detection. This behavior-based detection technique runs programs in a virtual environment and logs their actions to determine if a program is malicious.

How to prevent email virus infections
Email is an indispensable part of the modern worker's life. While it's not possible to stop using email to avoid email viruses, it is possible to take steps to avoid becoming a victim of such attacks.
The most important preventive tool is antivirus software. A trusted antivirus app that's updated with the latest virus definitions can go a long way toward thwarting email viruses.
Antivirus software is a key tool for preventing email viruses from causing damage.
Other ways to prevent an email virus from infecting a device or network include the following:
- Scan all email attachments for malware.
- Be careful about opening attachments from unknown sources.
- Avoid opening executable files included as attachments.
- Regularly update and patch mail clients, web browsers and operating systems.
- Never click on links in the body of email messages.
- Double-check the sender's name to confirm that an email is from a legitimate source.
- Watch for other signs that may indicate phishing emails, such as obvious grammatical errors, suspicious attachments, strange domain names, etc.
This was last updated in September 2021
Continue Reading About email virus
- Explore 5 business email compromise examples to learn from
- Games, not shame: Why security awareness training needs a makeover
- How to send secure email attachments
- How to choose the right email security service for your organization
- Detecting and Combating Malicious Email
 What is malware? Prevention, detection and how attacks work
What is malware? Prevention, detection and how attacks work  By: Kinza Yasar
By: Kinza Yasar  12 common types of malware attacks and how to prevent them
12 common types of malware attacks and how to prevent them  By: Sharon Shea
By: Sharon Shea  virus (computer virus)
virus (computer virus)  By: Robert Sheldon
By: Robert Sheldon