SSL certificate best practices for 2020 and beyond (original) (raw)
SSL/TLS security is continuously improving, and there are steps site owners should take to ensure the safety of their SSL certificates, websites and users. Read on to learn more.
SSL and its successor, TLS, are encryption-based internet security protocols that provide privacy, authentication and data integrity for internet communications, protecting users against eavesdroppers, man-in-the-middle attacks and hijackers who attempt to spoof trusted websites.
However, the state of SSL certificate security has come under scrutiny yet again -- from flaws in the protocols to attackers redirecting network traffic during requests to certificate authorities' inabilities to properly validate domain ownership.
Although SSL/TLS certificate security is continually improving, site owners and users need to be constantly made aware that certificates don't guarantee the trustworthiness of a site. There are, however, a number of steps enterprises can take to boost the security of their certificates and websites.
Here, learn about the state of SSL certificate security, the vulnerabilities they face and SSL certificate management best practices to keeping them secure.
Inside SSL certificate security
More than 80% of today's internet traffic is encrypted. SSL Pulse provides a dashboard view of the quality of SSL/TLS support across 150,000 SSL- and TLS-enabled websites, based on Amazon Alexa's list of the world's most popular sites. It provides an in-depth view of how well user connections to the busiest sites are protected.
Nearly 100% of the sites listed are no longer vulnerable to attacks such as BEAST, DROWN and ROBOT, which take advantage of weaknesses in various protocols related to SSL functions. While the statistic is good, it drops below 95% for vulnerabilities including Zombie POODLE, GOLDENDOODLE, Sleeping POODLE and 0-length padding oracle attacks. Given that SSL Pulse's statistics are for the top -- and presumably best managed -- sites in the world, the overall percentage of vulnerable websites is likely a lot higher when looking at the wider internet space.
Check versions and algorithms
What's to blame for the current state of SSL certificate security? Badly configured servers are the main reason many sites are vulnerable. Organizations should routinely review their servers' settings and scan their SSL certificates to ensure they are correctly installed and using the recommended protocols and algorithms, particularly on internet-facing services.
Services, including GlobalSign and Qualys CertView, scan internet-facing certificates and report how secure they are, offering recommendations on how to improve their security grade. Many certificate configuration grades can be easily improved by disabling SSL and TLS 1.0 on the server, as well as any cryptographic algorithms with known vulnerabilities. Supporting old versions of SSL and TLS leaves sites and their users vulnerable to downgrade attacks, which involve hackers forcing connections to a server using older protocol versions that have known exploits.
SSL certificates are not a set-it-and-forget-it security control.
Major browsers are officially removing support for TLS versions 1.0 and 1.1. While versions 1.1 and 1.2 have no known vulnerabilities, TLS 1.3 should be the protocol of choice to ensure sites are using only the strongest algorithms and ciphers. TLS 1.3 removed many of the problematic options in previous TLS versions and only includes support for algorithms with no known vulnerabilities.
Check expiration dates
SSL certificates are not a set-it-and-forget-it security control. They have expiration dates and can be revoked, so SSL certificate management best practices must be in place to track certificates and keep security teams up to date on new developments, both good and bad.
Certificate authority Let's Encrypt recently had to invalidate more than 3 million TLS certificates due to a bug in how it validated domain ownership. Domain validation is a process certificate authorities use to ensure a certificate applicant controls the domain it wants a certificate for. Site owners that are affected by this revocation of certificates -- you can check the status of your Let's Encrypt certificates here -- and that don't request a new certificate will find their revoked certificate is triggering browser and application errors, leading to failed connections that affect availability -- and, potentially, user confidence and brand reputation.
Also, as of Sept. 1, 2020, Apple's Safari browser will no longer trust certificates with validity periods longer than 398 days, and other browsers are likely to follow suit. Reducing validity periods reduces the time period in which compromised or bogus certificates can be exploited. As such, any certificates using retired encryption algorithms or protocols will need to be replaced sooner.
Regular scanning of certificates using tools such as NetScanTools' SSL Certificate Scanner or XenArmor Network SSL Certificate Scanner can prevent problems by flagging expired, soon-to-be-expiring or revoked certificates.
Let's Encrypt is further improving the domain validation process to prevent attackers from hijacking or redirecting network traffic during the challenge request, or associated DNS queries, and tricking a certificate authority into incorrectly issuing a certificate. A Princeton University research team demonstrated this type of attack can succeed by using insecure deployment of the Border Gateway Protocol. To prevent this, Let's Encrypt now validates domains from multiple perspectives, as well as from its own data centers, meaning an attacker would need to successfully compromise three different network paths at the same time.
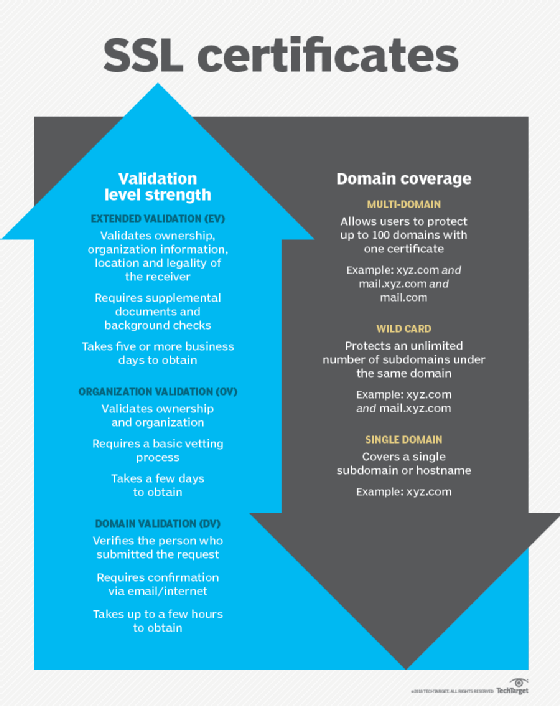
Extended validation certificates
Another way organizations can prove ownership of a domain is by purchasing an Extended Validation (EV) SSL certificate. These have stricter requirements for authentication than standard domain certificates. However, web browser companies differ on how effective EV certificate indicators are in protecting users from malicious sites. For example, Microsoft Edge displays EV certificates with a green lock and the company name in the address bar, but Google and Mozilla no longer do, citing research that showed these indicators "do not protect users as intended."
Of particular concern is the fact that an increasing number of phishing attacks use authentic SSL certificates to give their malicious websites an appearance of legitimacy. There are no safeguards to prevent a malicious IP address from obtaining an authentic SSL certificate. Because EV certificates require stricter authentication, fewer users would get tricked by such a phishing scam.
 What is a SSL (secure sockets layer)? By: TechTarget Contributor
What is a SSL (secure sockets layer)? By: TechTarget Contributor  Secure Sockets Layer certificate (SSL certificate)
Secure Sockets Layer certificate (SSL certificate)  By: Rahul Awati
By: Rahul Awati  3 types of PKI certificates and their use cases
3 types of PKI certificates and their use cases  By: Isabella Harford
By: Isabella Harford  certificate authority (CA)
certificate authority (CA)