How to use a jump server to link security zones (original) (raw)
Jump servers are a perfect example of less is more. By using these slimmed-down boxes, administrators can connect to multiple resources securely.
Jump servers, also known as jump boxes, are a popular way to secure administrative paths across systems in different security zones. Jump servers link one or more network segments, allowing administrative access between the zones.
For example, an administrator's workstation probably resides in a secured, internal virtual LAN (VLAN). That administrator might be responsible for configuring web, email or name resolution servers located in a relatively untrusted DMZ. With a jump server, the administrator can connect to these systems securely.
Jump servers are hardened, monitored and don't store any valuable information. They could be SSH tunneling endpoints or Remote Desktop Protocol (RDP) targets.
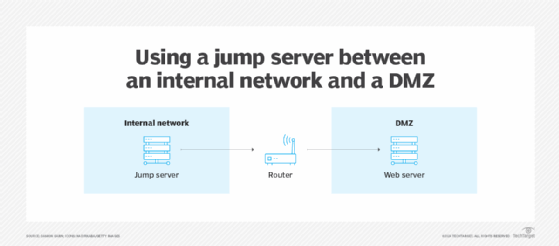
Figure 1: Internal network subnet and DMZ configured as security zones.
Common examples of jump servers
Let's examine how an admin's Linux workstation connects to a DMZ system. First, the workstation establishes an SSH connection to the jump server. That connection is authenticated and encrypted, even though it traverses the supposedly trusted internal network. From the jump server, the connection uses SSH forwarding to establish a secure connection to the target server in the DMZ.
These SSH connections require authentication -- usually key-based. Authentication requires the administrator to prove their identity, after which access to resources -- in this case the DMZ target system -- is granted.
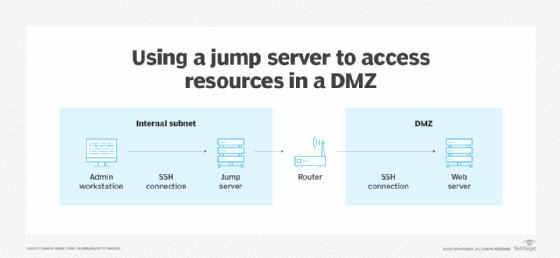
Figure 2: The administrator's workstation uses the jump server to get access to resources in the DMZ.
Jump servers can also centralize and control access to cloud resources. It's easier to control and monitor cloud connections that pass through a single point to access cloud-based systems. This example isn't different from on-premises systems, but the cloud's scalability can add challenges. Regardless, cloud service providers offer various ways of implementing jump servers to access resources.
Jump server technologies
Jump servers run a common OS. Let's take an organization standardized on Linux or Windows, or a combination. Its jump servers would have a minimal OS installation, most likely Linux. As such, the server would not have a GUI, run only the SSH and firewall services, and restrict access via the host-based firewall. All administration of the target systems occurs through the jump server.
Remember, jump servers should never store any sensitive data. They are not a place for user files, configuration file backups or databases. Their sole role is to connect two or more network segments.
Two primary technologies establish a network connection to and from jump servers: SSH and RDP.
SSH is a standard remote connectivity protocol in the Linux/Unix world. It's also commonly found with network devices, such as smart switches and routers. It's less common with Windows systems, though various SSH client and server options are available for the platform, for example, PuTTY is one Windows SSH client. Microsoft PowerShell also supports SSH.
Figure 3: Establishing an SSH connection to a remote host
RDP is a common Windows protocol. It provides a GUI to remote systems, enabling administrators to work with devices as if they were right in front of them. RDP encrypts administrator connections by default.

Figure 4: RDP login box
Options such as virtual network computing might also be appropriate to create a network connection, but be careful to properly lock down the software.
Firewall configurations for SSH and RDP are standard. SSH uses TCP port 22 and RDP relies on TCP port 3389.
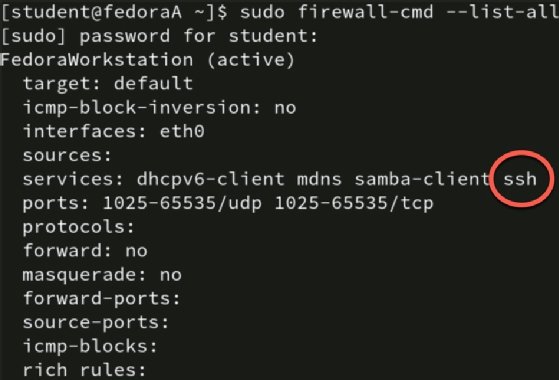
Display of current firewall rules. Note, SSH is allowed.
Jump server hardening checklist
Configuring a jump server is a great example of the "less is more" concept. It begins with secure installation and only installing the minimum features and services. Do not add more applications than required and use application control policies to permit only authorized applications to run.
Following are common hardening steps for jump servers:
- Minimal OS installation.
- Minimal application installation and enable application controls.
- Minimal services running.
- Strict firewall configuration.
- Strict access control to the jump server.
- Configure MFA.
- Only allow administrators to connect to the jump server from authorized workstations.
- No end-user data.
- No internet connectivity.
- Use only air-gapped methods for patching.
- Enable strict monitoring and logging policies with frequent auditing.
Linux systems usually rely on rsyslog for logging. It maintains detailed logs, offers log forwarding and provides alerts. Event Viewer is the standard Windows log file mechanism. It supports detailed and centralized logging and alerts. Regardless of the platform, audit jump server logs regularly for any anomalies.
Pros and cons of jump servers
Despite their benefits, jump servers also have a few challenges to consider.
Pros
- Basic OS and service configurations.
- No internet connectivity, which makes it difficult for attackers to add malware.
- No sensitive data stored on the system.
- Detailed monitoring, logging and auditing of the system.
Cons
- Exposing just one user's connections could open all connections.
- Could be difficult to harden and patch.
- Only provides front-end security; other network layers must be secured.
How to make jump servers work for you
Many organizations separate business resources into specific zones, with internal employee systems existing on VLANs separate from database servers, which are separate from internet-facing resources. These segments are essential parts of managing network security and traffic.
Jump servers are vital tools for administrators in heavily segmented and secured networks, providing a control point between segments. The fact that jump servers don't store data and run only minimal services means they are less prone to misconfiguration or vulnerabilities. The typical connection is SSH or RDP, though other options exist. The principles are the same whether accessing on-premises or cloud resources.
It's important to regularly review your network topology and identify security zones. Consider where cross-zone administration occurs and determine how jump servers can increase the security and management of your systems.
Damon Garn owns Cogspinner Coaction and provides freelance IT writing and editing services. He has written multiple CompTIA study guides including the Linux+, Cloud Essentials+ and Server+ guides, and contributes extensively to TechTarget Editorial and CompTIA Blogs.
 What is remote desktop protocol (RDP)?
What is remote desktop protocol (RDP)?  By: Kinza Yasar
By: Kinza Yasar  What is a headless server?
What is a headless server?  By: Gavin Wright
By: Gavin Wright  How to deploy and configure xrdp on Linux
How to deploy and configure xrdp on Linux  By: Damon Garn
By: Damon Garn  Top 3 ransomware attack vectors and how to avoid them
Top 3 ransomware attack vectors and how to avoid them  By: Diana Kelley
By: Diana Kelley