cloud security (original) (raw)
By
- Kinza Yasar,
- Andrew Froehlich, West Gate Networks
- Sharon Shea, Executive Editor
What is cloud security?
Cloud security, also known as cloud computing security, is a set of policies, practices and controls deployed to protect cloud-based data, applications and infrastructure from cyberattacks and cyberthreats.
Cybersecurity, of which cloud security is a subset, has the same goals. Where cloud security differs from traditional cybersecurity is in the fact that administrators must secure assets that reside within a third-party service provider's infrastructure.
Why cloud security is important
As enterprise cloud adoption grows, business-critical applications and data migrate to trusted third-party cloud service providers (CSPs). Because no organization or CSP can eliminate all security threats and vulnerabilities, business leaders must balance the benefits of adopting cloud services with the level of data security risk their organizations are willing to take.
The following reasons highlight the importance of cloud security:
- Business continuity. Putting the right cloud security mechanisms and policies in place is critical to prevent breaches and data loss, avoid noncompliance and fines and maintain business continuity (BC).
- Centralized security. A major benefit of the cloud is that it centralizes applications and data and centralizes the security of those applications and data as well. Eliminating the need for dedicated hardware also reduces organizations' cost and management needs, while increasing reliability, scalability and flexibility.
- Disaster recovery. Cloud security systems help prevent potential losses caused by natural disasters by providing data redundancy and backup services. Cloud environments typically include automated backup processes, where data is regularly backed up according to predefined schedules. These backups can consist of everything from individual files to entire server instances or databases that enable organizations to easily back up and recover important data in the event of a disaster at their office locations.
- Data protection. Businesses store confidential information, such as customer financial details, intellectual property and sales records on the cloud. If this information is leaked, it can cause irreparable damage. Therefore, stringent cloud security measures are essential for protecting sensitive data from unauthorized access and potential leaks. Most cloud security providers invest in advanced technologies, such as artificial intelligence (AI) and security analytics, to automatically scan for suspicious activities.
- Enhanced business outcomes. Cloud security enables better business outcomes by managing and mitigating cloud security risks. Businesses transitioning to the cloud must prioritize cloud security from the start so that it's easier for them to bounce back if anything goes wrong.
- Cost savings. When it comes to cloud security, many businesses outsource security to CSPs. This enables businesses to save on the costs of maintaining their own security infrastructure.
- Cloud data compliance. Ensuring compliance is a key component of robust cloud data security systems, which entails understanding data storage, access, processing and protection requirements. To lower the chance of breaches and meet data compliance, cloud data loss prevention (DLP) techniques are used by many organizations.
- Data encryption. Most CSPs utilize advanced encryption techniques to offer comprehensive options for secure data transfer, storage and sharing. Additionally, they ensure data protection both during transit and while at rest.
How cloud security works
Cloud computing operates in three main environments:
- Public cloud services. Public clouds are owned and hosted by third-party CSPs. These include software as a service, platform as a service (PaaS) and infrastructure as a service (IaaS). Public cloud services including cloud security services are available to anyone who wants to use or purchase them. Typically, cloud security in the public cloud focuses on protecting data from distributed denial-of-service attacks (DDoS), malware, hackers and unauthorized accesses.
- Private clouds. Private clouds are hosted by or for a single organization and are not shared with others. Cloud security in private clouds enables organizations to have more control over their data and resources while still being able to tap into the scalability and other benefits of the cloud.
- Hybrid clouds include a mix of public and private clouds. Cloud security in hybrid clouds involves securing data and apps running in the cloud as well as on-premises and other cloud environments. It also requires uniform security options, policies and practices for protection across various cloud providers.
As a result, cloud security mechanisms take two forms: those supplied by CSPs and those enforced by customers. It is important to note that the handling of security is rarely the complete responsibility of the CSP or the customer. It is usually a joint effort using a shared responsibility model.
The shared responsibility model
Although not standardized, the shared responsibility model is a framework that outlines which security tasks are the obligation of the CSP and which are the duty of the customer. Enterprises using cloud services must be clear about which security responsibilities they hand off to their provider(s) and which they need to handle in-house to ensure they have no gaps in coverage.
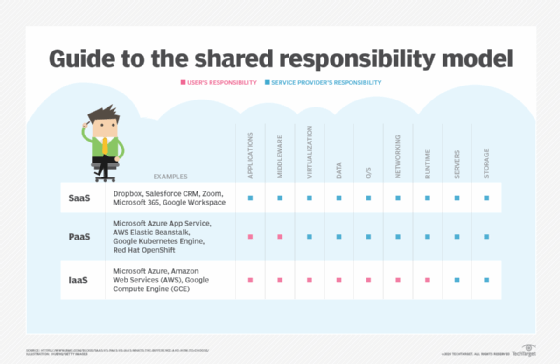
The shared responsibility model outlines the security responsibilities of the CSP and the customer.
The workload responsibilities vary depending on whether the workload is hosted on a software-as-a-service, PaaS, IaaS, or in an on-premises data center. In an on-premises data center, the customer owns the whole stack and is responsible for the entire security infrastructure. Customer responsibility commonly increases from software as a service to PaaS to IaaS. However, customers should always check with their CSPs to understand what the provider covers and what they need to do to protect the organization.
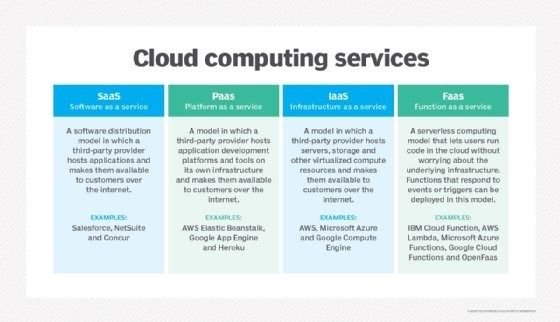
A basic comparison of SaaS, IaaS, and PaaS cloud service models.
CSP security responsibilities
Security controls supplied by CSPs vary by service model, be it software as a service, PaaS, or IaaS.
Here are some important points to consider when it comes to the security responsibilities of CSPs in the different service models:
- In general, CSPs are always responsible for servers and storage. They secure and patch the infrastructure itself, as well as configure the physical data centers, networks and other hardware that power the infrastructure, including virtual machines (VMs) and disks. These are usually the sole responsibilities of CSPs in IaaS environments.
- In a PaaS environment, CSPs assume more responsibility, including securing runtime, networking, operating systems (OSes), data and virtualization.
- In a software-as-a-service environment, CSPs also provide application and middleware security.
- The details of security responsibilities can vary by provider and customer. For example, CSPs with software-as-a-service offerings might or might not offer customers visibility into the security tools they use. IaaS providers, on the other hand, usually offer built-in security mechanisms that enable customers to access and view CSP security tools, which might also provide customer-alerting functionality.
Customer security responsibilities
Here are some important points to consider in terms of customer responsibilities for cloud security:
- To supplement the CSP security controls, customers are generally responsible for application, middleware, virtualization, data, OS, network and runtime security in IaaS clouds.
- In IaaS architectures, such as Amazon Virtual Private Cloud (VPC) or Microsoft Azure Virtual Network (VNet), for example, customers can supplement, replace or overlay built-in cybersecurity mechanisms with their own set of tools.
- In PaaS environments, customers take on fewer security tasks, generally only application and middleware security. Software-as-a-service environments involve even less customer responsibility.
- Data security and identity and access management (IAM) are always the responsibility of the customer, however, regardless of cloud delivery model. Encryption and compliance are also the responsibility of the customer.
- Because CSPs control and manage the infrastructure customer apps and data operate within, adopting additional controls to further mitigate risk can be challenging. IT security staff should get involved as early as possible when evaluating CSPs and cloud services. Security teams must evaluate the CSP's default security tools to determine whether additional measures will need to be applied in-house.
- Adding a company's own security tools to cloud environments is typically done by installing one or more network-based virtual security appliances. Customer-added tool sets enable security administrators to get granular with specific security configurations and policy settings.
- Many enterprises also often find it cost-effective to use the same tools in their public clouds as they have within their corporate local area networks (LANs). This prevents administrators from having to recreate security policies in the cloud using disparate security tools. Instead, a single security policy can be created once and then pushed out to identical security tools, regardless of whether they are on-premises or in the cloud.
Cloud security tools
Many of the same tools used in on-premises environments should be used in the cloud, although cloud-specific versions of them may exist. These tools and mechanisms include encryption, IAM and single sign-on (SSO), DLP, intrusion prevention systems and intrusion detection systems, and public key infrastructure (PKI).
Some cloud-specific tools include the following:
- Cloud workload protection platforms. A CWPP is a security mechanism designed to protect workloads -- for example, VMs, applications, or data -- in a consistent manner.
- Cloud access security brokers. A CASB is a tool or service that sits between cloud customers and cloud services to enforce security policies and, as a gatekeeper, add a layer of security.
- Cloud security posture management. CSPM is a group of security products and services that monitor cloud security and compliance issues and aim to combat cloud misconfigurations, among other features.
Types of cloud security
Cloud security encompasses various measures taken to protect data, infrastructure, applications and the integrity of cloud environments.
Security as a service is a subset of software as a service. The Cloud Security Alliance (CSA) defined the following security-as-a-service categories:
- IAM.
- DLP.
- Web security.
- Email security.
- Security assessments.
- Intrusion management.
- Security information and event management (SIEM).
- Encryption.
- BC/disaster recovery (BCDR).
- Network security.
- Continuous monitoring.
- Penetration testing.
- Vulnerability scanning.
These include services such as firewall as a service, cloud-based virtual private networks (VPNs) and key management as a service (KMaaS). Secure Access Service Edge (SASE) and zero-trust network access (ZTNA) are also emerging as two popular cloud security models.
How to secure data in the cloud
The steps required to secure data in the cloud vary. Factors, including the type and sensitivity of the data to be protected, cloud architecture, accessibility of built-in and third-party tools and number and types of users authorized to access the data must be considered.
Some general best practices to secure business data in the cloud include the following:
- Encryption. End-to-end encryption (E2EE) is the best form of defense against security threats to the cloud. Organizations should encrypt data at rest, in use and in motion. Encrypting data before uploading it to the cloud is an excellent precaution against potential hacking threats. This additional layer of security, known as zero-knowledge proof in cryptography, can protect data even from service providers and administrators. Encryption techniques, such as Secure Sockets Layer (SSL) and Transport Layer Security (TLS) for data in transit and encryption algorithms for data at rest should be considered. Additionally, organizations should consider using encryption keys managed for added control. It's essential to maintain secure storage and backup of encryption keys, ideally avoiding storing them in the cloud and regularly rotating them to prevent unauthorized access.
- Multifactor authentication and two-factor authentication. Companies should enforce the use of 2FA or MFA to verify user identity before granting access to cloud data.
- Configuration of cloud data. Configuration is an important aspect of cloud security as many breaches in cloud data stem from basic misconfiguration errors. To avoid misconfiguration errors, leaving default settings unchanged should be avoided as it gives hackers the ability to intrude into the cloud data. For example, users should never leave a cloud bucket, such as an Amazon S3 bucket open after using it.
- Cloud edge security. Adopting cloud edge security and endpoint protections, including firewalls, intrusion prevention systems and antimalware is crucial for enhancing cloud security. These protections help defend against external threats and unauthorized access, ensuring the integrity and confidentiality of data stored in the cloud.
- Regular security testing. Regular testing is essential to ensure that the cloud defense systems are operating efficiently. Many companies hire external teams of ethical hackers to test the security of their systems to confirm that their data is secure from potential threats.
- Isolating cloud data backups. Cloud data backups should be isolated to prevent ransomware threats. This is because ransomware attacks generally target backup files along with primary files to maximize their efficacy. Also, isolating backup data ensures that even if primary data is compromised by ransomware, unaffected backup copies remain intact and accessible.
- Data location visibility. Organizations should ensure data location visibility and control to identify where data resides and apply restrictions on whether data can be copied to other locations inside or outside the cloud. This not only prevents unauthorized access but also ensures compliance with data protection regulations.
- Monitoring. Companies should log and monitor all aspects of data access, system events, additions and changes. They should utilize cloud-native monitoring tools or explore third-party options to detect anomalies and unauthorized access attempts efficiently.
- Choosing a secure cloud vendor. Selecting a reliable and secure cloud provider is crucial. It's essential to choose a cloud provider carefully, considering factors such as industry, company size, business needs and local data privacy laws. This decision should not be taken lightly as it can significantly affect the security of the data stored in the cloud.
- Security awareness training. Organizations must offer security awareness training to employees, educating them on common security threats, best practices and their responsibility in upholding cloud security. This training should cover identifying phishing attempts and reporting security incidents. Also, specific roles, such as DevOps engineers and developers, who frequently handle cloud data, should receive additional training on secure development practices in cloud environments.
- Using emerging security tools. Emerging cybersecurity tools should also be considered to help secure data in the cloud. These include network detection and response and AI for IT operations. Both tools collect cloud infrastructure health and cybersecurity information. AI then analyzes data and alerts administrators of abnormal behavior that could indicate a threat.
Top cloud security challenges
Many of the traditional cybersecurity challenges also exist in the cloud. These can include the following:
- Insider threats.
- Data loss.
- Data breaches.
- IAM.
- Key management;
- Access control.
- Phishing.
- Malware.
- Shadow IT.
- DDoS.
- Insecure application programming interfaces (APIs).
As for cloud security challenges specifically, administrators have to deal with issues that include the following:
- Cloud account hijacking.
- Lack of cloud visibility and control.
- Working with cloud security tools that in-house administrators might be unfamiliar with.
- Tracking and monitoring where data is located both in transit and at rest.
- Misconfigurations.
- Weak cloud control plane.
- Challenges to understanding the shared responsibility model.
- Nefarious use of cloud services.
- Skill shortages and staffing issues.
- Multi-tenancy concerns.
- Incompatibilities with on-premises environments.
- Cloud compliance.
- Cloud governance.
- AI-driven attacks.
- Complex access control lists in multi-cloud environments.
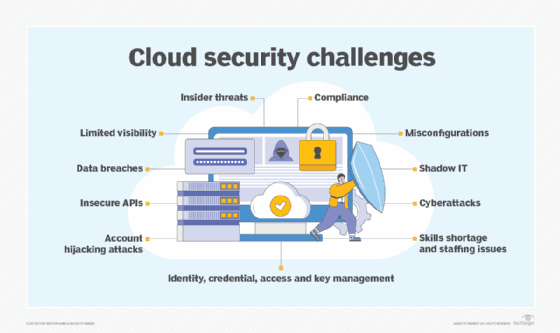
Top cloud security challenges faced by organizations.
Security administrators must have plans and processes in place to identify and curb emerging cloud security threats. These threats typically revolve around newly discovered exploits found in applications, OSes, VM environments and other network infrastructure components. To handle these security challenges and eliminate emerging threats, organizations must quickly and properly update and patch the software that they control.
It's also important to establish communication channels between in-house IT and CSP staff. In-house staff should subscribe to, monitor and digest the CSP's security bulletin stream. If coordination between the customer and CSP is required to handle a security incident, well-documented communication channels must be established and continuously updated so time isn't wasted when working through a security breach.
Cloud security best practices
There are separate security-as-a-service best practices, PaaS best practices and IaaS best practices. Organizations should also adhere to a number of general cloud security best practices, including the following:
- Understand the shared responsibility model. Organizations should understand the shared responsibility model, including the responsibilities of their CSPs and their security team. Organizations need to focus on how they connect to the cloud and control data and access.
- Choose the CSPs wisely. Businesses should know what security controls the cloud vendors offer and review contracts and service-level agreements diligently.
- Adopt an IAM policy. It's important to adopt a strong, granular IAM policy to control who has access to what. The principle of least privilege, also referred to as POLP; strong passwords; 2FA or MFA should also be enforced.
- Enforce encryption. Data should always be encrypted, whether it's at rest, in use or in motion.
- Conduct continuous monitoring. Companies should maintain cloud visibility through continuous monitoring. Regular monitoring helps with staying on top of security-related feature updates from their cloud providers and also helps with establishing incident response practices.
- Establish and enforce cloud security policies . A cloud security policy outlines the guidelines, procedures and controls that govern the security of data, applications and infrastructure in cloud environments. It helps ensure that security measures are consistently applied across the organization's cloud deployments and align with regulatory requirements and industry best practices.
- Provide security training. Companies should conduct security awareness training for employees, third-party partners and anyone accessing organizational cloud resources.
- Perform cloud segmenting. Cloud segmentation involves dividing cloud environments into unique segments or zones based on factors such as access requirements, data sensitivity and security controls. Segmenting cloud resources enables organizations to set up granular access controls, ensuring that users and apps only have access to the resources they require.
- Consult the Cybersecurity Security Information Sheets. The Cybersecurity and Infrastructure Security Agency (CISA) and the National Security Agency (NSA) have released joint Cybersecurity Information Sheets (CSIs) to provide organizations with recommended best practices and mitigations to improve the security of their cloud environment. Organizations should look into these to execute best practices for cloud security.
Difference between cloud security vs. cyber security
Cloud security and cybersecurity are related concepts but have different scopes and focuses:
Cloud security specifically deals with protecting data, applications, programs and infrastructure hosted in cloud environments. It encompasses measures and controls deployed to secure cloud-based resources, including data centers, servers, networks and VMs. Cloud security addresses unique challenges such as shared responsibility models, multi-tenancy, data privacy and compliance requirements in cloud computing environments. The primary concern of cloud security is data privacy and protection during data transfer.
Cybersecurity, on the other hand, is a broader discipline that encompasses the protection of computer systems, networks, devices and data from cyber attacks. It includes securing both cloud-based and on-premises IT environments against a wide range of cyber threats, including malware, ransomware, phishing attacks, data breaches and insider threats. Cybersecurity focuses on safeguarding digital assets and information from unauthorized access, manipulation, or theft, regardless of where they are stored or accessed. Cybersecurity primarily deals with keeping information secure at rest.
Future of cloud security
Cloud security is a rapidly evolving field with several emerging trends and technologies shaping its future. Per IBM's Cost of Data Breach 2023 report, 45% of breaches occur within cloud-based systems, with 82% of breaches involving data stored in the cloud. Given the notable surge in cloud-based attacks, it is imperative for companies embracing cloud technology to prioritize robust security measures.
The following are some emerging trends shaping the future of cloud security:
- Serverless computing. Serverless computing is quickly becoming a cornerstone of cloud strategy as it enables businesses to run applications and services without having to manage the underlying server infrastructure. It offers numerous benefits for cloud security by reducing the attack surface, automating security updates, providing isolation and sandboxing, enabling scalable security controls, offering built-in security features and promoting security as code (SaC) practices. As organizations increasingly adopt serverless architectures, they are likely to rely on these capabilities to enhance the security posture of their cloud-based applications and services.
- Integration of large language models. Cloud services are increasingly integrating LLMs. By automating threat detection and response through ML and natural language understanding, LLMs transform cloud security. Their ongoing adaptation to changing threats offers real-time information for prompt incident handling. LLMs also serve as proactive sentinels against social engineering threats, simplify compliance management by understanding regulatory texts and assist with incident response communication to lessen the damage security breaches do to a company's reputation.
- Adoption of zero trust. Zero trust concepts are expected to significantly shape cloud environments. With zero trust, access to resources, data and permissions are not automatically granted based on user identity or network location. Instead, every access request is rigorously authenticated, authorized and continuously monitored, regardless of whether it originates from inside or outside the network perimeter. By adopting zero-trust policies, organizations can minimize the risk of lateral movement attacks and reduce the effects of potential breaches. In the context of cloud network security, zero-trust models are expected to become increasingly prevalent as organizations adopt cloud-based architectures and distributed workforces.
- AI- based threat detection. Conventional security measures might not be adequate as cyberthreats change over time. By examining large data sets to find anomalies and possible breaches, threat detection driven by AI is becoming the new norm. It's a notable development in cloud security due to its proactive protection against new threats, which enables enterprises to recognize and eliminate threats before they can negatively affect the cloud infrastructure.
Many organizations face a shortage of in-house cloud security expertise and resources required to adequately protect cloud assets during their transition to hybrid and multi-cloud infrastructures. Learn the benefits of outsourcing cloud security and explore the pros and cons of managed cloud security services.
This was last updated in June 2024
Continue Reading About cloud security
- Private vs. public cloud security: Benefits and drawbacks
- Hybrid cloud security challenges and how to manage them
- Multi-cloud identity management tips and best practices
- Security Think Tank: Going beyond IAM for cloud security
- Assess security posture with the Cloud Security Maturity Model
 The cloud shared responsibility model for IaaS, PaaS and SaaS
The cloud shared responsibility model for IaaS, PaaS and SaaS  By: Chris Tozzi
By: Chris Tozzi  Cloud licensing explained: What businesses need to know
Cloud licensing explained: What businesses need to know  By: Andy Patrizio
By: Andy Patrizio  By: Jill McKeon
By: Jill McKeon  What is cloud scalability?
What is cloud scalability?  By: Michael Nadeau
By: Michael Nadeau