brute-force attack (original) (raw)
What is a brute-force attack?
A brute-force attack is a trial-and-error method used by application programs to decode login information and encryption keys to use them to gain unauthorized access to systems. Using brute force is an exhaustive effort rather than employing intellectual strategies.
Just as a criminal might break into and crack a safe by trying many possible combinations, a brute-force attack of applications tries all possible combinations of legal characters in a sequence. Cybercriminals typically use a brute-force attack to obtain access to a website, account or network. They may then install malware, shut down web applications or conduct data breaches.
A simple brute-force attack commonly uses automated tools to guess all possible passwords until the correct input is identified. This is an old but still effective attack method for cracking common passwords.
How long a brute-force attack lasts can vary. Brute-forcing can break weak passwords in a matter of seconds. Strong passwords can typically take hours or days.
Organizations can use complex password combinations to extend the attack time, buying time to respond to and thwart the cyber attack.
What are the different types of brute-force attacks?
Different types of brute-force attacks exist, such as the following:
- Credential stuffing occurs after a user account has been compromised and the attacker tries the username and password combination across multiple systems.
- A reverse brute-force attack begins with the attacker using a common password -- or already knowing a password -- against multiple usernames or encrypted files to gain network and data access. The hacker will then follow the same algorithm as a typical brute-force attack to find the correct username.
- A dictionary attack is another type of brute-force attack, where all words in a dictionary are tested to find a password. Attackers can augment words with numbers, characters and more to crack longer passwords.
Additional forms of brute-force attacks might try and use the most commonly used passwords, such as "password," "12345678" -- or any numerical sequence like this -- and "qwerty," before trying other passwords.
What is the best way to protect against brute-force attacks?
Organizations can strengthen cybersecurity against brute-force attacks by using a combination strategies, including the following:
- Increasing password complexity. This extends the time required to decrypt a password. Implement password manager rules, like minimum passphrase length, compulsory use of special characters, etc.
- Limiting failed login attempts. Protect systems and networks by implementing rules that lock a user out for a specified amount of time after repeat login attempts.
- Encrypting and hashing. 256-bit encryption and password hashes exponentially increase the time and computing power required for a brute-force attack. In password hashing, strings are stored in a separate database and hashed so the same password combinations have a different hash value.
- Implementing CAPTCHAs . These prevent the use of brute-force attacking tools, like John the Ripper, while still keeping networks, systems and websites accessible for humans.
- Enacting two-factor authentication . This is a type of multifactor authentication that adds an additional layer of login security by requiring two forms of authentication -- as an example, to sign in to a new Apple device, users need to put in their Apple ID along with a six-digit code that is displayed on another one of their devices previously marked as trusted.
A good way to secure against brute-force attacks is to use all or a combination of the above strategies.
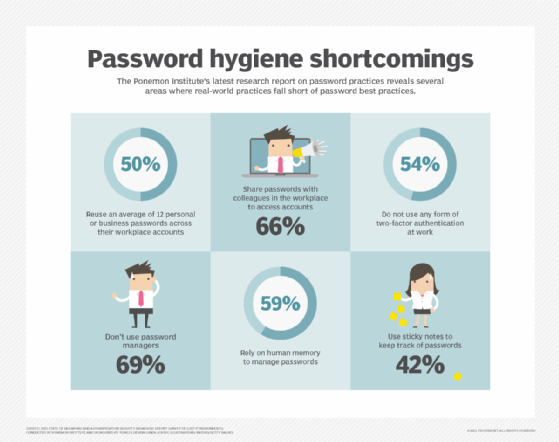
Ponemon Institute's research on the state of password practices
How can brute-force attack tools improve cybersecurity?
Brute-force attack tools are sometimes used to test network security. Some common ones are the following:
- Aircrack-ng can be used to test Windows, iOS, Linux and Android. It uses a collection of widely used passwords to attack wireless networks.
- Hashcat can be used to strength test Windows, Linux and iOS from brute-force and rule-based attacks.
- L0phtCrack is used to test Windows system vulnerabilities against rainbow table attacks. No longer supported, new owners -- as of summer 2021 -- are exploring open sourcing, among other unnamed options for the software.
- John the Ripper is a free, open source tool for implementing brute-force and dictionary attacks. It is often used by organizations to detect weak passwords and improve network security.
 IT can use the wireless network auditing tool Aircrack-ng to test password security.
IT can use the wireless network auditing tool Aircrack-ng to test password security.
What are examples of brute-force attacks?
- In 2009, Attackers targeted Yahoo accounts using automated password cracking scripts on a Yahoo web services-based authentication application thought to be used by internet service providers and third-party web applications.
- In 2015, threat actors breached nearly 20,000 accounts by making millions of automated brute-force attempts to access Dunkin's mobile app rewards program for DD Perks.
- In 2017, cybersecurity criminals used brute-force attacks to access the U.K. and Scottish Parliament internal networks.
- In 2018, brute-force attackers cracked passwords and sensitive information of millions of Cathay Pacific airline passengers.
- In 2018, it became known that a Firefox bug exposed the browser's master password to brute-force attacks against insufficient Secure Hash Algorithm 1 hashing left unfixed for almost nine years.
- In 2021, the National Security Agency warned of brute-force password attacks being launched from a specially crafted Kubernetes cluster by a unit within Russia's foreign intelligence agency.
- In 2021, hackers gained access to T-Mobile testing environments and then used brute-force attacks and other means to hack into other IT servers, including those that contained customer data.
This was last updated in September 2021
Continue Reading About brute-force attack
- How to use hashcat to address authentication vulnerabilities
- What is a password spraying attack and how does it work?
- The top 6 SSH risks and how regular assessments cut danger
- Create and enforce a password policy across the enterprise
 dictionary attack
dictionary attack  By: Gavin Wright
By: Gavin Wright  How to use the John the Ripper password cracker
How to use the John the Ripper password cracker  By: Ed Moyle
By: Ed Moyle  reverse brute-force attack
reverse brute-force attack  By: Alexander Gillis
By: Alexander Gillis  rainbow table
rainbow table